
Mobile Application Security
With the rapid rise of mobile technologies such as smartphones and tablets within an enterprise creates a unique set of challenges that must be addressed in a systematic way by identifying privacy, security and compliance risks from applications development to deployment stages.
Varutra utilizes its extensive knowledge, experience with technical and operational skills to examine the issues and challenges unique to the security and management of mobile technologies and the information the mobile devices store and processes by the applications.
Varutra uses blend of services offerings such as Penetration Testing, Secure Code Review, Application Architecture Review as well as Vulnerabilities Patching in protecting the applications against latest cyber attacks.

Mobile Application Penetration Test
The mobile application penetration testing / security assessment aims at identifying the vulnerabilities that can be exploited in the target application on the mobile devices.
The testing approaches involves Black Box Penetration Testing, Gray Box Penetration Testing where PenTester acts as an authenticated as well as an unauthenticated user of the app while assessing it. This type of test involves building a threat profile in order to discover contextual security vulnerabilities specific to the application.
We at Varutra perform complete security assessment of applications, along with the associated web services and APIs.
The testing involves assessing mobile applications exhaustively for vulnerabilities that put any valued data at risk. Our methodology follows OWASP Mobile Application Security Verification Standard (MASVS) and OWASP Mobile Top 10 Security Guidelines.
Our assessments are complimented by detailed reports on the vulnerabilities identified, along with relevant proof of concept, recommendations for vulnerabilities mitigation. You can also opt for Varutra’s Vulnerability Remediation Services.
We provide Mobile Application Security Services across different platforms such as - Android, i0S of type Native, Hybrid, Web as well as Mobile Device Management apps.
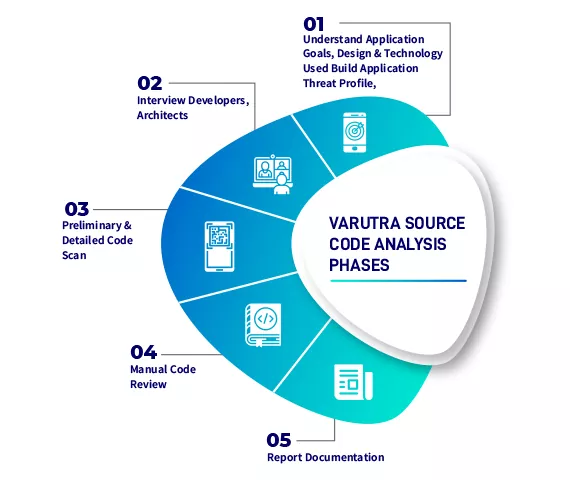
Source Code Review
A comprehensive source code analysis involves a security expert with strong development experience and proven analytical capabilities, examine the source code of your application to identify programming and logical errors.
The aim is to examine the source code of the application and identify vulnerabilities before the application is deployed. Varutra consultants understand the application business objectives, its design and the technologies used for its implementation. Application threat profile is created to identify critical code areas to concentrate during the code analysis. Blend of open source and commercial code analysis tools will be used followed by manual verification approaches, clubbed with general and best practices of coding standards respective to various platforms such as JAVA, C#, .NET, PHP, python, ruby, android, swift, HTML5, C++, JS, ASP.NET, VB.NET, Visual Basic, PL/SQL, Perl, JSP, Objective C, VBScript.
Our experts also recommend the cost-effective and practical remediation strategies specific to your business objectives in order to control, mitigate and prevent these defects.
Application threat profile is created to identify critical code areas to concentrate during the code analysis. Blend of open source and commercial code analysis tools will be used followed by manual verification approaches, clubbed with general and best practices of coding standards respective to various platforms such as JAVA, C#, .NET, PHP, python, ruby, android, swift, HTML5, C++, JS, ASP.NET, VB.NET, Visual Basic, PL/SQL, Perl, JSP, Objective C, VBScript.






