Bluetooth Vulnerability: Implications and Mitigations for Android, macOS, iOS, and Linux Devices
I.Introduction
Bluetooth has become an integral technology for billions of smartphones, computers, wearables, and other devices to connect and exchange data over short distances. With growing technology, it is also paving ways for the flaws that arise from it.
Recently a serious remote code execution vulnerability was discovered in Bluetooth Classic pairing which impacted – Android, iOS, macOS, and Linux devices.
According to 2023-24 figures, there were over 3.9 billion active Android devices, 1.3 billion+ iPhones, and tens of millions of Macs and Linux PCs vulnerable to this issue. Successful exploitation allows attackers to connect a fake keyboard or input device, remotely inject keystrokes, and take full control of target devices.
II.Breaking the Code: Understanding the Recent RCE Vulnerability in Bluetooth Technology
Operating in the 2.4 GHz band, Bluetooth uses short-range radio communication to transmit data over distances up to 100 meters.
The widespread dependence on Bluetooth makes it a prime target for cyber attacks. Several vulnerabilities have surfaced over the years that can be exploited to intercept traffic, track device locations, deny service, and gain unauthorized access.
Recently, a severe Remote Code Execution (RCE) vulnerability was disclosed by security researcher Marc Newlin of SkySafe. Tracked as CVE-2023-45866, the vulnerability enables attackers to remotely connect to Bluetooth-enabled Android, macOS, iOS, and Linux devices and control them by injecting keystrokes
This blog analyses the technical foundation of this vulnerability, outlining the extent of its impact, the significant security risks it represents for enterprises and individuals, along with mitigation strategies and recommendations
III. Bluetooth Vulnerability Technical Analysis
The Bluetooth vulnerability arises from flaws in the implementation of the Bluetooth Classic pairing process on affected devices. It allows an attacker to connect a fake keyboard or input device to the target system without authentication or user confirmation.
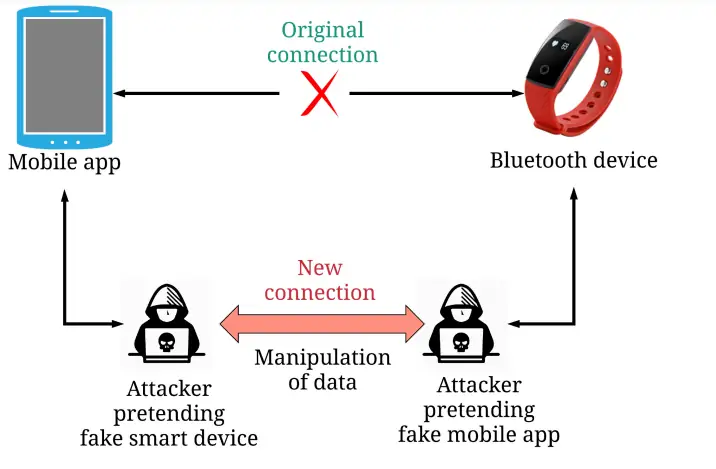
Man-in-the-middle-Attack ( MITM)
Bluetooth Classic pairing involves the following high-level steps:
1. Device Discovery – The two devices establish awareness of each other through scanning.
2. Link Key Generation – A link key is generated to authenticate and encrypt the connection.
3. Authentication – Using the link key, the devices validate each other’s identities.
4. Link Key Registration – The link key is stored for future authentication.
The vulnerability specifically bypasses above Steps 2 and 3, allowing the attacker’s device to connect without proper authentication.
