Varutra Audit and Compliance services incorporate a perfect combination of People, Process and Technology.
Our Audit and Compliance services are highly customizable and have been structured in such a way to cater to ever changing business dynamics.
Our services are led by expert certified consultants having sound experience into variety of critical business areas leading to perfection, flawless execution with actionable metrics.
Out team understands customer’s pain points and have the passion and skills to make a difference by offering expert guidance and quality deliverables.
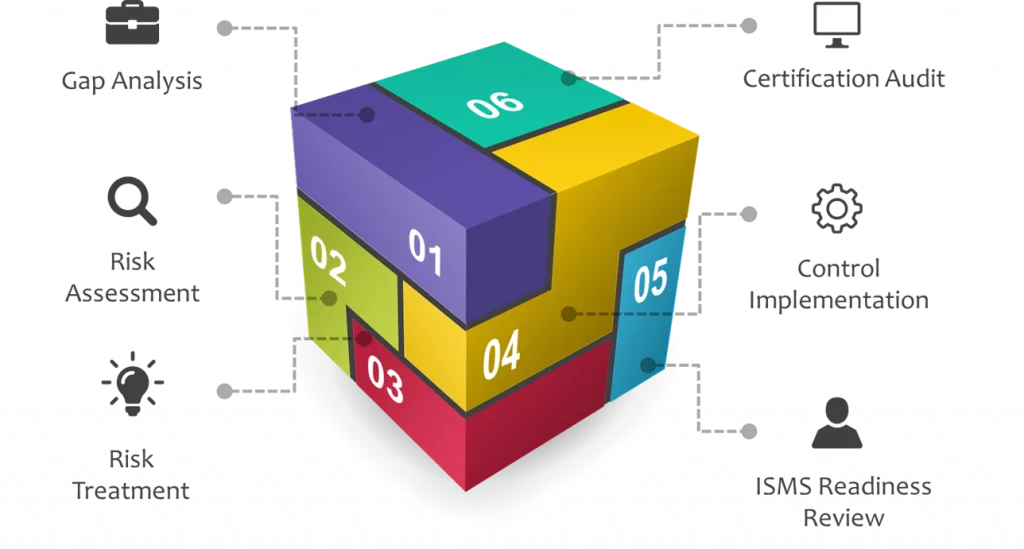
Key Service Offerings
- Create a security benchmark for the organization at large.
- Create and execute audits for inhouse and vendor
processes. - Create and maintain a roadmap by having third party
auditors view. - Identify Strengths and Weaknesses of current security
practices.
- Prioritize the exposures that present the greatest risk.
