Applications Security
Secure software applications are the biggest need in today’s world. Web applications have become a must to have component in organizations with the uptime of 24/7 offering secure data and access to customers, employees, partners, and suppliers. With numerous products offering security solutions to the application layer for protecting enterprise data often they fail to do so.
Hackers find ways to carry out malicious activities and put organization reputation at stake. It is important to revamp the entire software development mechanism by adopting a secure development life cycle and right combination of testing methods to make the software self-resilient to safeguard the data.
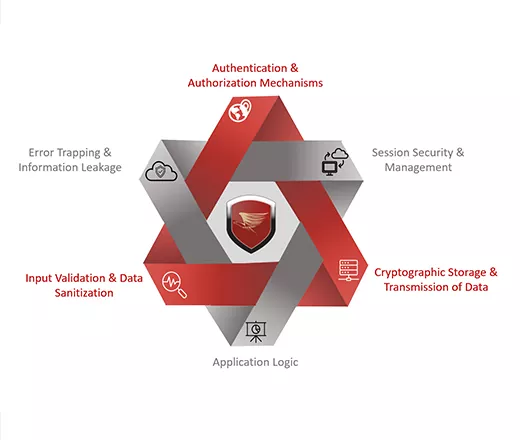
Application Security Testing
Varutra consultants simulate a hacker’s mindset to identify security holes in target web applications, including OWASP Top 10 vulnerabilities along with vulnerabilities related to business logic and implementation.
The Application Security Assessment methodology utilizes a combination of automated and manual assessment processes intended at finding security flaws in the application. Preliminary activities include identification of application layout and points of risks of relatively large magnitude.
Post this phase, tests are initiated to discover vulnerabilities in the application, leveraging novel and latest vulnerability detection and penetration testing techniques. Findings are aggregated, compiled and a detailed report is created and delivered.
Security vulnerabilities discovered during assessments are classified on the basis of the business impact they inflict on organization.
Source Code Review
A comprehensive source code analysis involves a security expert with strong development experience and proven analytical capabilities andexamine the source code of application to identify programming and logical errors.
The aim is to examine the source code of the application and identify vulnerabilities before the application is deployed. Varutra consultants understand the application business objectives, its design and the technologies used for its implementation.
Application threat profiles are created to identify critical code areas to concentrate during the code analysis. Blend of open source and commercial code analysis tools will be used followed by manual verification approaches, clubbed with general and best practices of coding standards respective to various platforms. Our experts also recommend the cost-effective and practical remediation strategies specific to your organization in order to control/mitigate/prevent these defects.
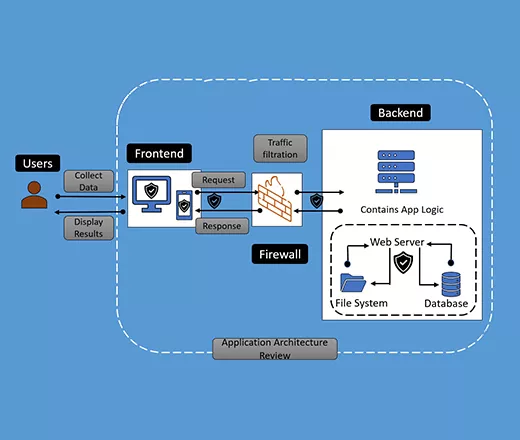
Application Security Architecture Review
The security side of the application architecture, sometimes referred to as security architecture, is often overlooked in the enterprise is what we have observed in our experience.
Varutra approaches Application Security Architecture Review holistically. Our team looks at all of the interwoven components that make up an enterprise application architecture, including the systems and infrastructure that enable the application's availability.
Designing and maintaining applications, systems, and a network infrastructure based on security standards and best practices protects organizations from attack, reduces risk, and maintains compliance implicitly with virtually any standard, regulation, or law.
- Application Architecture Documents
- Deployment and Infrastructure Considerations
- Authentication and Authorization
- Configuration Management
- Session Management
- Cryptography
- Exception Management
- Auditing & Logging
- Application Framework and Libraries
- Analysis of the existing SDLC and its effectiveness
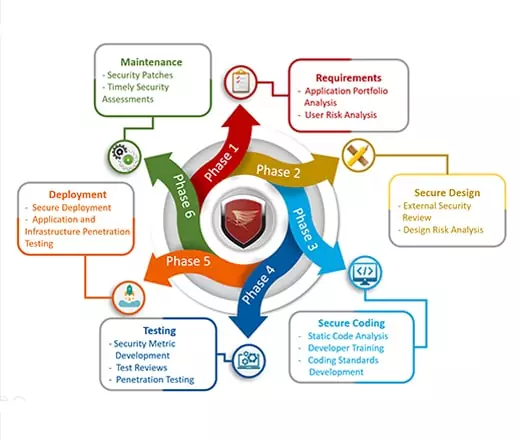
Secure Software Development Lifecycle Implementation
Cyber Security is the main concern for every customer in today’s modern days where cyber-attacks are getting smarter. So why not involve us right from the start where there is just a mere idea of the product? This will not only help to build a secure product but will also help with cost efficiency. S-SDLC stresses on incorporating security into the Software Development Life Cycle in the entire life cycle of the software development.
We understand that applications have complex background and reasoning behind certain builds. We start right with a walkthrough and understanding of the product idea to completely understand client requirements, objectives and provide secure implementation in the planning phase itself and assist developers to do a secure development which will mitigate most of the security concerns before they arise!
We always try to do more than what we commit to our clients and hence aid them throughout the SSDLC period. Seems Interesting?
Our SSDLC Implementation Approach
Security Baselines & Requirement Gathering - Security Planning, Risk Assessment & Security Controls, Findings Gaps.
Security Training & Awareness - Security training sessions for developers, designers, architects, and QA on the various cybersecurity threats, risk impact and management.
Threat Modeling & Architecture Review - Identify and manage threats early in the development lifecycle and architecture, response plan from the beginning, planning the appropriate mitigation.
Security Design & Code Review - Ensure the software is built with the most secure features, security design review, with common coding security pitfalls identifications.
Security Testing - Performing multiple level of assessments, Static Analysis, Dynamic Analysis, conducting VAPT assessments to ensure it is hack proof.
Deployment - Secure Deployment, Hardening the underlying infrastructure with best practices.
Maintenance - Assistance in periodic VAPT engagements, changes in application modulesand infrastructure upgrades.
Read Related Blogs / Case Studies