IV.Technical Cause
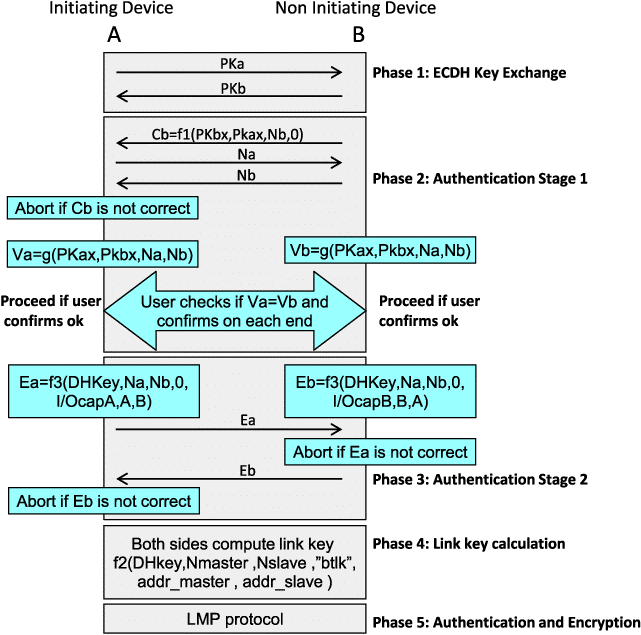
The root cause is improper validation of the Simple Secure Pairing (SSP) protocol by affected Bluetooth protocol stack implementations.
SSP is designed to strengthen Bluetooth Classic pairing relative to older methods like PIN-based pairing. It employs Elliptic Curve Cryptography to generate an initial encryption key. This key is then used to establish a secure connection between the two devices to subsequently exchange authentication tokens and derive the final link key.
However, flaws in the SSP validation process can allow unauthenticated connections to be established before the link key exchange occurs. By masquerading as a supported input device like a keyboard, an attacker can inject keystrokes over this insecure channel since the host Bluetooth stack fails to validate the authenticity of the connection.
V.Attack Methodology
To successfully execute the attack, an attacker simply needs a device with Bluetooth capability in proximity to the target system, along with standard tools like hcitool and bluez installed on Linux.
The steps involved are:
•Scan for discoverable Bluetooth devices in proximity using hcitool.
•Obtain the target device’s Media Access Control (MAC) address.
•Use the Bluez tool to initiate an SSP connection to the target as a Bluetooth HID (Human Interface Device) like a keyboard without valid authentication.
•Inject keystrokes over the unauthorized connection using another tool like Carnegie Mellon’s KeyKeriki.
This results in arbitrary code execution on the target device under the permissions of the logged in user or default Bluetooth privileges.
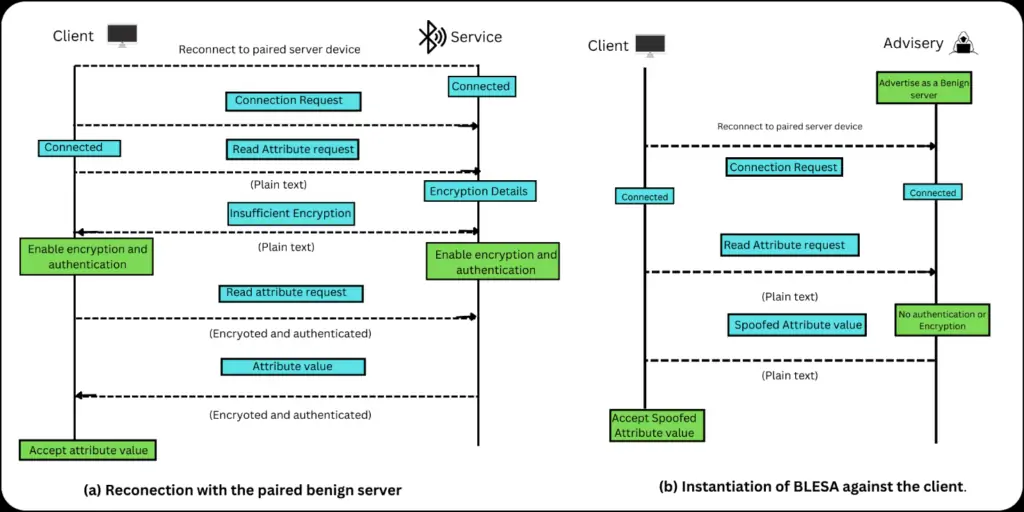
Spoofing Attacks against Reconnections in Bluetooth Low Energy
VI.Proof of Concept
Researcher Marc Newlin demonstrated the attack by developing proof-of-concept exploit code targeting Linux, Android, and iOS devices. He was able to remotely connect a fake keyboard and inject keystrokes to open a termina, land execute the id command to confirm access. The same method can be used to run any other command or install malware.
