Measuring Your Organizations Information Security Maturity
Cyber threats vary from organization to organization and from one business sector to the other sector, thus ‘a one size fits all’ approach to cyber and data security does not work and a ‘blanket’ approach is extremely pricey in the domain to come up with and adhere to. So Information Security Maturity Assessment is one way to protect your information asset and secure your system against cyber threats.
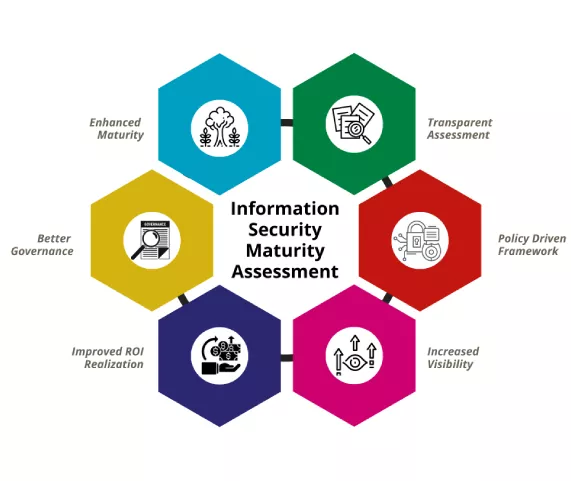
Varutra's Information Security Maturity Assessment Model analyses your organization’s cyber security posture and compliance necessities to determine the effectiveness of current security measures implemented and followed in business operations. It conjointly evaluates whether the existing position aligns with organizational cyber maturity targets primarily based upon risk appetency, neutral expectations, and regulatory, compliance, statutory requirements these form the baseline framework for maturity assessment activity.
Understanding your position of the current implementation, we will highlight areas for improvement and the priority of the investment needed to ensure the GREY risk areas are addressed enough to mitigate possible threats and reduce the vulnerabilities eventually.
Our Approach for Information Security Maturity Assessment
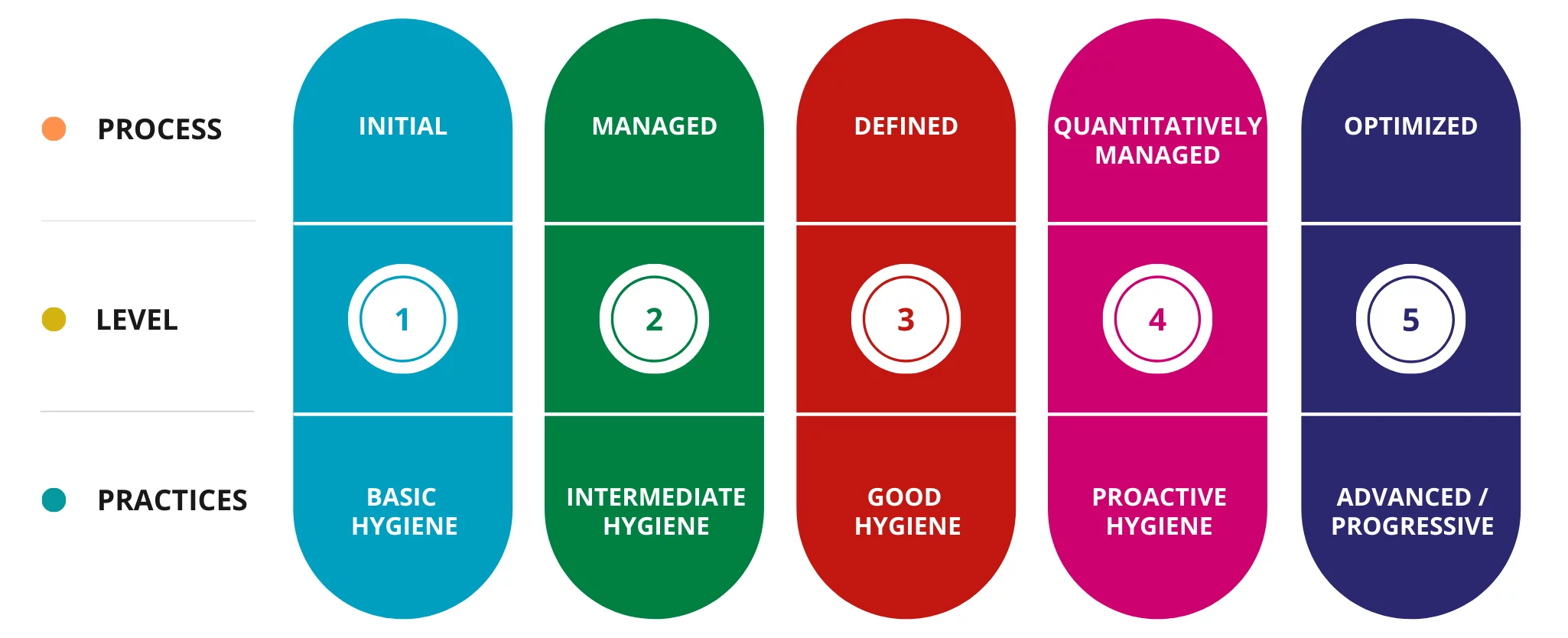
Varutra Security Consultants will evaluate 20 domain areas within 89 key security control areas that have a bearing on your organization’s cyber security posture. They score these processes or domains using a 5-point scale that ranges from 1 (non-existent) to 5 (optimized).
