Key Service Offerings
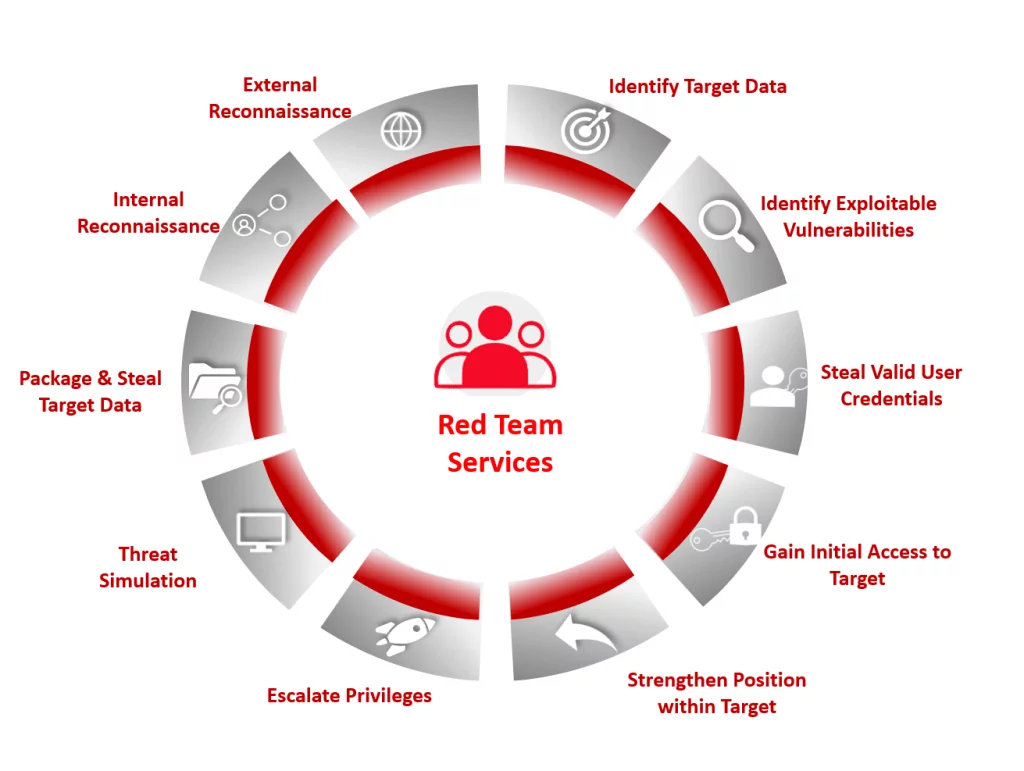
- Red team exercises rapidly dissipate any hidden threats in an organization, and focus attention on planning & investment which will have a clear purpose
- By creating a broad acceptance of vulnerabilities, such an exercise builds organization-wide consensus & awareness without having to learn from ‘painful experiences’
- A defined perspective on attack scenarios and potential business consequences post successful attack
- Red team exercises build confidence within an organization, from shareholders down to the security & business continuity teams, that preparation, planning, and investment are appropriate to task
- Better risk understanding and management from board level where greater involvement will create better prioritization, and use of budgets & resources
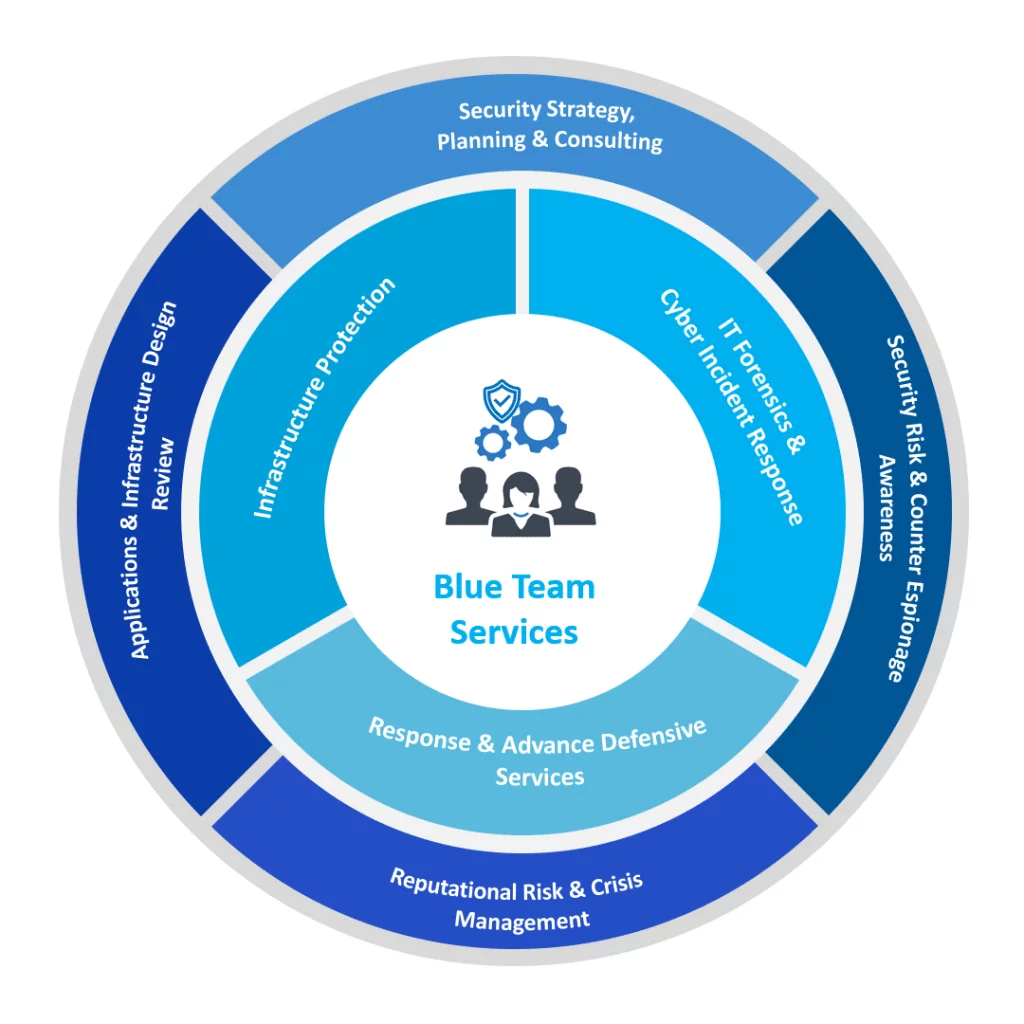
Service Deliverables
- A report presenting results & conclusion of the exercise, covering technical, process and policy issues with a series of industry best-practice recommendations
