Containerization Security: A Deep Dive into Isolation Techniques and Vulnerability Management
As containerization becomes increasingly popular for application deployment, it is essential to ensure that your containerized environments are secure. Containerization provides many benefits for application deployment, including portability, scalability, and consistency. However, it also introduces new security challenges that must be addressed to protect against potential threats. In this blog post, we will explore the latest containerization security techniques and best practices to help you safeguard your containerized environments effectively.
What is Containerization ?
Containerization is a software development technique that allows developers to package an application and its dependencies into a single unit called a container. Containers are isolated from each other and from the host operating system, which makes them more portable and secure than traditional virtual machine.
Containers are created from container images, which are essentially snapshots of a running container. Container images can be shared and reused, which makes it easy to deploy applications quickly and consistently.
Containerization is revolutionizing software development and deployment by encapsulating applications in lightweight, isolated environments. By facilitating efficient resource utilization and scalability, containers have gained significant popularity. As of 2023, industry reports indicate a remarkable 67% adoption rate of containerization among organizations worldwide.
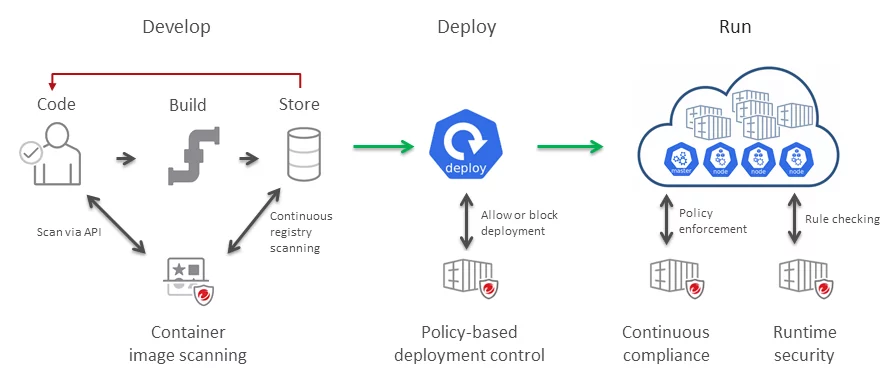
https://cloudone.trendmicro.com/docs/container-security/about/
Concept & Benefits of Containerization
A. Brief Explanation of Containerization and its Benefits
Containerization is a method of packaging software applications into standarized units called containers. Containers have revolutionized the way applications are deployed, offering a lightweight and portable solution that ensures consistent execution across diverse environments. Some of the benefits of containerization include architectural modularity, application responsiveness, fault isolation or failure prevention, and platform independence.
B. Popular Containerization Platforms and their Adoption Rates
According to a report by Datadog, Kubernetes continues to be the most popular container management system with over 30% of hosts running containered using an unsupported version. Another report by BMC Software states that containerization saw a massive leap in adoption during 2019 with over 87% of respondents stating that they are running container technologies up from only 55% in 2017. Moreover, an overwhelming majority of around 90% of organizations currently leverage containerization for running their applications in production environments.
In terms of popular containerization platforms and their adoption rates, Microsoft AKS is the most popular single option for running Kubernetes (47%), followed by IBM IKS (40%), Google GKE (39%) and Amazon EKS (35%) 6. Docker accounted for 27% market share of the containerization technologies market in 2022.
Isolation Techniques for Enhanced Security
Overview of Container Isolation and its Significance
To guarantee strong containerization security, effective isolation is crucial. Containers must be isolated from each other and the underlying host system to prevent unauthorized access and mitigate potential attacks.
Several techniques contribute to this isolation:
a.Resource Isolation: Ensuring Segregation of Resources Among Containers
Resource isolation is a technique used in computer systems to ensure that resources are allocated and used in a secure and efficient manner. It is particularly important in multi-tenant environments where multiple users share the same resources. Resource isolation in network slices ensures that each slice operates independently, preventing any unauthorized or malicious attempts to access or manipulate resources from other slices. There are three types of resources for which isolation needs to be ensured: CPU, memory, and network access.
Resource isolation is achieved by isolating resources like CPU and memory between tenants. Network isolation is achieved by isolating network access between tenants. In a single tenant environment, resource isolation can be achieved by securing with Azure Active Directory. In a multi-tenant architecture, resource and identity isolation can be achieved by disabling all cross-tenant collaboration capabilities and effectively building a separate identity.
b.Kernel-Level Isolation: Isolating Containers at the Operating System Level
Kernel-level isolation is a technique used in computer systems to isolate containers at the operating system level. It relies on technologies such as Linux namespaces and control groups (cgroups) to ensure that processes within containers do not affect other containers or the host system . By isolating containers at the operating system level, kernel-level isolation prevents processes within containers from affecting other containers or the host system.
c.Network Isolation: Securing Container Networks and Preventing Lateral Movement
Network isolation safeguards container networks, limiting their communication to authorized endpoints. Techniques such as network namespaces and firewall rules prevent lateral movement and restrict access to sensitive resources.
