Threat Modelling – Focused Defence for Modern Enterprises
Threat modeling is creating a buzz that everyone wants to talk about it. Every organization wants to remodel its overhaul information. It will help them in producing a priority list for security improvements for their requirements, concepts, design, and implementation.
Overview of Threat Modelling
Hackers are constantly looking for any type of exposure to attack organizations. If the attempts are successful, then the organization’s sensitive data are at risk. They can even prevent the systems and servers from properly functioning. As technology is growing, the threats are also evolving.
What is this Threat Modelling everyone is talking about?
Threat modeling is a means to identify, communicate, and understand threats. It includes architectural vulnerabilities, lack of appropriate safeguards, and mitigations. It helps create proper documentation with profiling on hackers and other attack vectors that will assist system analysts and defenders with better understanding and increase efficiency.
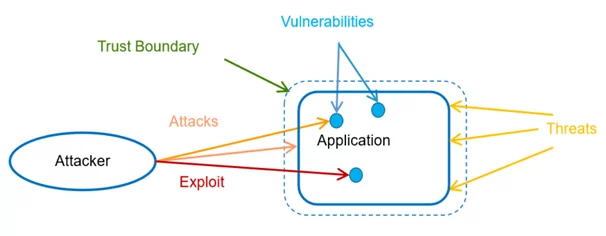 Fig: 1.0 Threat Scenario
Fig: 1.0 Threat Scenario
Implementation of threat modeling is possible in a variety of things like software applications, systems, networks, IoT, distributed systems, business processes, and much more. Though this procedure can be carried out at any development stage it is preferred to be done early at the design time.
Process of Creating a Threat Model
The procedure of threat modeling begins with the designing of a visual representation of an application or system analysis. There are two means of creating a visual representation.
- Visual Representation by Data Flow Diagram (DFD)
DFDs are the tools that provide a high-level visualization of the application that works within the system to store, move or manipulate the data by system engineers. It has three core steps:
- View System as an adversary
- Characterize the system
- Determine the threats
The threats determined by the DFD method are limited. So, it is considered to be a poor starting point for modeling and it is imprinted as a weakness. Some of them are listed below:
- They don’t talk about the structure and stream of use.
- Their main focus is how information is being streamlined rather than client connectivity to the framework.
Risk displays that are DFD-based do not have a standard methodology. It results in various individuals creating threat models with multiple outputs for a similar situation.
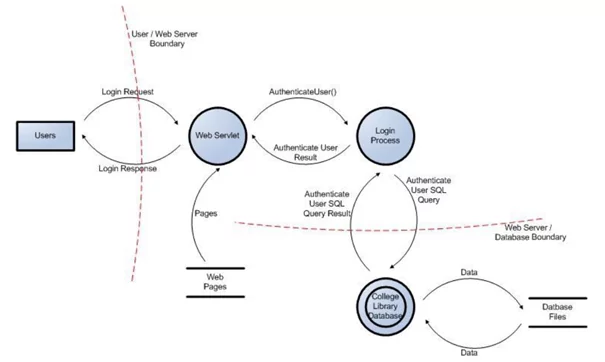
Fig: 1.1 DFD of an online college application
- Visual Representation by Process Flow Diagram (PFD)
They are the tools that permit software developers to create threat models based on the application design process. It provides a visual representation specially designed for depicting a hacker’s thought process. Attackers do not analyze the data flow, but they may draw a roadmap on proceeding through different applications. PFD follows three core steps:
- Display of the application’s used cases.
- Communication protocols are properly segregated. It helps the individual in moving between the used cases.
- Use cases are formed by collaborating various technical controls like cookies, sessions, forms, and other coding elements.
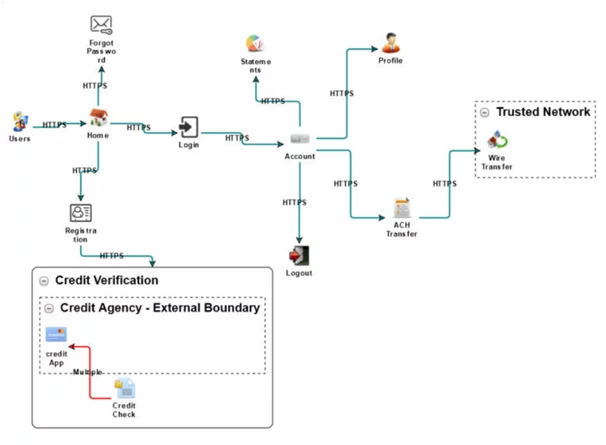
Fig: 1.2 PFD of an online banking application
Threat Modelling Methodologies
The methodology is required to model the threats independently of the attacker-centric, asset-centric, and software-centric. Here are the top three methods from which organizations can choose depending upon their project needs.
