HIPAA Compliance Framework – A Guide for Implementation

The Health Insurance Portability and Accountability Act (HIPAA) has set the standard for sensitive and critical patient healthcare data protection. Organizations that handle protected health information (PHI) should have appropriate physical, network, and administrative security measures and controls in place and follow them as per the regulatory guidelines to ensure HIPAA Compliance. According to the U.S. Department of Health and Human Services (HHS), the HIPAA Privacy Rule has established national standards for protecting and safeguarding certain health information. In addition, the Security Rule defines a national set of security standards and frameworks for protecting and safeguarding specific health-related information that is stored or transferred in electronic form.
Covered Entity
A Covered Entity can be anyone who is a health care service provider, platform provider, etc. Hospitals are a major part and very common category of the slot that is at the central part of the process for handling patient-related data and reports. It is mandatory as a part of the process for the Covered Entity to be HIPAA compliant to avoid regulatory fines and impositions. The covered entity must implement all the safeguard controls and processes to ensure HIPAA Compliance.
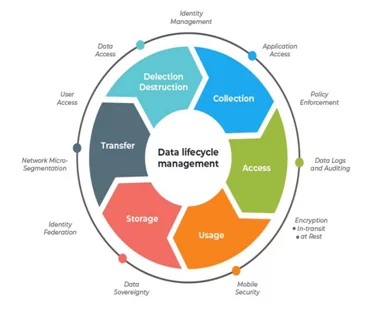
It is a must requirement to analyze, document, and exercise the security controls in accordance with the Privacy Policy for the PHI Lifecycle Management. It is required by the covered entity to have a detailed inventory of all the PHI and PII data that is being collected. The covered is required to be well adverse with the fact of the points of from where the e-PHI data is getting collected, the identification of the point of collection is important to ensure and enforce policies that will make sure that the covered entity is not collecting data that it is not legally authorized to do so. From the point of collection to the point of Transmission, Storage, Processing, and Deletion of the Data are also equally important to identify and document from the HIPAA compliance perspective.
Business Associate
A Business Associate is a person who has been providing services to the covered entity. The Business Associate can be anyone who provides services like IT – Communication or vendor outsourced services required by the covered entity.
It might be in the form of a food vendor or a stationary vendor who can provide all the required stationary of the hospital or health care service provider agency. These are the service providers who are from a non-medical background and provide non-medical services required by the hospital to perform their operations smoothly.
It is often seen that the covered entity usually outsources its process to a third-party service provider who then assists the covered entity by providing the desired service. Any entity that is involved in the Data Lifecycle Management process for the ePHI data and the PII data will be termed as a Business Associate. It is mandatory for the Business Associate to determine their point of share for the Data Life Cycle Management Process and implement controls accordingly.
What are the HIPAA Compliance Requirements?
As per the HIPAA requirements, every covered entity or any business associate that has access to the PII or the EHR data of patients or data regarding the private reports of the hospitals must comply with the Technical, Administrative, and Physical Safeguards as mandated by the HIPAA council.
A high level of risk assessment focusing on data privacy must be performed in a detailed manner to identify the risks that are associated with the PII data and the access to the patient health care data. This risk assessment should be monitored on a regular basis to identify the risk and implement the assurance controls that will mitigate the risk factors. The asset value is to be determined as per the classification of the assets and the associated threats to these assets are to be identified. These factors should be taken into consideration and the vulnerabilities across the threat pair should be identified and associated actions should be taken for minimizing the risk factor.
Technical Safeguards
Technical safeguards are the technical specifications mandated by the HIPAA to be implemented. In terms of the Technical Safeguards, the access control mechanism, authorization controls, incident management and other controls mandated in detail by the Technical Safeguards are to abide by and the control should be monitored on a regular basis to ensure that there are no gaps or non-conformance in the system.
The data security is the major concern in this aspect and technical controls should be implemented to cover the data security and privacy for Data at rest and data in motion. Encryption of devices and data is advised in such instances to ensure that the risks and associated threats are mitigated.
Physical Safeguards
Physical Safeguards are specified by HIPAA regarding the Physical Security of the perimeter in which the PII or e-PHR data is hosted. Physical safeguards consist of physical measures, procedures, and policies that help to secure a covered entity’s information systems and related equipment and buildings from unauthorized intrusions and natural as well as environmental hazards. The security measures include CCTV installation, monitoring of entry and exit points of the organization premises, and many other things. Physical safeguards include a wide and vivid variety of controls to be applied from the physical security perspective.
Administrative Safeguards
Administrative safeguards are to be implemented as prescribed by the HIPAA council. Administrative Safeguards highlight the major requirements to have a policy and procedure in place that will ensure the implementation of controls. The associated policies and procedures are to be defined, reviewed, and approved by the senior management of the organization and further controls can be implemented based on these administrative safeguards.
Infrequent risk assessments are the major cause of the non-compliance as per the HIPAA council, and this has to be addressed on priority to ensure that the risks are controlled and will not cause a threat to the organization.
