Android Weak Host Validation

In this blog we are going to discuss about android weak host validation and see how android application is not validating weak host for the android apps.
Requirements:
- ADB (Android Debug Bridge)
- JADX (Android Decompiler)
- Android Emulator (Genymotion)
For the testing purposes, we are using InsecureShop vulnerable android application.
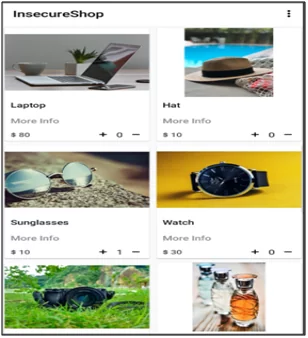
Fig1: Post login interface
First, we need to decompile insecureshop.apk in the JADX decompiler. In the below screenshot, we can see the source code of the insecureshop android application.
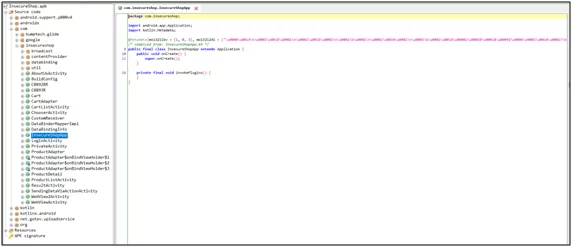
Fig2: Source code of insecureshop
Check for the androidmanifest.xml file. There you will have to look for the structure and components of the application. Also, look for the exported activity permissions provided by the developers in the source code of the application.
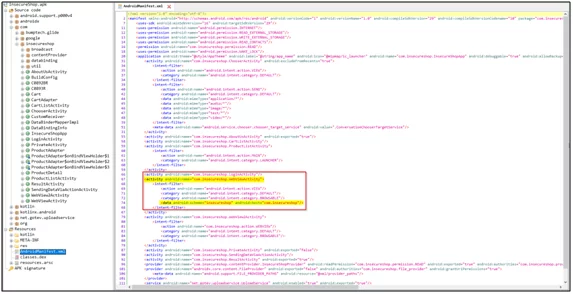
Fig3: Androidmanifest.xml
In the fig3: androidmanifest.xml screenshot, you can see there is an activity that is used as “<activity android:name=”com.insecureshop.WebViewActivity”>”
What is Activity?
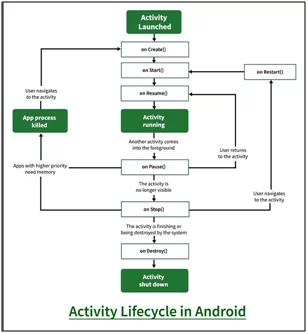
An Activity is a single representation in an app. Pass the intent to startActivity() and begin your new Activity. The intent is an Activity that has to be started to carry the essential data. You can also visit developer.android.com for more details.
In the following diagram, you can see the important state paths of an Activity. The callback methods are represented by a colorless rectangles dialog box. When an Activity is transferred between states it will be used for implementation to perform operations. The colored boxes represent the major states of the Activity.
Check the deep link for an activity in the image below
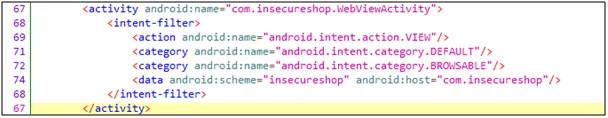
Fig4: Deeplink in androidmanifest.xml
- Intent-filter: It can be defined as the capability of an activity component that is based on the type of URI.
- <action> Specify the ACTION_VIEW intent action. This procedure is carried out so that any search engine like Google, DuckDuckGo, or more can reach out to intent filter anytime.
- <category> Include the BROWSABLE category. It is required as it will ensure that the intent filter gets accessible from a web browser. Without it, just clicking on the link that was opened in the browser won’t be resolved to your app.
- Also, include the DEFAULT category. It allows the app to respond to implicit intents. Without it, the activity can’t be started until intent specifies your app component name.
- Additional <data> tags are to be added as they represent a URI format that revolves around the activity. It is recommended that the <data> tag is to be included in the android:scheme attribute.
In the figure below, you can see that deeplink invokes webview by looking at the android activity name. You can also visit the blog to know more about webview.
