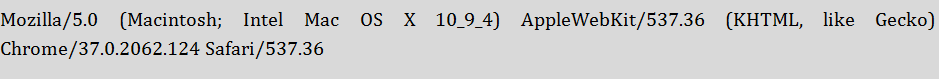Shellshock-Security Patching Aftermath
On September 24th 2014, a publicly disclosed vulnerability was revealed in the UNIX/Linux which we have discussed in our blog https://www.varutra.com/blog/?p=1010. Although a patch has been released for this vunerability by vendors such as ubuntu,redhat and centos etc. but the patch was not successful, Additional vulnerability in the same area were discovered which left Bash again more vulnerable to severe attack such as arbitrary remote code execution. The set of vulnerability collectively known as shell shock are serious issue in many organizations. The CVE number that are part of this are CVE 2014-6271, CVE 2014-7169, CVE 2014-7186, CVE 2014-7187, CVE 2014-6277 and CVE 2014-6278.
In response to shellshock, Richard Stallman (software freedom activist and computer programmer) said the bug was just a “blip”. It’s not, it’s a “blimp” — a huge nasty spot on the radar warning of big things to come. Three more related bugs have been found, and there are likely more to be found later. The cause isn’t that a programmer made a mistake, but that there is a systematic failure in the code — it’s obsolete, having been written to the standards of 1984 rather than 2014.
Detailed Explanation Shellshock – Security Patching Aftermath
The Shellshock problem is an example of an arbitrary code execution (ACE) vulnerability. Typically, ACE vulnerability attacks are executed on programs that are running, and require a highly sophisticated understanding of the internals of code execution, memory layout, and assembly language—in short, this type of attack requires an expert. Attacker will also use an ACE vulnerability to upload or run a program that gives them a simple way of controlling the targeted machine. This is often achieved by running a “shell”. A shell is a command-line where commands can be entered and executed. The Shellshock vulnerability is a major problem because it removes the need for specialized knowledge, and provides a simple (unfortunately, very simple) way of taking control of another computer (such as a web server) and making it run code. Suppose for a moment that you wanted to attack a web server and make its CD or DVD drive slide open. There’s actually a command on Linux that will do that: /bin/eject. If a web server is vulnerable to Shellshock you could attack it by adding the magic string () { :; }; to /bin/eject and then sending that string to the target computer over HTTP. Normally, the User-Agent string would identify the type of browser you are using, but, in in the case of the Shellshock vulnerability, it can be set to say anything.
Example: curl -H “User-Agent: () { :; }; /bin/eject” http://example.com/
would be enough to actually make the CD or DVD drive eject.
How does this Shellshock Attack works?
When a web server receives a request for a page there are three parts of the request that can be susceptible to the Shellshock attack: the request URL, the headers that are sent along with the URL, and what are known as “arguments” (when you enter your name and address on a web site it will typically be sent as arguments in the request).
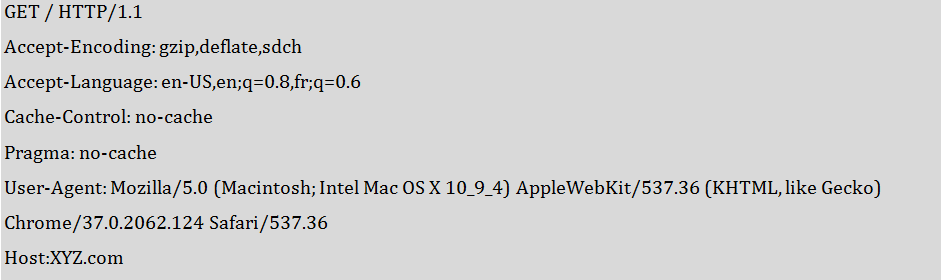
For example, here’s an actual HTTP request that retrieves the XYZ homepage:
In this case the URL is / (the main page) and the headers are Accept-Encoding, Accept-Language, etc. These headers provide the web server with information about the capabilities of my web browser, my preferred language, the web site I’m looking for, and what browser I am using.
It’s not uncommon for these to be turned into variables inside a web server so that the web server can examine them. (The web server might want to know what my preferred language is so it can decide how to respond to me).
