Why Ongoing Vulnerability Assessments Are Key to a Sound Security Posture?

Cybercriminals are very smart and continuously looking for opportunities to exploit any possible vulnerability they can find. In 2021, more than 50 vulnerabilities were logged daily, as per a report by Redscan. In addition, there has been a significant increase in malware, DDoS, ransomware, and other types of cyber-attacks. More than 90% of malicious cyber activities were carried out last year by hackers with less technical expertise. Therefore, organizations need to build and manage a reliable security posture in these circumstances. In other words, organizations need to adopt a proactive approach to address the vulnerabilities, and one of the primary steps to achieve this is to perform a vulnerability assessment.
What is a Vulnerability Assessment?
As a human, it is common to make some errors and mistakes. It means if we create an application, it may sometime contain bugs. These bugs can be problematic as any cybercriminal can exploit these, and the organization can be at risk. This situation can be avoided through a vulnerability assessment. It scans and analyzes the system for any vulnerabilities that hackers can exploit.
Source: silentbreach
Vulnerability Assessment and Penetration Testing (VAPT)
Vulnerability Assessment and Penetration Testing, generally known as VAPT, are two different types of Technical Security Risk Assessment. So, it can be said that the functions of vulnerability assessment and penetration testing are different, but they show different results and have the same focus area.
In the vulnerability assessment process, the tools will detect any vulnerabilities that are already existing in the system. While assessing the vulnerabilities, it may not be possible to differentiate between the bugs that can cause damage to the system and those that will not. The vulnerability scanners will quickly detect the pre-existing defects that were already present in their infrastructure/codes and their location, then report it to the organization. While in penetration testing, a tester has to identify vulnerabilities by exploiting them manually. It is done to determine the extent of damage these vulnerabilities may carry out, like giving unauthorized access or other malicious activities. Then, it tries to identify what poses a threat to the system or any application.
Source: researchgate
How Does Vulnerability Assessment Work?
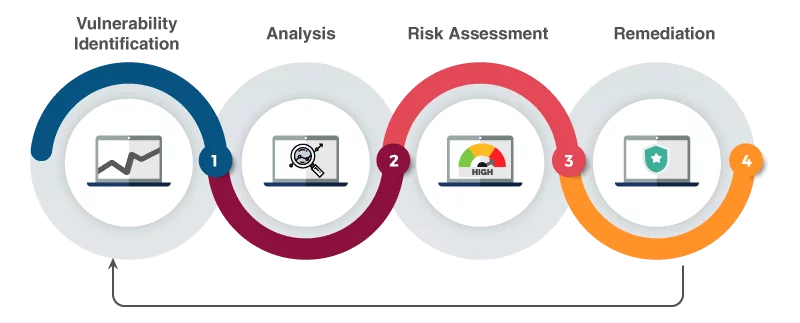
Here are the five steps that are included in the vulnerability assessment process.
- Identifying the vulnerabilities that can be exploited.
- Perform vulnerability analysis where the vulnerability’s source, root cause, and impact are analyzed.
- Check the level of risk the vulnerability possesses. It is identified based on severity score and is known as risk assessment.
- The security gaps are now patched using various methodologies like virtual patching, debugging, configuration, etc.
- The vulnerability assessment process is concluded by generating a report with complete details regarding the procedure.
Why the Vulnerability Assessment is a Key to a Sound Security Posture?
Here are some points which will explain why the vulnerability assessment is key to a sound and reliable security posture.
Providing Insights Regarding Security Risks
For a safe and sound security posture, an organization should adequately understand the cybersecurity risks they face. These threats and risks fluctuate from time to time. Therefore, one can never be sure what type of attack they may encounter. So, performing vulnerability assessments at regular intervals will help provide real-time scan reports. If vulnerabilities are found, they can be mitigated in time before they can cause more significant damage.
Exposes Security Gaps, Misconfigurations, and Vulnerabilities in the System
By utilizing the vulnerability assessment tools, deep and intelligent scans are performed to detect any vulnerabilities. These automated scanning tools speed up the procedure and provide flexibility, agility, and accuracy while scanning and looking for new areas to crawl to discover any possibility of bugs. It helps an organization identify any misconfiguration, unknown vulnerabilities, and flaws.
Finding Any Cracks in the Armor
While vulnerability assessment is performed, the organization can evaluate its security defenses for cracks or gaps. This way, they can strengthen their defenses and ensure their infrastructure, critical assets, and sensitive data are secured. In addition, it will help the organization increase the efficiency of its security systems.
Helping in Understanding the Impact of Vulnerabilities
The work of vulnerability assessment is not only to identify but also to help with prioritization and vulnerability analysis. When this proves is going on, the organization will get insight into the vulnerabilities and their impact if any hacker exploits it. They can utilize the time to harden their security and modify their IT infrastructure to prevent any security risks and threats. This way, they can maintain a sound security posture.
Creating a New or Updated Assets Inventory and Prioritizing Business-Critical Assets
An organization should always keep track of its assets. While vulnerability assessment is performed, an organization needs to update its asset inventory. They will get real-time visibility on the attack surface and identify the exposed and vulnerable areas to attacks. This way, they can work on how to reduce their attack surface. In addition, the organization will understand its standing regarding the condition of its assets and its purpose. This way, they can categorize the assets and prioritize them. This way, they can make efforts toward their business-critical assets and create an updated inventory of assets.
Enables Agile Strategy and Decision Making
An ongoing vulnerability assessment provides real-time insights and a detailed report when it is complete. It will help the organization make a smart decision at the right time and form intelligent strategies to prepare themselves by creating incident response plans. This way, they can have a better and more robust security posture. So, it can be rightly said that cyberthreats and risks constantly fluctuate and need regular monitoring.
Conclusion
Organizations should always be vigilant and ensure that they have a good security posture. So, it is necessary to conduct vulnerability assessments regularly as it helps the organization understand its security posture. This way, they will know what risks they face and look for means to mitigate them.
Reference:
https://www.forbes.com/sites/forbestechcouncil
Author,
Sanjana Yadav,
Marketing Department,
Varutra Consulting Pvt. Ltd.