- Deliver prompt audit results focusing on customer centric reporting requirements.
- Provide risk mitigation recommendations consistent with compliance regulations.
- Incorporate security best practices, client specific industry best practices, and client business objectives.
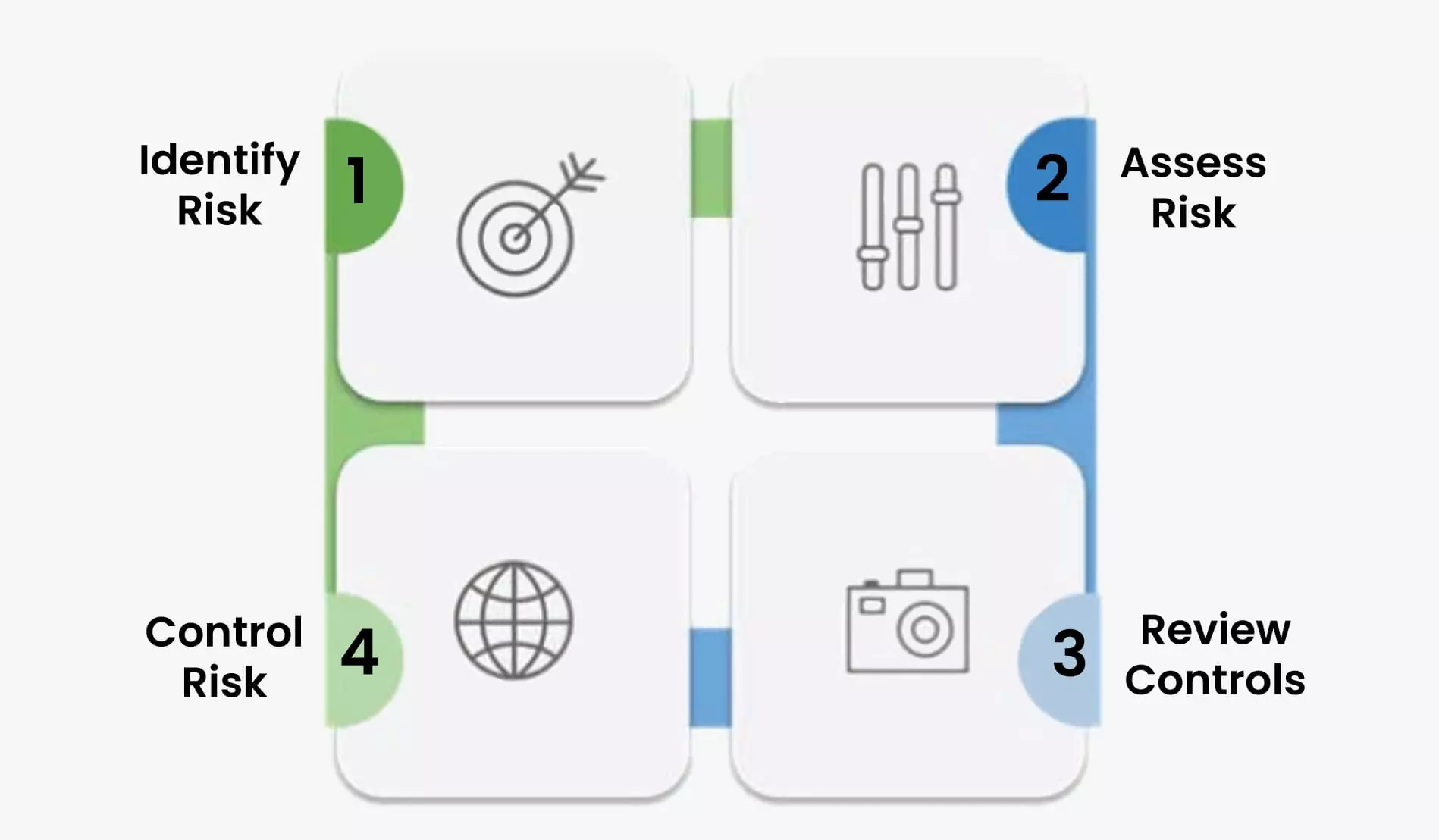
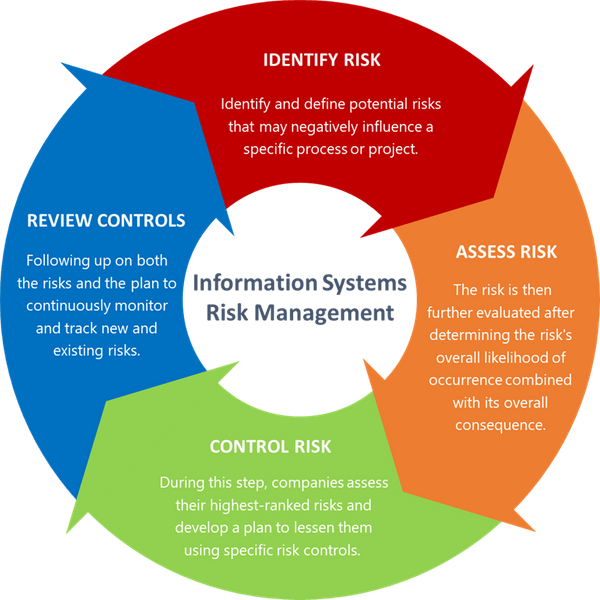
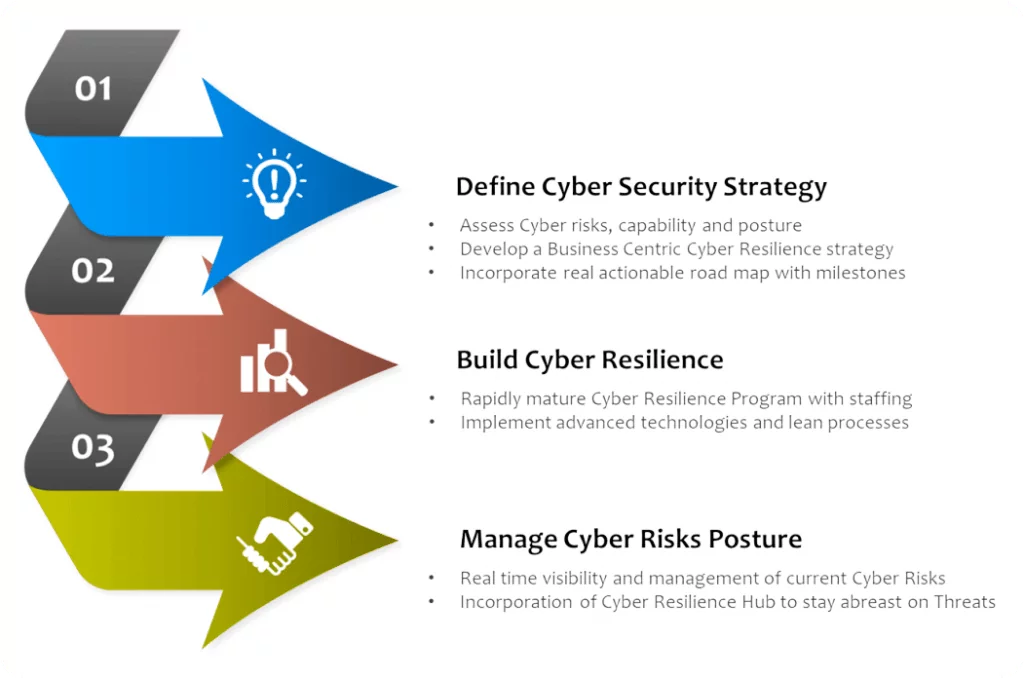
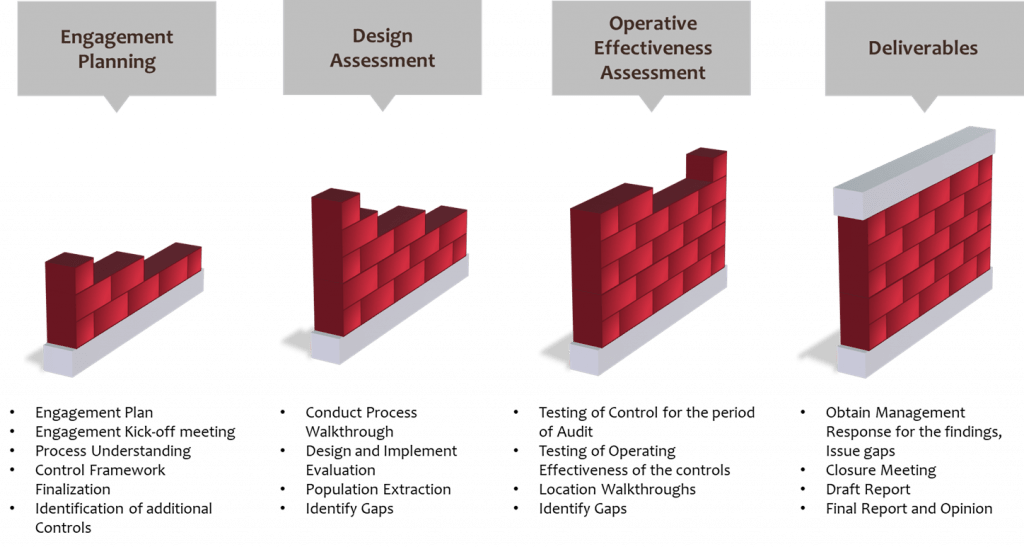
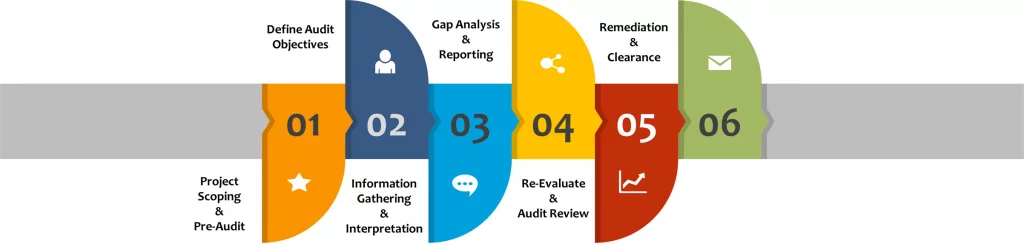
Our Approach
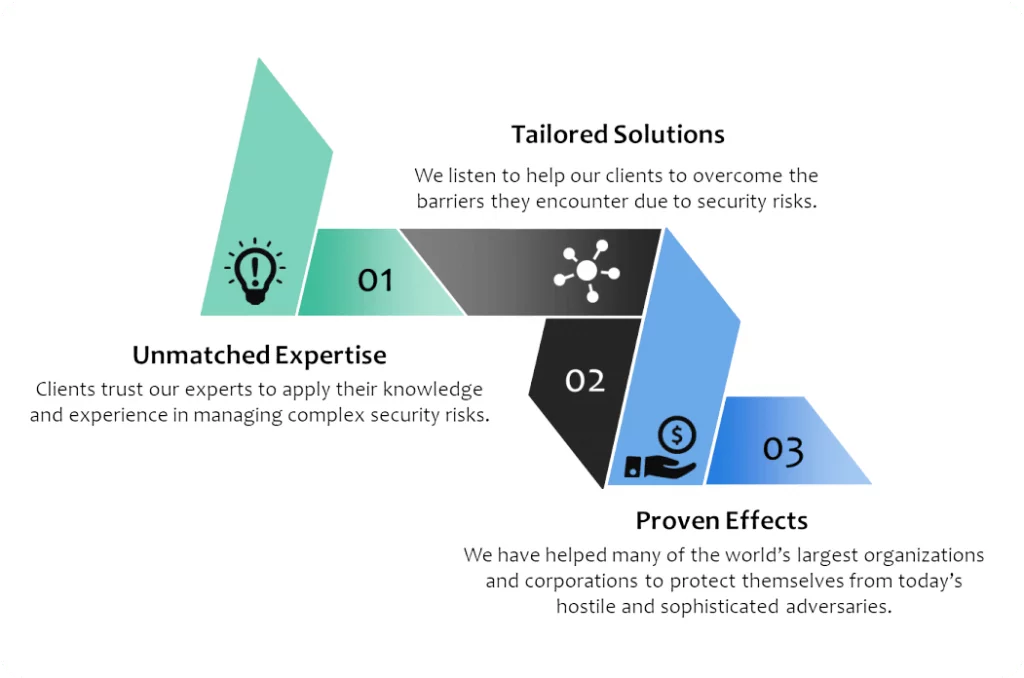
