Security Assessment Case Study
About Our Client
The client is a major non-banking finance company (NBFC). The Company is engaged in lending and allied activities. It focuses on consumer lending, small and medium-sized enterprises (SME) lending, commercial lending, rural lending, fixed deposits and value-added services. Its consumer lending products include two-wheelers and three-wheelers finance, consumer durables finance, digital products finance, retailer finance, salaried personal loans, e-commerce consumer finance, e-commerce seller finance and home loan.
Objective
The client sought Varutra for advice on securing their entire Network Infrastructure from security threats which can lead to loss in Confidentiality, Integrity and Availability (CIA) of the data. Client wanted to ensure that their Infrastructure meets all the security standards.
The Challenge
Client’s major business goal was to provide their customers with secure platform to manage their financial transactions. It was imperative for the Client to ensure that their application was not susceptible to technical or design flaws while providing a smooth banking experience to its customers. Hence, Varutra team to be more cautious while conducting the security assessment which won’t disrupt availability of the application.
Major concern was to secure the customer’s sensitive data, client being from financial background has developed applications considering all secure configurations like SSL Pinning and root detection implemented.
Security Standards Followed at Varutra
Varutra’s security assessment methodology is in accordance with best standards and follows guidelines from OSSTMM, OSINT, NIST, ISSAF, CIS and OWASP for web and mobile and SANS for Network Penetration Testing. Varutra follows Application Security Verification Standard (ASVS) which helps developers with the requirement for secure development.
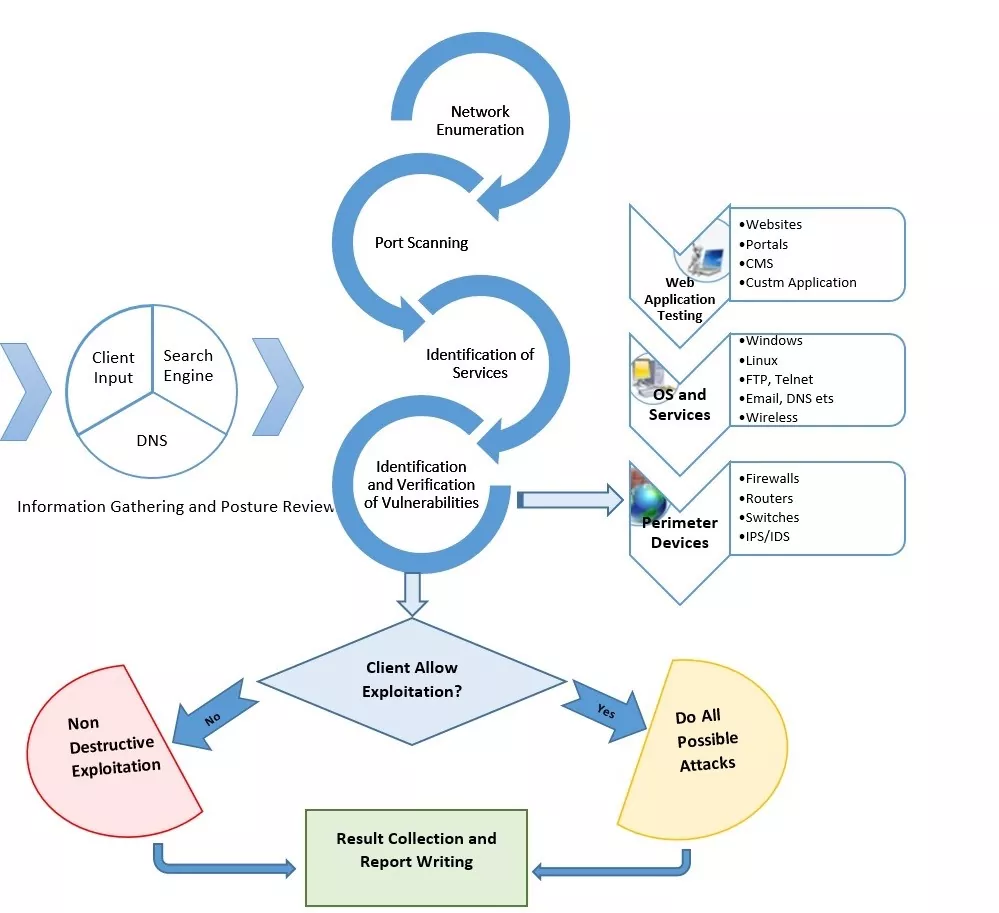
Our Approach
Varutra’s methodology involves assessing the security posture of the critical servers and networking devices to find out vulnerabilities (if any) to check the security of server systems from an attacker’s point of view; specifically, as an internet malicious user, and determine if the hosts could be compromised to gain access impacting Confidentiality, Integrity and Availability of data.
