MALWARE ANALYSIS – PART 2 (SETTING UP THE LAB)
In the previous blog, we have got a basic idea about Malware like what is malware, its behavior, types, and a brief introduction to Malware Analysis. In this section, we will be setting up the testing lab for dynamic and static analysis. So, let us begin with setting up the environment and labs.
Setting up Malware Analysis Lab:
To exercise the functionality of malware, we need to simulate the network services. The risk associated with this would be spamming, denial-of-service attacks. The first thing you can take into consideration is not using the main computer or host operating system. The primary functionality of the malware would be relying on the internet. So, it will check whether the host has an internet connection. The modern piece of malware comes with anti-analysis features.
Sandbox:
Sandbox environment is an isolated virtual machine that can be used to execute malicious code or malware without affecting the actual host. It decreases the risk of infecting the host OS from malware.
To carry out dynamic analysis of malware, we need a sandbox environment or any isolated operating system. Sandboxing helps us to carry out dynamic analysis and helps us to protect our system from malware.
There are few sandboxes that are freely available over the internet. Some of them are mentioned below:
- Any.run:
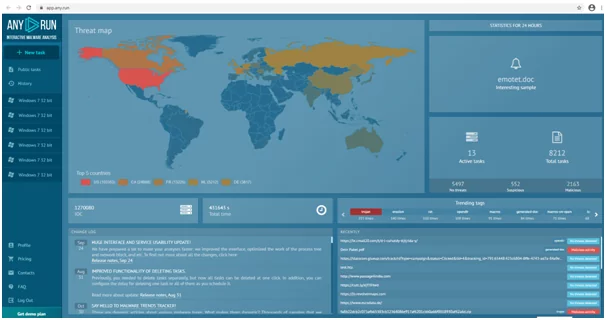
Any.run is an online sandbox used for malware analysis. Here you can execute the suspicious executable or URL, in which you can check the real-time execution and behavior of any malware or suspicious programs. You can navigate to the URL https://any.run/ and register yourself for free and get hands-on experience.
*
- VirusTotal:
Virus Total is an online service that can further analyze the files and URLs for detection of any Virus, Trojans, Worms, or any other malicious files. It is a kind of antivirus engine and scanner used to detect viruses.

These are the freely available tools over the internet which can be used for analysis. In Static Analysis, we get the basic idea of the malicious file or what kind of code/data it has.
To get a further detailed description or the behavior of the actual malicious file, we need to conduct the Dynamic Malware Analysis. For further analysis, we will need to have Virtual Environment/Sandbox.
Let us get an overview of how to set up a virtual environment. You can download any virtual OS for windows like 7, 8, 10.
The following are the prerequisites for setting up a Virtual Environment/Sandbox:
- Virtual Box/ VM Ware
- Windows Operating System
You can download OS and Virtual Box from the link provided in the description:
- https://developer.microsoft.com/en-us/microsoft-edge/tools/vms/
- https://www.virtualbox.org/wiki/Downloads
Setting Up Sandbox Environment:
Points to be taken care of before initiating the process:
- Malware nowadays is designed with an anti-malware analysis feature due to which it gets lengthy and a bit cozy for analyzing the malware
- Malware when executed, will check whether the operating system is a host or guest operating system. And will behave accordingly
- Host OS and Guest OS should be on cross-platform.
For example: Host OS can be Linux distribution or Mac OS
- The guest operating system can be Win 7 as this OS is more reliable for sandbox environments.
- There are few checks which need to implement on Virtual Environment i.e.: Internet Connection, Guest OS needs to set as Host OS in virtual box
Observing the above-mentioned points, it’s recommended to set up a virtual environment accordingly.
Let us get the actual scenario of setting up this environment:
Step 1: Import Virtual OS
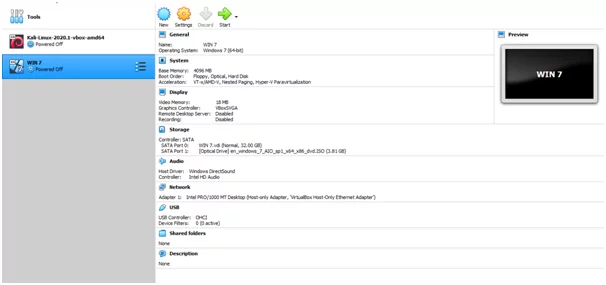
After importing any virtual OS we need to configure the virtual environment. For any malware analysis, we need to create an isolated environment. In the actual scenario, we will be executing the malicious code, as this process requires the actual isolated system. So below configurations are required to create an isolated system. While performing the analysis external drives[HDD, Pen drive]should not be attached or connected.
Step 2: Configuring the OS
- Configurations: 4 GB Ram
- Network Adapter: Set to Host-Only
- Shared Folder: Set to None
After configuring the virtual environment, we require the analysis tools to analyze the malicious file. There are freely available tools that can be downloaded and used to examine the same. But it will take a long process of downloading all the tools one by one. Flare VM has pre-build tools for malware analysis which will save time for downloading the tools. Flare VM has a combined package of all required tools for analysis. Let us move to a further step for downloading Flare VM.
Step 3: Downloading & Installing Flare VM:
To download the Flare VM you can get the GitHub link and download the files from the following references. You can follow up on this reference and download the VM and install it.
https://github.com/fireeye/flare-vm

After installing the Flare VM, it should look like this. As it has a combined package of required tools.
That is all you would need to set up. In the last and final part of the blog for Malware Analysis, we will understand the practical in-depth approach towards the analysis.
Author,
Vijay Damor
Attack & Pentest Team
Varutra Consulting Pvt. Ltd.