Network namespaces provide a way to partition network resources such as interfaces, routing tables, and ports into separate namespaces. This allows for the creation of multiple virtual networks on a single physical host, each with its own set of network resources. Network namespaces can be used to isolate containers from each other and from the host system.
Vulnerability Management in Containerized Environments
Containerization does not eliminate the risk of vulnerabilities. To maintain a secure container ecosystem, organizations must employ effective vulnerability management practices:
A. Identifying vulnerabilities in container images is a critical first step. By scanning container images for known vulnerabilities, organizations can assess their risk exposure and take appropriate actions.
B. Continuous vulnerability scanning and monitoring are essential for staying vigilant against emerging threats. Regularly scanning and updating container images helps maintain a secure environment.
C. Patch management is crucial to address identified vulnerabilities promptly. Organizations should adopt best practices for timely updates and fixes. This includes establishing a well-defined patch management process that ensures patches are tested, deployed, and verified efficiently across containerized environments.
D. Container runtime protection plays a vital role in vulnerability management. By utilizing runtime security tools, organizations can detect and mitigate vulnerabilities that may arise during container execution. These tools employ techniques like behavioral analysis, anomaly detection, and container introspection to identify and respond to potential threats.
Best Practices for Containerization Security
To strengthen containerization security, organizations should follow these best practices:
A. Implement secure container configurations by leveraging container security frameworks and adopting industry-standard security guidelines. This includes enabling security features like container image signing, enforcing least-privilege access controls, and utilizing secure defaults.
B. Employ strong access controls and authentication mechanisms to restrict container access to authorized personnel. Implementing multifactor authentication and role-based access controls helps minimize the risk of unauthorized container interactions.
C. Leverage container security platforms and tools that provide comprehensive visibility, monitoring, and threat detection capabilities. These tools assist in identifying potential security gaps, monitoring container behavior, and responding to security incidents effectively.
Container security platforms and tools are designed to enhance the security of containerized applications and the underlying infrastructure. They provide various features and capabilities to detect, protect, and respond to security threats in container environments. Here are some popular container security platforms and tools:
a.Docker Security Scanning: Docker Security Scanning is a feature provided by Docker that scans container images for known vulnerabilities. It analyzes the contents of the images and compares them against a vulnerability database, providing security advisories and recommendations.
b.Twistlock: Twistlock, now part of Palo Alto Networks, is a comprehensive container security platform that offers vulnerability management, runtime defense, compliance monitoring, and threat intelligence. It provides real-time protection and integrates with popular container orchestration platforms like Kubernetes.
c.Aqua Security: Aqua Security provides a container security platform that focuses on securing containerized applications from development to production. It offers image scanning, runtime protection, compliance monitoring, and secrets management to safeguard container environments.
d.Sysdig Secure: Sysdig Secure is a container security platform that provides runtime security, vulnerability management, compliance monitoring, and threat detection capabilities. It offers deep visibility into containerized environments and helps organizations identify and respond to security incidents.
e.Anchore: Anchore is an open-source container security tool that performs comprehensive image scanning and analysis. It detects vulnerabilities, enforces security policies, and ensures that container images meet the organization’s security requirements.
f.Falco: Falco is an open-source cloud-native runtime security tool. It uses behavioral rules and system call monitoring to detect abnormal activities and potential security threats within containers and the underlying infrastructure. Falco is often used alongside Kubernetes.
g.OpenSCAP: OpenSCAP is an open-source security framework that provides vulnerability scanning, configuration assessment, and compliance checking for container environments. It supports various container technologies like Docker and Kubernetes.
h.Trivy: Trivy is an open-source vulnerability scanner designed specifically for container images and operating systems. It can be integrated into the CI/CD pipeline to scan container images for known vulnerabilities and provide detailed reports.
These are just a few examples of container security platforms and tools available in the market. The choice of platform or tool depends on your specific requirements, the container environment you are using, and your organization’s security policies and practices.
D. Conduct regular security audits and assessments to evaluate the effectiveness of containerization security measures. Penetration testing, vulnerability assessments, and security code reviews help identify potential weaknesses and provide insights into areas for improvement.
