Network Infrastructure Security
Our technical know-how drives beyond traditional vulnerability scanning to reveal the real actionable threats in the network infrastructure via rigorous assessments to uncover external, and internal threats.
Network security evolves as quickly as the technology it’s built on which is why our penetration testing services go beyond traditional vulnerability scanning methodology with our expert certified consultants.
Our penetration testing services outline the network security risks with business impacts you need to be aware of and with our unique approach towards network pentesting which goes above and beyond standard vulnerability assessment followed by penetration testing.
Our assessment team recognizes, validates, exploits, and documents the most subtle of vulnerabilities exists in the network with sufficient Proof of Concept evidences.

Network Vulnerability Assessment
In today’s world, rapid business evolution, and the constant evolving threat landscape has lead to multiple security challenges for client’s organization's.
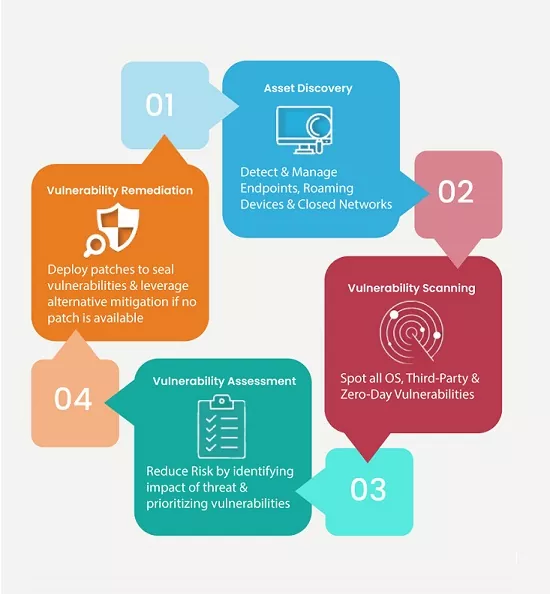
Varutra’s Vulnerability Assessment services helps you to respond by detecting, classifying, categorizing and addressing security vulnerabilities observed and in providing the ongoing support and guidance to remediate them in a timely manner.
Our methodology focuses on identifying, validating, prioritizing the vulnerabilities in the target systems and provide realistic status to help them fix those.
Our expertise lies in conducting external and internal vulnerability assessment and by leveraging a combination of open source and commercial tools which are used along with major stress on manual verification and validation of each and every vulnerability to understand the vulnerability potential, risk involved in case the vulnerability gets exploited on client’s network and its business impact.
Vulnerabilities will be prioritized considering the client's business and reported with specific mitigation steps in the recommendations.
Network Penetration Testing
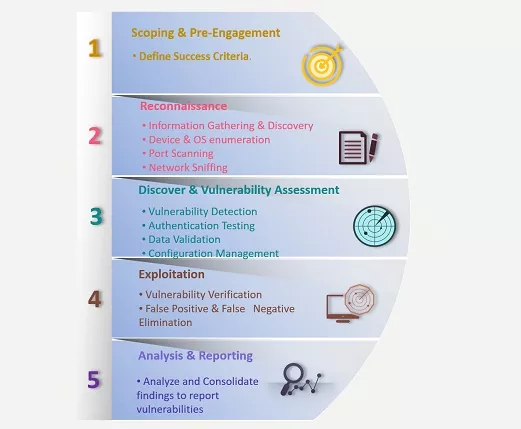
Network Penetration Testing, also known as network pentest or pentesting, refers to the testing of computer networks, computer systems, networking devices and applications to identify and report security weaknesses residing on them.
It is of utmost importance to assess the corporate network security posture to defend and protect the data against known/unknown cyber attacks.
Varutra cyber security cum penetration testing services involves assessing the network to gain unauthorized access in the network as an external entity/hacker and/or as a malicious insider trying to elevate access privileges and perform malicious activities.
As per the client’s need black box, gray box or combination of both approaches can be outlined. No exploitation will be carried out before seeking client’s permission during the engagements.
- Proof of concept exploitation can be carried out on testing servers.
- Assessment reports will prioritize vulnerabilities listed with severity rating, business impact rating and detailed recommendations to help client team to patch the vulnerability.
- We incorporate industry accepted penetration testing standards which helps organizations to effectively manage cyber security risks by identifying, validating, documenting the outcome and at last helping clients to remediate that could otherwise lead to data and assets being compromised by malicious entities.
Configuration Audit
In the days of cyber threats, it is essential that organizations should use trustworthy configuration, review and audit their network infrastructure on a periodic basis.
