Security Advisory – Tecnimont Cyber Theft

Tecnimont Cyber Theft – Security Advisory
Background:
Maire Tecnimont SpA is the parent company of the Italian group Maire Tecnimont, which consists of at least 50 operating companies in the engineering and main contracting sector. It deals in oil and gas, chemicals and petrochemicals, energy, infrastructure and civil engineering.
This document is about a security incident of Tecnimont Cyber Theft wherein a Chinese group swindled US$18.5m from an Indian arm of Italian firm on 10 January 2019.
Financial Loss:
USD $18.6 million / INR 130 Crore
How it Happened?
Type of Attacks Involved:
- Phishing
- Cyber Theft
- Identity Theft
- Social Engineering
- Malware Attack
Prime Target:
Indian head of Tecnimont SpA
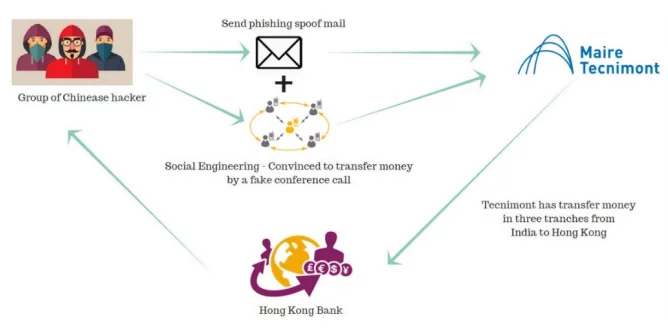
Attack Scenario:
- The Chinese attackers sent emails to the head of Tecnimont Pvt. Ltd., the Indian subsidiary of Milan-headquartered Tecnimont SpA, through an email account that looked deceptively similar to that of group CEO.
- The email’s wording imitated the writing style of the group chairman. Other communications that purported to come from various executives were similar in nature as the hackers might have managed to penetrate the IT system and study their emails.
- The hackers then arranged a series of conference calls to discuss a possible “secretive” and “highly confidential” acquisition in China. Several people played various roles during these calls, pretending to be the group CEO, a top Switzerland-based lawyer and other senior executives of the company. § The attackers have convinced India CEO to send money for a secret acquisition happening in china.
- The hackers convinced that the money couldn’t be transferred from Italy due to regulatory issues.
- After that the CEO has transferred the amount in three tranches during one week in November. The money that was transferred — $5.6 million, $9.4 million and $3.6 million — from India to the banks in Hong Kong was withdrawn within minutes. The fraudsters tried for a fourth transfer, but by then the fraud had been discovered.
Observations:
- Attackers masked their Email addresses.
- Email harvesting done to identify emails of executive officers.
- Used similar domains which made the phishing emails seem legitimate. § All people in conference call had fraudulent ID’s.
- The bank account which they have used to transfer the amounts were opened using fake documents confirmed by the investigators.
- The publication reported citing internal examinations that all those on conference calls had sham identities and the top Swiss lawyer who went by the name of Luigi Corradi doesn’t exist. The bank accounts into which the money was sent were opened using bogus documents.
- The attack was carried out using Social Engineering + Phishing Emails Attack.
Recommendations:
With respective to this attack below are the recommendations that need to follow:
- Do not respond to unknown and/or suspicious emails
- Conduct phishing diagnostic (red team attack) & social engineering attack to identify overall organization’s security posture
- User security awareness training is required
- Periodically update the security patches and antivirus signatures
- Continuous security monitoring of critical network with securely configured solutions
- Use two factor authentications to authenticate into the emails and critical application as well as systems account.
- Secure network architecture deployment across main office to plants.
Author,
Jinto T.K.
SOC Team
Varutra Consulting Pvt. Ltd