- Pentesters gathered information related to the organization in the Reconnaissance Phase which includes sensitive data like IP addresses, dumped data on darknet, email IDs, phone numbers which was used to perform various social engineering attacks.
- Upon performing all passive scans and gaining sensitive information related to the organization Pentesters initiated with Active scanning phase on the target which involved the scanning of various ports and find vulnerabilities related to it.
- The client network was consisting of various technologies such as firewall, IPS, web servers, database, networking devices, SMTP servers etc. The goal was to understand the current level of external risks which may compromise the sensitive data of the customer as well as the organization.
- With the client permission, pentesters started with black box testing for web application in which they found many critical and high vulnerabilities, SQLi lead to Remote Code Execution, by which Pentesters were able to dump database and also get the source code of the application.
- After getting the source code of the application, Pentesters started analyzing source code of the application which lead to discovering several high severities as well as medium severity vulnerabilities.
- By logging in to the application Penteters also discovered business flaws which can lead to high business loss. Pentesters also tried to exploit each vulnerability and manually assessed full application and source code.
- Post completion of the web application assessment, pentesters started the assessment of mobile application with static analysis and reversing the application to understand application behavior. Reversing application helped Pentesters in dynamic testing which lead to many vulnerabilities like SQLi, authentication bypass etc. Pentesters edited SMALI code to bypass root detection and virtualization detection.
- Post successful completion of Network, Device Conf. Audit, Web and Mobile Application security assessment, Varutra was engaged to perform encryption audit for the organization as well.
Key Findings & Observations
Varutra, with its skilled Pentesters, was able to break into the organization’s infrastructure both using network as well as web application attack surface and gain access to the systems. While doing assessment Varutra found multiple critical vulnerabilities which are as below:
- Eternal Blue (SMB WannaCry)
- Open mail relay on SMTP server
- Multiple servers and devices with weak credentials susceptible to brute force attacks
- SQL Injection
- External XML Entity (XXE) and Server-Side Request Forgery (SSRF)
- Improper Session Management and Authentication bypass
- Database having sensitive data in unencrypted form
- Security misconfiguration on networking devices
- Encryption key or subkey were not unique per device
- No recovery/master key for database
- Misconfigured firewall
- Multiple medium and low severity vulnerabilities
The assessment was done with the automated testing using commercial and open source tools as well as extensive manual testing for verification and validation. This was the most important phase of a penetration test because it effectively demonstrates the impact of breach for the concern organization.
Deliverables
The reports and remediation provided by Varutra were customized to match the Client’s operational environment and requirement.
The following reports were submitted to the client:
How Varutra Helped
Our Penetration Test helped numerous clients to identify the potential threats / vulnerabilities that could have compromised entire infrastructure. All of our clients are assisted in assessing percentage of potential business and operational impacts of successful attacks / exploitation. Additionally, the client gained the following benefits:
Conclusion
Penetration testing is often done for varying reasons. Two of the key goals our team and the client team aimed for, were to increase upper management awareness of security issues and to test intrusion detection and response capabilities. After conducting the Pentest and compromising the organization, we engaged the client in a controlled offensive / defensive threat detection challenge, allowing the client several days to identify and remediate active threats within their systems. After this challenge was complete organization was appointed to conduct training for the key internal security team like secure code development as well as further advisory on remediation tactics. In the end our client was able to meet the highest level of compliance and regulation standards, develop better security practices and reassure their customers, employees, and board of their continued dedication to best business practices and continued growth.
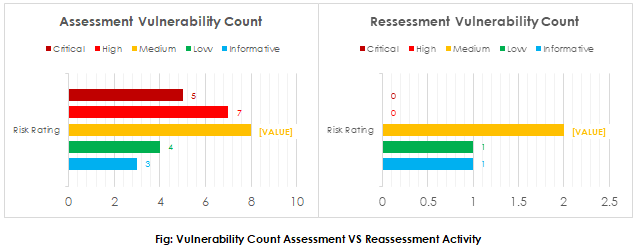
After mitigating all security risks by following all remediations suggested by Varutra, the client infrastructure was secure from all possible risks uncovered by Varutra and effectiveness of these vulnerabilities can be verified by conducting Reassessment activity on same target scope to compare strength of the security posture. Upon Reassessing the target scope for all security vulnerabilities following are the vulnerability count for Assessment and Reassessment activities.
Upon applying all the patches and following all the remediation as per the documented report, the client was able the migrate the security posture of their infrastructure from an overall High severity to Low severity upon further patching and following secure configuration the Network infrastructure was secured from all Security Risks which would have otherwise affected Confidentiality, Integrity and Availability of the data. Now client’s Infrastructure met all compliance standards and regulations which will influence their business positively.