- Review of results and feedback in a workshop setting, to build awareness and alignment among stakeholders, and a roadmap of measures to improve security & resilience in the future
- Short-term tactical fixes for immediate remediation of any outstanding vulnerabilities within the tested environments
- Long-term strategic initiatives that will proactively thwart any potential repetition of vulnerabilities discovered during the exercise
- Our aim is at providing industry best extensive Dark Web Analysis service to facilitate security to the Organizations from all possible threats emerging over the Internet as well as dark net.
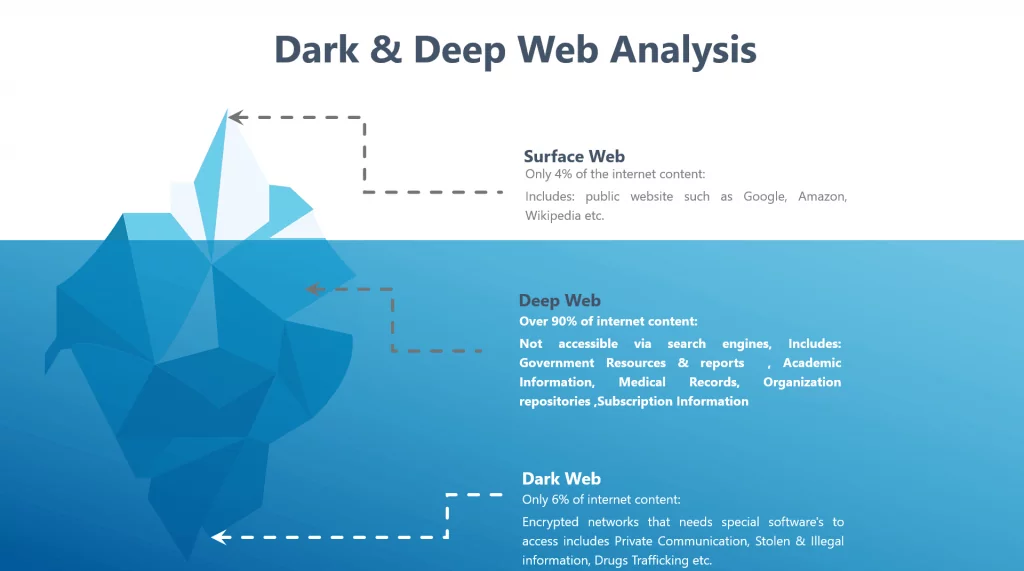
- Dark Web Analysis is the method of processing and analyzing data related to the organization over the surface web, deep web, and dark web. The type of data leaked comprises Employee details, Sensitive File/Codes, Dumped Credentials, etc. This data is extremely competent for an evil intended attacker trying to compromise an organization.