1.STRIDE Methodology
It is one of the primitive threat-modeling methods to be used. It was designed by Microsoft. It delivers an imprint for the basic set of threats that are categorized into six categories. They are:
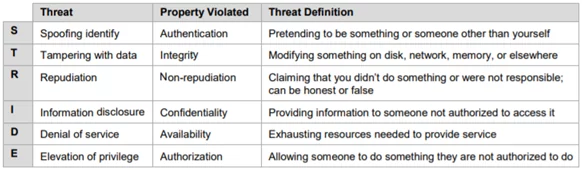
Fig: 1.3 STRIDE Threat Categories
STRIDE performs system detail design evaluation. This procedure is carried by creating DFDs (Data Flow Diagram). It then identifies the system entities, events, and system boundaries. It is an easy to adopt method but is time-consuming. There is an issue of a rapid increase in threats as the system complexity increases.
2. P.A.S.T.A. Methodology
P.A.S.T.A. was designed in 2012, which is a risk-centric threat modeling framework. It is the abbreviation for Process for Attack Simulation and Threat Analysis. It is divided into seven categories. Each category is designed for multiple activities. They are:

Fig: 1.4 PASTA Threat Categories
he main function of P.A.S.T.A. is to bring technical prerequisites and business destinations together. Multiple plans and tools are used in different stages. Using this strategy, the threat modeling cycle is divided into many vital levels i.e., administration engineering, key decision-makers, acquiring security contribution from tasks, and improvement. P.A.S.T.A. is generally viewed as a risk-driven structure, and it utilizes viewpoint driven by an attacker to create an asset-driven output for threat scoring and identification.
3. LINDDUN
Its full form is Linkability, identifiability, nonrepudiation, detectability, disclosure of information, unawareness, noncompliance. It focuses on the user’s privacy and data security. It consists of six core steps and provides a seamless approach towards privacy settlement.
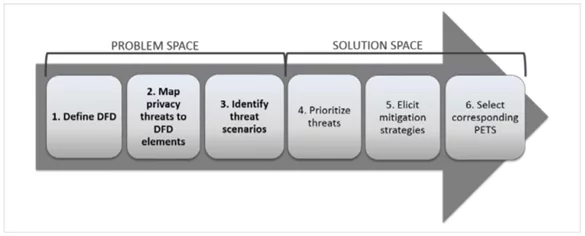
Fig: 1.5 LINDDUN Methodology Steps
The LINDDUN process begins with a DND of the system where it explains the system’s information flow, data storage, external entities, and procedures. LINDDUN users can easily distinguish threat appropriateness in the framework and then build threat trees by deliberately repeating every model component and breaking them down from their respective threat classifications.
Conclusion
Threat modeling makes your item more reliable and secure. It displays significant risk demonstration techniques and procedures. They can be used for individual purposes as well as for others. There are instances where multiple strategies are combined. To perform threat modeling, you need to be clear about your target (risk, security, and privacy), to what extent you need to carry out this process, your experience with it, how deeply your partners are to be included in the spry environment, contingent time for running and how frequently the modeling is rehashed.
We offer several cybersecurity services to counter these cyber-attacks and risks. Services like Audit and Compliance, SOC and Global Threat Management Services, Information Security Maturity Assessment, Special Security Services, and much more. Our tailored security services will help organizations secure their information and enhance their defensive security systems.
References:
- https://www.cs.montana.edu/courses/csci476/topics/threat_modeling.pdf
- https://resources.sei.cmu.edu/asset_files/WhitePaper/2018_019_001_524597.pdf
- https://threatmodeler.com/wp-content/uploads/2017/08/Online-Banking-Application-Threat-Model-v2-e1523416136759.jpg
Author,
Sankalp Mahajan
Attack & Pen Test Team
Varutra Consulting Pvt. Ltd.