Why Choose Us?
Our dedicated team supports all standard and industry specific audits and manages relationships with external auditors so that organizations focus on what is important - growing the business and serving the customers.
With Varutra as a trusted partner, our clients benefit via our expert guidance to manage the complicated world of Audit and Compliance, as well as predictable results.
Our processes, governance, and service levels are proven to meet stringent and demanding requirements of diverse clients spread across various business groups across the globe.
At Varutra, we leverage a deep and experienced pool of skilled consultants to deliver all our assurance and advisory services. We set extremely high standards and our team also holds multiple accreditations and professional qualifications to make things possible.
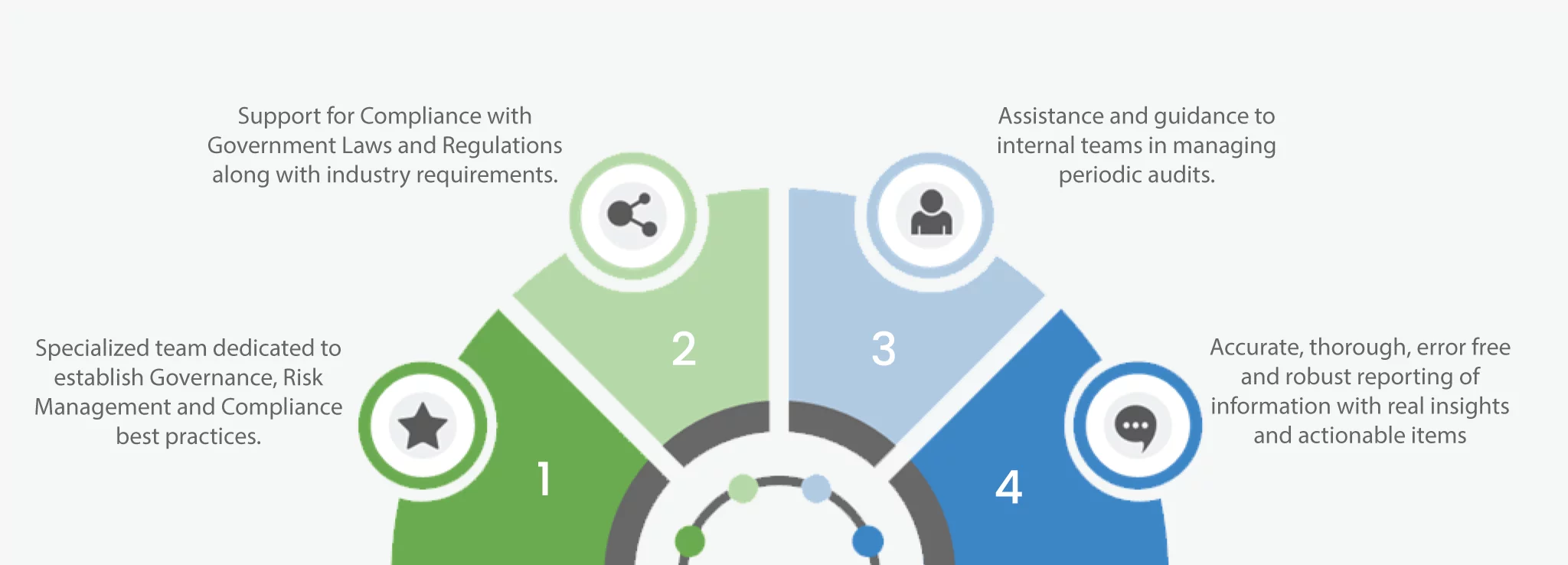
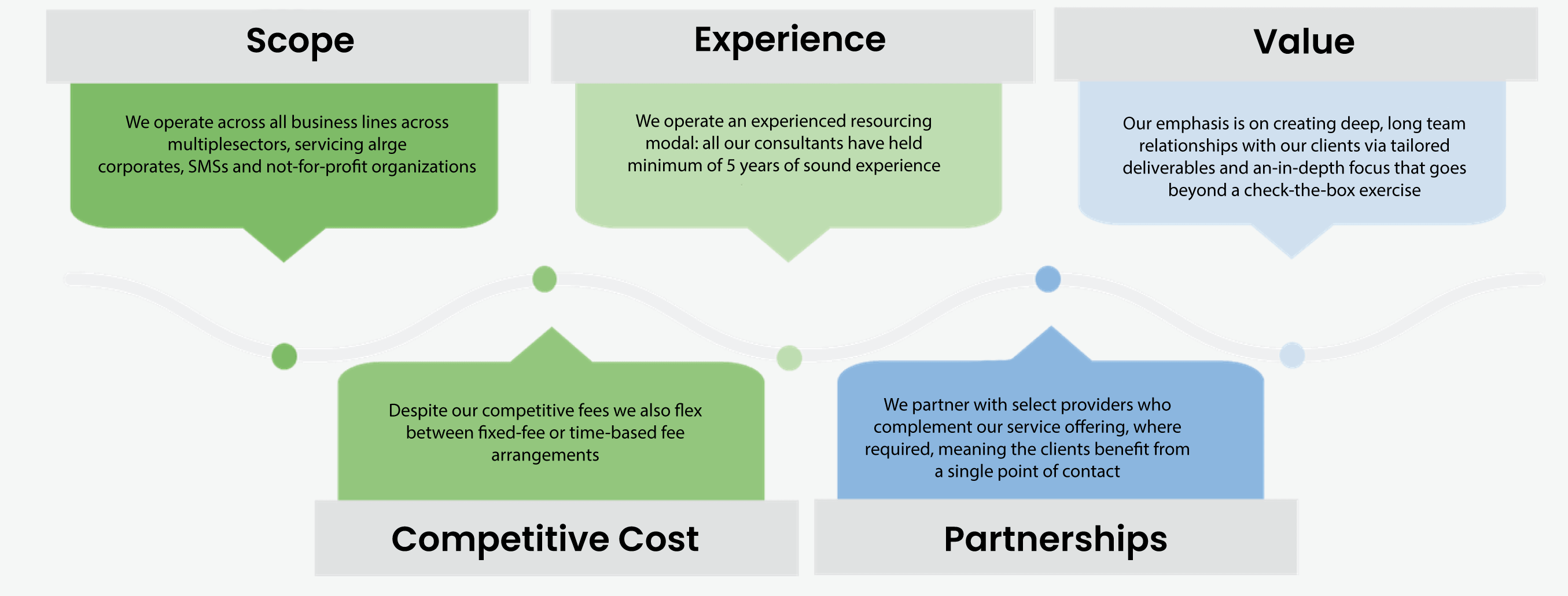
Services Key Highlights
Our Audit and Compliance Services Key Highlights