Newlin proved the vulnerability affected multiple Android versions, including 4.2.2, 6.0.1.10, 11, 13, and 14. On iOS, version 16.6 was confirmed exploitable, while macOS versions Monterey 12.6.7 and Ventura 13.3.3 were impacted. Linux distributions running BlueZ, including Ubuntu 18.04, 20.04, 22.04 and 23.10 were also vulnerable.
This demonstrates the wide impact of the vulnerability across current and legacy Bluetooth implementations.
VII.Extent of Impact on Operating Systems
Billions of devices running Android, iOS/iPadOS, macOS, and Linux could potentially be compromised by exploiting this vulnerability.
Android Devices
Any Android device with Bluetooth enabled is vulnerable. This encompasses over 3 billion active devices, according to Google’s figures. This includes phones, tablets, televisions, wearables, and various IoT gadgets with Bluetooth connectivity.
IOS Devices
All generations of iPhones, iPads, and Macs with Bluetooth enabled are susceptible.
Linux Devices
The Bluetooth protocol stack implementation in Linux, BlueZ, is affected across multiple popular distributions. Debian-based distributions like Ubuntu make up the largest segment of Linux desktops and servers. Enterprise IoT devices and industrial systems running embedded Linux are also at risk.
Windows and ChromeOS
Microsoft and Google indicate that Windows and ChromeOS are not vulnerable as their Bluetooth stack implementations perform appropriate SSP validation.
VIII.Security Implications for Enterprises and Individuals
The Bluetooth vulnerability represents a serious threat with the potential for large-scale exploitation. Attackers can leverage it to circumvent authentication systems, gain persistent remote access, and control devices without the owner’s knowledge.
Some notable security risks include:

IX. Mitigation Strategies and Recommendations
Enterprises and individuals should adopt a combination of measures to minimize the risk of attacks leveraging this Bluetooth vulnerability:
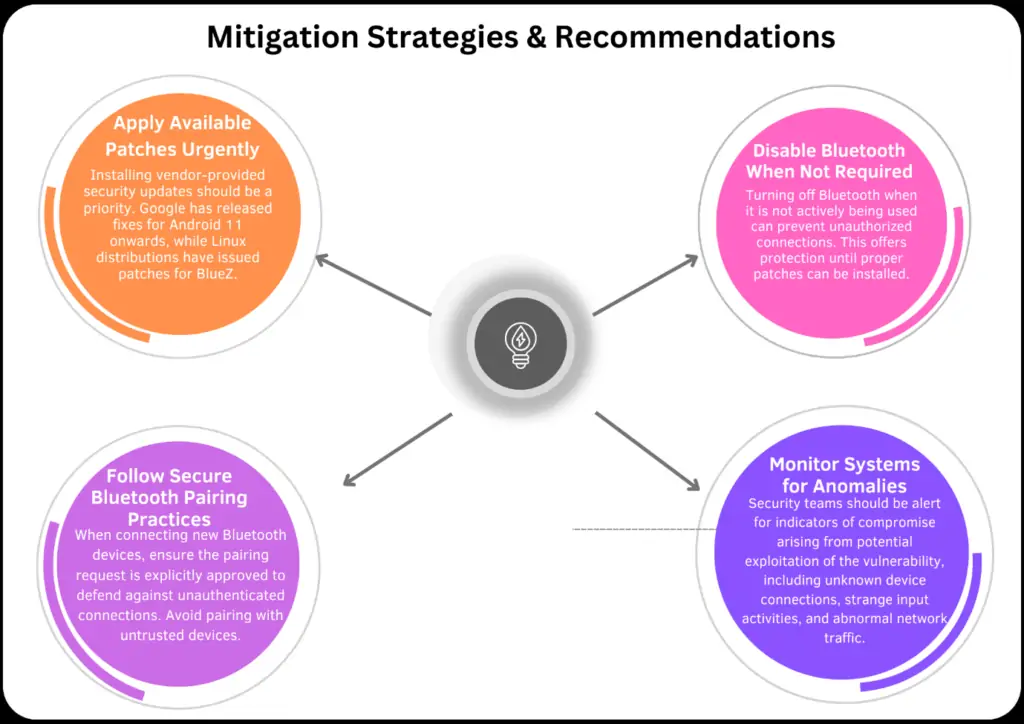
X.Adopt Comprehensive Security MeasuressXI.Demand Vendor Accountability
Organizations should press upon device manufacturers and vendors to provide timely security fixes and transparency around vulnerabilities. Procurement policies should include security criteria.