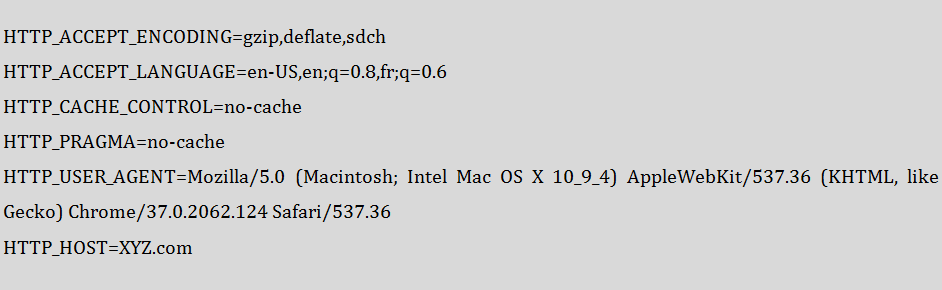
For example, inside the web server responding to the request for the XYZ home page it’s possible that the following variables are defined by copying the request headers character by character.
As long as those variables remain inside the web server software, and aren’t passed to other programs running on the web server, the server is not vulnerable.
Shellshock occurs when the variables are passed into the shell called “bash”. Bash is a common shell used on Linux systems. Web servers quite often need to run other programs to respond to a request, and it’s common that these variables are passed into bash or another shell.
The Shellshock problem specifically occurs when an attacker modifies the origin HTTP request to contain the magic () { :; }; string discussed above. Suppose the attacker change the User-Agent header above from
to simply () { :; }; /bin/eject. This creates the following variable inside a web server:
If that variable gets passed into bash by the web server, the Shellshock problem occurs. This is because bash has special rules for handling a variable starting with () { :; };. Rather than treating the variable HTTP_USER_AGENT as a sequence of characters with no special meaning, bash will interpret it as a command that needs to be executed.
The problem is that HTTP_USER_AGENT came from the User-Agent header which is something an attacker controls because it comes into the web server in an HTTP request. And that’s a recipe for disaster because an attacker can make a vulnerable server run any command it wants (see examples below).
The solution is to upgrade bash to a version that doesn’t interpret () { :; }; in a special way.
Some attacks using shellshock
The Shellshock attack takes advantage of a flaw in Bash that enables attackers to execute remote commands that would ordinarily be blocked.
Allows an attacker to execute command via user agent, referrer, and other HTTP headers. 
Figure : Working of Shellshock
The Shellshock problem is an example of an arbitrary code execution (ACE) vulnerability. A shell is a command-line where commands can be entered and executed.
- Somebody could use your server as an attack bot:
- () { :; }; ping -s 1000000 <victim IP>
- If victim.com was vulnerable then
- curl -H “User-Agent: () { :; }; /bin/eject” http://victim.com/
- Would be enough to actually make the CD or DVD drive eject.
- To extract private information, attackers are using a couple of techniques. The simplest extraction attacks are in the form:
- () {:;}; /bin/cat /etc/passwd
- DoS attack using Shellshock
- () { :;}; /bin/sleep 20| /sbin/sleep 20|/usr/bin/sleep 20
Proof of Concept for incomplete fix to shellshock
The bash fix for CVE-2014-6271 was incomplete and command injection is possible even after the patch has been applied. The issue is being tracked as CVE-2014-7169 and exists due to incorrect function parsing.
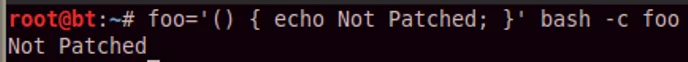
To test, execute this command from within a bash shell:
foo='() { echo not patched; }’ bash -c foo If you see “not patched“, you probably want upgrade immediately. If you see “bash: foo: command not found”, you’re OK.
Figure: Unpatched Bash
The two attacks CVE-2014-6277(Permits remote code execution and requires a high level of expertise. It has a CVSS score of 10.0) & CVE-2014-6278 (More severe as it allows remote code execution and doesn’t require a high level of expertise. It has a CVSS score of 10.0) are more severe and permit remote code execution:
These two vulnerabilities have been resolved in upstream patches Ubuntu/RHEL/Debian.
Deadening Shellshock
We strongly recommend applying the patches that were released on September 27th in order to remediate these new vulnerabilities by the following command:
APT-GET: Ubuntu / Debian
Update Bash to the latest version available via
apt-get: sudo apt-get update && sudo apt-get install –only-upgrade bash
YUM: CentOS / Red Hat / Fedora
Update Bash to the latest version available via the yum:
sudo yum update bash
For detailed explanation to mitigate the shellshock go through the links:
https://access.redhat.com/articles/1212303
http://www.bankinfosecurity.com/how-to-mitigate-shellshock-risks-a-7363/op-1
https://f5.com/solutions/mitigation/mitigating-the-bash-shellshock-cve-2014-6271-and-cve-2014-7169-vulnerabilities
http://www.akamai.com/html/security/shellshock-bash-cve-list.html
References:
http://seclists.org/oss-sec/2014/q3/650
Author(s): Lokesh Bawariya Security Consultant & Sachin Wagh Security Consultant, Varutra Consulting