Varutra’s technical configuration audit process is highly customized to suit the organization’s network infrastructure to ensure that the enterprise’s IT assets such as Operating systems, Databases, Applications and Software's as well as Network devices are operational and are compliant to standards and policies.
The audit process broadly consists of auditing the perimeter devices, network devices such as Firewall, Routers, Switches, Load Balancers, IPS/IDS and Server Systems such as Domain Controllers, File Servers, FTP Servers, Email Servers, Proxy Servers, Antivirus Servers and Databases comprising the entire network architecture.
For all in-scope targets, Varutra consultants will analyse various components of identified operating systems using automated tools and manual techniques to identify known vulnerabilities in categories such as:
- Security Patch Levels
- File Permissions / Registry Permissions (as applicable)
- Misconfiguration issues
- File Systems
- Users / groups presents on the system
- Services running
- Network Configurations
- Event Logging
- Database Configurations
- Version specific vulnerabilities
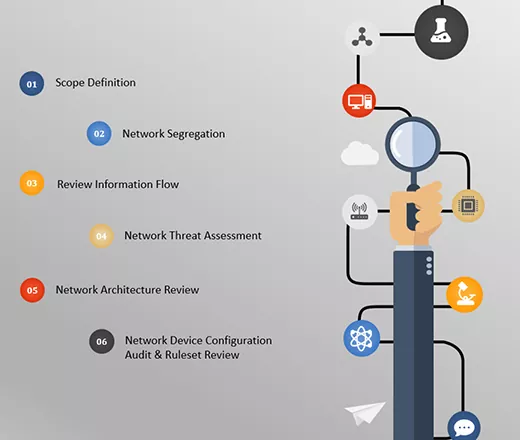
Network Architecture Security Review
Network Architecture Security design review process for an organization analyzes the structural design from a security perspective. It helps to recognize and validate the design elements which might impact the security posture.
It is a common practice to set up the network infrastructure in the very initial days and once the setup is completed, organizations fail to recall about it. Over the time, as business evolves, network infrastructure also evolves and possibly opening it up to new vulnerabilities unless it is reviewed periodically.
Varutra network architecture review is a process of thoroughly assessing the network component’s configurations with their placements in the network and the overall network design. Our network security team will observe the network from defense in depth strategy to withstand any network attacks. The review objective is to assist in increasing the security posture of the existing network infrastructure.
Organizations can review the network architecture by their own, but there is no substitute for having an independent skillful expert sporadically reviewing it and checking for the hidden weaknesses.
The NSAR helps identify weaknesses in areas such as - network security policy and procedures, network design, device configurations, during the assessment, Varutra will:
- Identify organization’s network security policies / standard procedures
- Assess whether network security solutions are aligned with business requirements and goals
- Identify all technology solutions regarding network security
- Assess the target network design and architecture, review of redundancy, network segmentation, and access management tools
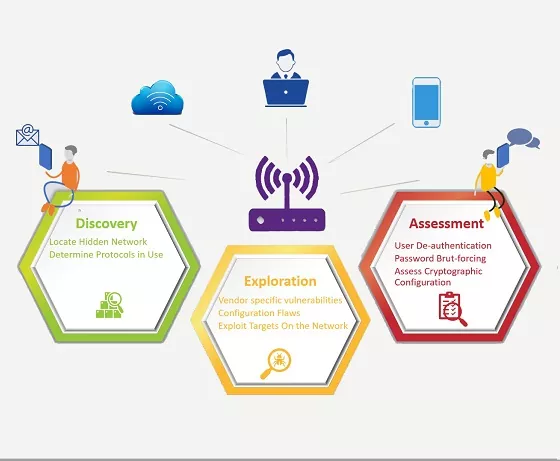
Wireless Penetration Testing
Wireless Networks are an integral part of organizations network infrastructure and have exposure to internal/external threats.
Several wireless deployments are accessible beyond the acceptable physical premises leading to insecure infrastructure, which presents unique threats which is where attackers can target wireless access points with pre-defined and planned attack strategies.
Varutra’s wireless security audit methodology is a result of research, proven techniques, advanced testing tools and rich experience of our security experts in this area to ensure the maximum coverage over all possible threats from various dimensions.
Wireless security assessment will help in detecting, locating and mitigating the risks posed by the current implementation of wireless network technology by taking a very pragmatic and systematic approach to assess and report the current security posture of wireless networks be taking care of below:
- Defining Testing Scope
- Detection of Wireless Access Points as well as Rogue Access Points (if any)
- War Driving
- Wireless Network Vulnerability Scanning
- Vulnerability Identification and Validation
- Wireless Device Configuration Review and Reporting