- The Dark Web consists of sensitive organization dumped information. With the disclosed information an organization can safeguard itself from possible threats.
- Multiple Dark Web offerings are highly relevant for the cyber security domain in anticipating and preventing attacks, such as information about zero-day exploits, stolen datasets with login information, or botnets available for hire.
Apart from Dark Web Analysis we follow extensive Open Source Intelligence (OSINT) for gathering all sensitive details from Dark and Deep Web which covers additional facts than traditional methodology.
Advantages
The Dark Web Analysis uncovers all minor details which are found by the expertise of our Security Consultants that might be missed out or go unnoticed via automated approach. Choosing us will have several advantages in Dark Web analysis:
- Identify / Mitigate vulnerable endpoints which can be used by attackers to infiltrate into the organization network infrastructure
- Safeguard vulnerable endpoints which can be probable target of an attacker
- Assurance to end user for a trusted and reliable service
- Access to leaked data over the internet to mitigate probable outcomes of the breach
- Gain an upper hand in terms of security with respect to competition
The objective of the Phishing Diagnostic Service is to assess the risk associated with an organization with respect to its public, social presence in the form of people, process, and technology. There are many ways to protect an organization from technology associated attacks but still the insecurity associated with 2 P's i.e. Process and People; lack of which may lead to severe security consequences.
Varutra manages to reduce the risk by the Phishing diagnostic service and minimize the security issues, which can have business impact on the organization.
Advantages
- Helps organization understand the behavioral response of employees and preparedness against impersonate attacks.
- Reduce overall security risks arising from Phishing attacks by protecting an organization's social and public presence.
- Helps in improving the information security in organization through awareness programs.
- Prevention from Reputational loss, Financial loss and remediation cost due to phishing attacks.
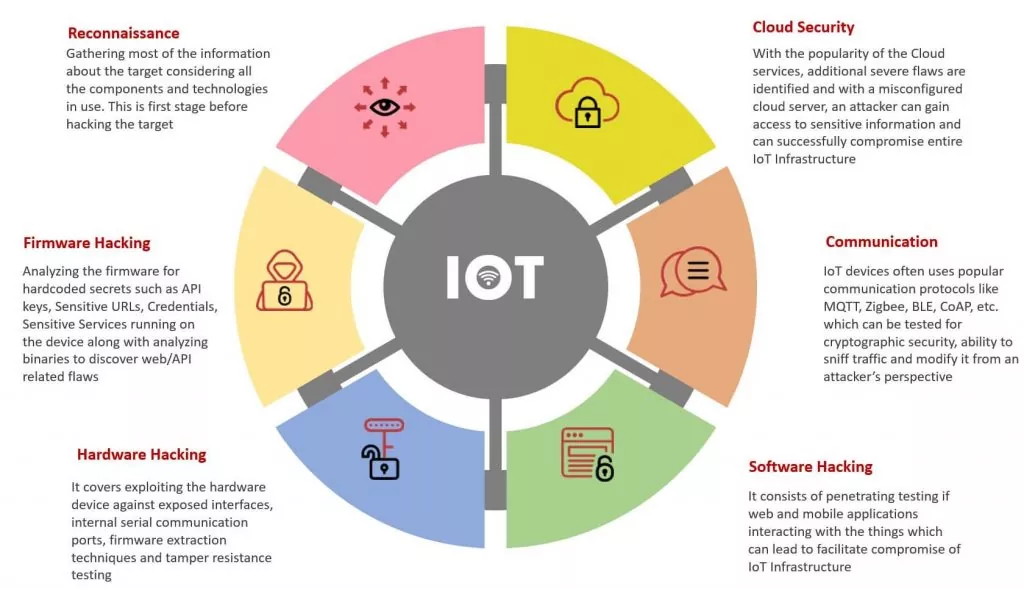
Our Security experts help you strengthen the security of your IoT products from chip to cloud. Our solutions provide coverage across technological domains, including embedded devices, firmware, wireless communication protocols, web and mobile applications, cloud services and APIs, and back-end network infrastructure.
Advantages
- Varutra IoT security experts will work with the development team to design and manufacture the secure IoT products/devices.
- End-to-End Internet of Things (IoT) ecosystem security which includes Hardware, firmware security, Radio communication, web/mobile application security assessments.
- The Security assessment for IoT Devices is highly inspired by the OWASP IoT Top 10 and other emerging industry standards.
- A well-structured approach of executing a pen test on the IoT infrastructure which will provide overall security posture to the entire IoT environment
- The security assessment lifecycle increases the confidence of the management and investors in developing more secure IoT products.
- Ability to look at the broad view of the current security position of a product/device & its ecosystem from an expert’s view