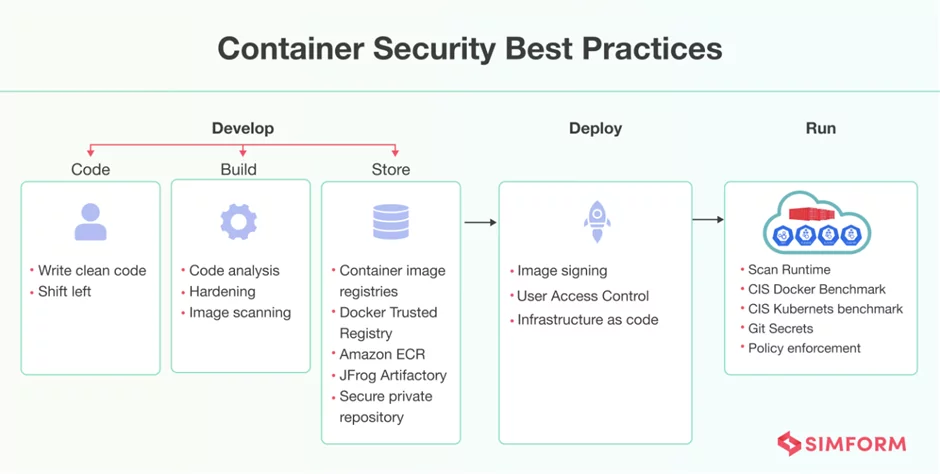
https://www.simform.com/blog/containerization-best-practices/
The Future of Containerization Security
A. Emerging Trends and Technologies in Container Security
The future of containerization security is marked by several emerging trends and technologies that aim to enhance the protection and resilience of containerized environments. These advancements are driven by the need to address the evolving threat landscape and ensure the integrity and confidentiality of containerized applications. Some key trends and technologies include:
Runtime Protection: The development of advanced runtime protection mechanisms specifically designed for containers is gaining traction. These solutions employ techniques such as behavior analysis, anomaly detection, and real-time monitoring to detect and mitigate threats during container execution.
Immutable Infrastructure: Immutable infrastructure refers to the practice of creating containerized environments that cannot be modified once deployed. This approach enhances security by reducing the attack surface and minimizing the risk of configuration drift or unauthorized changes.
Container-specific Security Tools: As containerization becomes more prevalent, specialized security tools are emerging to cater to the unique security requirements of containerized environments. These tools offer features like vulnerability scanning, image signing and verification, secrets management, and secure container orchestration.
Secure DevOps Practices: The integration of security into DevOps workflows is becoming crucial in containerization security. By implementing security measures throughout the software development lifecycle, organizations can ensure the secure deployment and continuous monitoring of containerized applications.
B. Anticipated Challenges and Opportunities
While containerization brings numerous benefits, it also introduces new challenges and opportunities for security professionals. Some of the anticipated challenges and opportunities in containerization security include:
Container Image Vulnerabilities: Ensuring the security of container images and their dependencies is a significant challenge. Vulnerabilities in base images or third-party libraries can pose a significant risk, requiring comprehensive vulnerability management strategies.
Orchestrator Security: Container orchestration platforms, such as Kubernetes, introduce their own security considerations. Securing the orchestration layer and effectively managing access controls and configurations are vital to prevent unauthorized access or malicious activities.
Compliance and Regulatory Requirements: Organizations must navigate compliance and regulatory requirements specific to containerized environments. This includes maintaining proper audit trails, ensuring data privacy, and adhering to industry-specific regulations.
Automation and Integration Opportunities: Containerization presents opportunities for automating security processes and integrating security tools into the container deployment pipeline. This allows for continuous security testing, vulnerability scanning, and seamless security enforcement.
Conclusion
Containerization security is a critical aspect of modern-day cybersecurity. By understanding and implementing effective isolation techniques, vulnerability management strategies, and best practices, organizations can safeguard their containerized environments from malicious threats. Prioritizing containerization security in a rapidly evolving threat landscape is essential for maintaining the confidentiality, integrity, and availability of containerized applications and data.
As organizations continue to embrace containerization, a proactive and comprehensive approach to security is imperative. By staying informed about emerging threats, leveraging industry best practices, and embracing technological advancements, organizations can ensure the secure adoption and deployment of containerized environments, safeguarding their critical assets in the ever-changing cybersecurity landscape.
Research, references & resources :
https://revdebug.com/blog/containerization-benefits-and-challenges/
https://middleware.io/blog/containerization/
https://kodekloud.com/blog/docker-containerization/
https://www.datadoghq.com/container-report/
https://www.bmc.com/blogs/state-of-containers/
https://portworx.com/wp-content/uploads/2019/05/2019-container-adoption-survey.pdf
https://portworx.com/wp-content/uploads/2019/05/2019-container-adoption-survey.pdf
https://snyk.io/blog/best-practices-for-container-isolation/
https://www.researchgate.net/publication/316602321_Understanding_Container_Isolation_Mechanisms_for_Building_Security-Sensitive_Private_Cloud
Illustrated guide to containerization security | TechTarget
16 Containerization Best Practices: Speed Up Your Application Delivery by 3X (simform.com)
https://blog.aquasec.com/container-isolation-techniques
https://docs.docker.com/desktop/hardened-desktop/enhanced-container-isolation/