This Information Security Maturity assessment process which can take few days depending on business size and complexity and Geo-Location Spread and areas of in-scope parameters – divisions and follow with a detailed report of security assessment that will clearly depict and highlight the current maturity level of process within a domain assessed and any additional steps that are further needed to meet the cyber maturity levels which are necessary to achieve a better mature score and to implement a better process. Further, we will provide mitigation assistance, roadmap, and customized dashboard to track -monitor and achieve and incorporate missing processes.
Varutra's Assistance to help you identify the gaps in your processes
The overall security assessment focuses to identify and highlight where security measures are not proper places and incorporated with reference to the industry-accepted best practice – benchmarks and where efforts must be concentrated and organized to improve the organization’s cybersecurity posture. This will help and organization to understand and identify the RISK areas. We recommend you undertake an Information security maturity assessment in the following scenarios:
You want to Benchmark and HIGHLIGHT your maturity assessment result against the rest of your industry competitors.
You want to Weave a stronger LAYERED NET of a cyber security culture within the organization and nurture it further.
You want to ensure that your business organization is prepared enough to face the evolving security and upcoming threat landscape and challenges in the Cybersecurity Domain.
Varutra's Assistance to prioritize your investment in security expenditure
Varutra will provide a detailed Information Security Maturity Model Assessment Report, detailing the findings, evaluated cyber maturity levels and recommendations, the process followed to complete the evaluation, easy tracking, and monitoring support for governing and ensuring improvements on the grey area points. These findings will shape how effort is concentrated to improve maturity levels and which actions should be prioritized by the organization to increase their maturity score eventually and incorporate missing processes.
This can facilitate and will be a MODULAR HUB of effective project planning, risk management, resource forecasting, and budgeting and assures organization with a cyber strategy planning tool, to ensure that your native team targets the right amount of maturity for areas that can create improvement and protect valuable assets as the activity progresses.
Communicating security metrics to senior management and stakeholders
It is increasingly a much common fact that senior executives and Board of Directors must be reassured and actively provided with evidence and reports that provide and depict appropriate information management safeguards and process parameters are in place. Your organization’s key decision-makers are provided with an independent non-technical graphical-based explanation and timely updates of the current cyber maturity levels and recommended actions, in line with the organization’s risk appetite and desired maturity further roadmap and process details. We at Varutra follow a distributed RACI model in each Project.
Make the Most out of Cyber Insurance
It is a more common fact to see nowadays that many insurance companies are required with a security assessment to gauge and come up with how mature an organization’s security measures are incorporated. By conducting an information security maturity assessment, you get your organization to stand tall highlighted in the best possible position to demand the best premium from your insurance provider.
With Motto of Continuous improvement
Continuous improvement is an important aspect of remaining compliant with several regulations and upcoming compliance requirements; therefore, many organizations and business leads find benefit in repeating this information security maturity assessment at regular intervals of time. This provides a consistent metric for tracking and monitoring for key stakeholders (e.g., Senior Management, the Board, Regulators, or shareholders and other interested parties) to measure and demonstrate continuous improvement and increasing maturity levels.
What is information security?
Assess your business's current security maturity levels to help your organization
to operate securely with a clear understanding of where they currently are and develop best practices
to provide a roadmap to improve its maturity.
Read Related Blogs / Case Studies