Essentials of Third Party Risk Management (TPRM)
Risk management is the process of carrying out evaluative decisions based on analytics and calculations that will ensure to mitigate the adverse effects of risk on a certain business unit. The adverse effects of risk can vary from an objective perspective or quantifiable like insurance premiums and claims costs, or subjective perspective and difficult to quantify such as damage to reputation or decreased productivity.
The extent of risk can be mathematically expressed as follows:
Risk = Probability x Severity
Probability is the likelihood of an event getting triggered, and severity is the extent and cost that occurred to an organization of the resulting loss.
What is Third-Party Risk Management (TPRM) ?
A “Third-party” is an entity or organization or business process with which may you have an agreement to deliver a product or service to either you or your clientele on behalf of your company. A third party is also termed and identified as a supplier, service provider, or vendor from a broader perspective.
Therefore, Third Party Risk Management is an assessment of vendor risk presented by an organization’s third-party relationships along the whole supply chain in the industry market. TPRM involves all about the process of identifying, evaluating, and monitoring the risks which are depicted throughout the lifecycle of your relationships and engagements with the third parties and further taking steps to ensure that these risks are mitigated or reduced to a certain acceptable level. This often initiates during procurement or onboarding and reaches the end of the offboarding process.
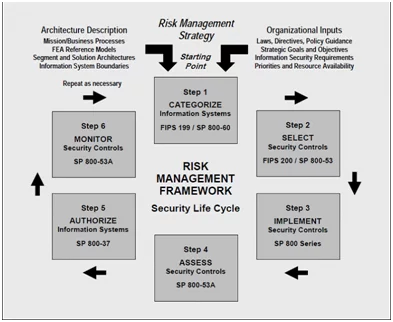
SOURCE - https://sites.google.com/site/itec5321fall09/nist-800-53
Essentials of Third Party Risk Management (TPRM) Program
1. To have A standardized, uniform onboarding process.
From the initial vendor request for the engagement relationships and prescreening of the vendor to collecting required documentation for verification, following a standard onboarding process will ensure that you are not missing any critical requirements that may further affect any internal process, and that you and your vendor are prepared to start doing business together herewith.
As part of your onboarding and partnering with the Vendor, to kick off with is to create a central repository of vendors, this should be lesser paper and document-based but should be automated so you can see – review, at any time, where a vendor is in the onboarding process during the entire course of time.
2. Create a Risk-Based Vendor Profile.
Creating a risk-oriented and risk-centric profile for each vendor associated with you will not only help you define your approach and relationship with the vendor but will also help you evaluate the products/services they will provide—and how essential or mission-critical they and their services are to your business organization. It will also assist you to further identify and define what type of physical, systems, servers, and data access has been given and provided to the vendor.
Categorization of vendors through risk profiling makes vetting your vendors more consistent in aspects of service being provided or delivery of certain commitments and creates a better understanding of your vendor arena.
3. Use risk & controls assessments.
Once the risk associated with a vendor is highlighted and evaluated, further you will need to check that are the proper controls in place to ensure that risk is managed and that they are operating effectively and a reconciliation or a monitoring mechanism is present to monitor the risk areas periodically. Those controls can be part of a larger security framework or roadmap of the organization. This can be achieved with reference to certain security compliance frameworks like NIST, FEDRamp, ISO, and many others.
4. Have a remediation management plan.
It is very common to discover an issue when onboarding vendors with the organization, so having a planned and distributed approach to address and remediate and monitor the issues quickly to keep the onboarding process going is critical. With TPRM, there are four steps to the remediation management process in any project.
- Record the activity blocker.
- Record and identify the action items to identify and decide on follow-up measures.
- Send consecutive action reminders to stakeholders that need to respond.
- Remediate and retest the issue.
You can always make things easier by using a rules-based approach to ensure issues are not closed before all the action items are completed, creating a Ticket based system is a good approach to implement and follow.
5. Periodic review of service level contracts.
As the issues are remediated, the next step is to consider and further determine that how well your vendors are performing against their service level agreements and contracts with you. Because poorly managed contracts are a source of both increased risk which may also further reflect in terms of revenue loss.
If your TPRM program is at a maturity level where performance management indicator matters the most to the organization, the factor to be monitored is KPI, i.e., the Key Performance Indicators.
6. Mandate ongoing vendor monitoring.
It is not just the SLA that will require a periodic review or check-in. That supplier you vetted a year ago could put you in danger of a compliance violation or privacy norms violation or disrupt your supply chain today if not monitored properly. Ongoing monitoring can be accomplished in several ways, but some common methods include but not limited to as stated below:
- Automating the scheduling of follow-up assessments based on the risk level of a vendor by profiling it duly based on a calendar.
- Using automation to trigger assessments directly when thresholds are reached, or related significant events are discovered.
- Integrating third-party intelligence feeds on a periodic basis that provides ongoing monitoring alerts for significant changes to a vendor’s risk ratings.
7. Set a vendor offboarding process.
You may end a relationship or engagement with a vendor for several reasons based on a number of scenarios, but it is not as simple that just stopping your orders and ending your business. You will need an apre-ready offboarding strategy and plan that includes finalizing payments, disabling vendor access to the organization’s crucial data, and many more like it.
How we can help
Varutra’s Audit and Compliance service help to minimize your organization’s exposure to risks associated with outsourcing or working with third parties by designing end-to-end third party risk management programs, systems, and technologies everything you need to manage these risks.
Author,
Omkar Gaikwad
Audit and Compliance Department
Varutra Consulting Pvt. Ltd.