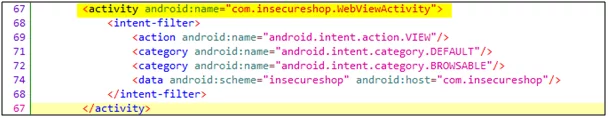
Fig5: WebViewActivity in androidmanifest.xml
In Jadx, to open the code in a new tab, you will have to press hold the ctrl key and click on the activity name.
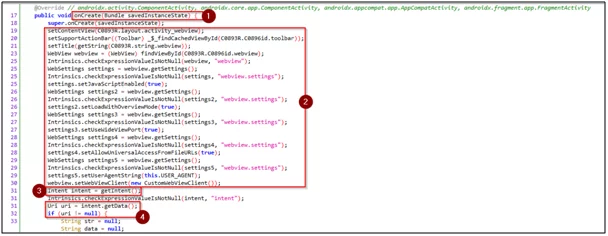
Fig6: Webview activity source code
- onCreate() is a life cycle event that is found in Android. There are 6 core set of life cycle events in Android’s activity lifecycle, i.e., onCreate(), onStart(), onResume(), onPause(), onStop(), and onDestroy().
- webview settings for the defined webview activity.
- getIntent() fetches the intent and stores it in the intent object.
- intent.getData() fetches the URI and stores it in the URI object. It then checks if the URI is empty.
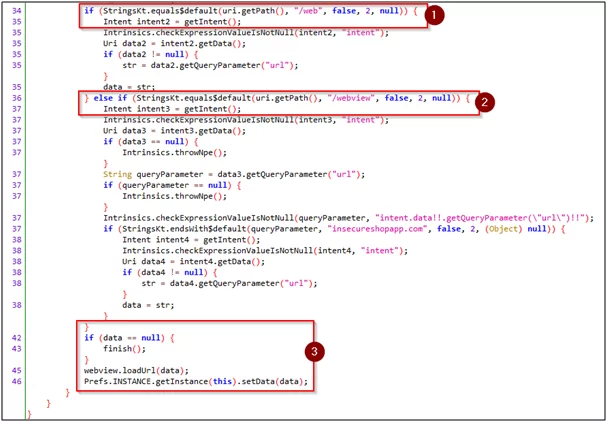
Fig7: Webview activity source code – 2
- We have two paths in the code it has /web or/webview in it. Then, accordingly, it executes the respective code.
- finish() means if both checks fail. Now, webview will not be loaded.
- If 1 or 2 passes the request, it will fetch the URI and extract the value from the URL query. Then, it will store it on data variables and will be loaded via webview.
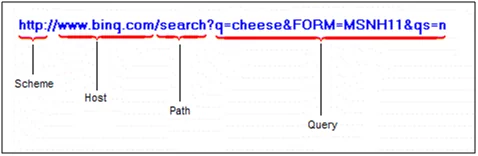
Fig8: URI format
Let’s try to exploit this vulnerability, we have made one payload based on URI format to load the arbitrary web page in the webview.
“insecureshop://com.insecureshop/webview?url=https://varutra.com/ \?insecureshopapp.com”
We will be using ADB to launch webview activity by passing URI as data to it. The command used for exploiting is: adb shell am start -W -a android.intent.action.VIEW -d “insecureshop://com.insecureshop/webview?url=https://varutra.com/\?insecureshopapp.com”.
You can see that Webview loads the arbitrary URI:
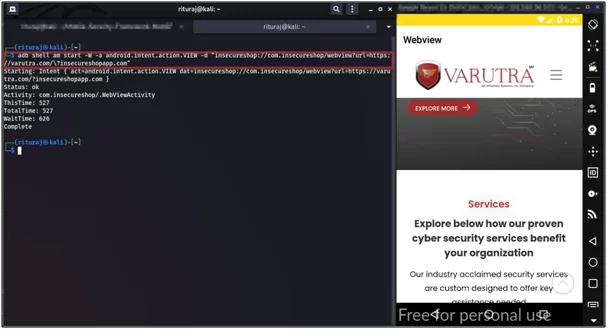
Fig9: Arbitrary URI is loaded in webview successfully
References:
- https://www.youtube.com/watch?v=VfyuZIvLX8Y
- https://labs.f-secure.com/archive/adventures-with-android-webviews/
Author,
Rituraj Vishwakarma
Attack & Pentest Team
Varutra Consulting Pvt. Ltd.