XII. The Need for Enhanced Bluetooth Security
While the discovered vulnerability results from specific implementation flaws, it highlights that the Bluetooth specification itself lacks adequate authentication mechanisms. The ability to pair peripherals without any user confirmation or consent presents an inherent risk.
The Bluetooth Special Interest Group (SIG) responsible for defining the core Bluetooth standards should aim to restrict unauthenticated connections in future revisions of the specification.
XIII. Some improvements that can be incorporated:
•Make user confirmation mandatory for all pairing connections.
•Introduce cryptographic signing of authentication messages.
•Enforce encrypted connections prior to any data transfer.
•Define uniform security requirements and validation criteria for all platform implementations.
Adopting these measures would disallow the possibility of random unauthenticated device connections and improve Bluetooth security overall.
XIV. Role of Vendors and Security Researchers
While standards improvements will take time, device vendors and software developers can act now to enhance their Bluetooth implementations:
•Perform rigorous security analysis of protocol stack code and fix flaws.
•Implement safeguards like PINPairing and link key verification.
•Provide timely fixes and transparency for vulnerabilities.
•Adopt secure development best practices like threat modeling, fuzz testing, and red teaming.
Continuous scrutiny helps detect issues early before exploits become widespread. It allows vendors to mitigate risks quickly by releasing security patches.
XV.Conclusion
The Bluetooth vulnerability CVE-2023-45866 represents a serious threat to billions of devices across multiple operating systems. An attacker can obtain complete device takeover and remote code execution by tricking Bluetooth implementations into unauthenticated pairing.
To mitigate risks, enterprises should apply available patches urgently, follow secure Bluetooth practices, monitor for threats, and adopt comprehensive security measures. While standard improvements will take time, vendors need to enhance their Bluetooth implementations and address vulnerabilities promptly.
Ongoing security research and responsible disclosure are crucial to revealing underlying risks in protocols and software. With collaborative efforts across vendors, standards bodies, and the cybersecurity community, Bluetooth security can be substantially strengthened against emerging threats.
Image references
Image 1 : https://ieeexplore.ieee.org/stamp/stamp.jsp?arnumber=9706334
Image2: https://www.researchgate.net/figure/Bluetooth-Secure-Simple-Pairing-with-numeric-comparison-12_fig2_340356923R
Research & references :
https://blog.bugzero.io/exploiting-a-bluetooth-vulnerability-to-hack-linux-macos-ios-and-android-bd15e1a8905d
https://www.csoonline.com/article/1291144/magic-keyboard-vulnerability-allows-takeover-of-ios-android-linux-and-macos-devices.html
https://www.spiceworks.com/it-security/endpoint-security/news/bluetooth-vulnerability-mac-ios-linux-android/
https://thehackernews.com/2023/12/new-bluetooth-flaw-let-hackers-take.html