HIPAA Compliance Privacy Rule
The HIPAA Privacy Rule states that how the e-PHI data will be shared on what basis and norms. It has been clearly identified by the HIPAA norms the grounds on which the critical data will be shared. The e-PHI data has been associated with the covered Entity and the Business Associate, and HIPAA has laid down the rules and regulations regarding these entities managing and holding the e-PHR data.
Moreover, HIPAA has added details on how the data will be consumed and shared between the channels by the covered entity and the Business Associate. The Rules and Regulations further state that patients can request the Covered Entity or the Business Associate for a copy or a duplicate of the data stored by these parties with them, also the patients can request a change or correction in the
data handled by these process units. Also, the Covered Entity and the Business Associate need to confirm back or take appropriate action on these points within 30 working days.
Covered entities further need to ensure the below things:
- Provide Security Awareness Training to their employees regarding the security architecture and posture of the organization.
- Ensure that the required steps are being taken by the organization to check the integrity of the data being handled by them.
- They are obtained by written permission from the patients or the data owners to store and process their data.
The HIPAA Compliance Breach Notification Rule
In case if the Covered Entity suffers a potential breach of data, the Covered Entity is responsible and accountable for contacting the stakeholders (patients and the HIPAA Council) and brief them about the status of the data breach, and determine its severity and steps being taken to minimize the damage associated with the data breach. Such data breaches are further analyzed, and the HIPAA Council may impose certain restrictions on the Covered Entity and the Business Associate if they are found guilty of the data breach.
Hence, it is required by the Covered Entity and Business Associate to implement processes and controls in a manner that has been approved by the HIPAA Compliance – Technical – Administrative and Physical Safeguards. Further, regarding these incidents, a detailed Root Cause Analysis is to be done and shared with the Council for the Preventive and Curative measures taken.
Breach notifications must include the following information in detail:
- The nature of patient health information that has been breached
- Unauthorized access control for the data if being done – with a detailed RCA
- Was the e-PHI data record copied, backed up, or just was shoulder surfed?
- Risk Assessment of the current scenario for the data breach
It is mandated by the HIPAA Council that the Covered Entity and the Business Associate has to send a detailed report and keep the affected patients informed on a timely basis with reference to the data breach activities. This process is to be initiated within 60 days from when the Incident has taken place.
HIPAA Omnibus Rule
The Omnibus Rule has been amended by the HIPAA Council and the US Federal Reserve in order to extend and cover the regulations regarding the Business Associate and the third-party sub-contractors. This term broadly covers the agencies that provide supporting utilities and assistance to the Covered Entities. These might include, on a broader scale, IT Support, Data Centre Support, Data Storage, and Compliance Support.
The Omnibus Rule amends HIPAA regulations as described below in detail:
- The Final Amends and regulations proposed by the HITECH should be implemented
- Penalty as per the Penalty Structure finalized by the HITECH Penalty Structure
- Amend Policies and Procedure to include that the data breach has to be notified to the HIPAA Council
- The e-PHI data must not be used for marketing purposes
The term ‘Business Associate’ and ‘Workforce’ had definition changes. Now, the workforce includes volunteers, employees, and trainees. Also, the nature of PII which is classified as PHI was updated.
Following the HIPAA Omnibus Rule, to be HIPAA compliant, Covered Entities must now:
- Update Business Associate Service Level Agreements (the old and archived SLAs are to be restructured). These new SLAs now have to include the recent amends from the last Omnibus Rule, that highlight the cause and inclusion for the Administrative, Technical and Physical Safeguards of the PII data, while the administrative safeguards focus on implementing controls by approving a formal policy and procedure document. These policies and procedures are to be reviewed for changes on a periodic basis. The controls regarding the Technical and Administrative parts should be implemented to comply with the regulations and send a detailed report on compliance to the Covered Entity.
- To issue and sign new Business Level Service Agreements before onboarding the third party for their services with the Covered Entity.
- The Privacy Rules to be updated- The Privacy Rules and regulations must be updated and revised for the changes in the regulations that will mandate the requirement of restricting the use of the e-PHI data openly. The data will be authorized to be accessed by the responsible person only and selling this crucial and critical data must be restricted as per the law.
- Update Notices of Privacy Practices – The Privacy Practices are to be updated to cover the type of information that will require authorization.
- Train staff – Security Awareness Training is to be provided on a regular basis.
HIPAA Enforcement Rule
The HIPAA Enforcement Rule focuses majorly on the investigations that are mandatory to be carried out and they may face hefty fines and impositions in case they fail to abide by the HIPAA Enforcement Rule. It is further mandatory to have a proper policy and procedure for incident management.
Below we can see the fines that are imposed on the covered entity in case of lapses in the system to comply with the regulation.
- A violation of attributable to ignorance is liable for a fine of $100 – $50,000.
- A violation committed despite reasonable vigilance being in place will be liable for a fine of $1,000 – $50,000.
- A violation committed due to negligence and was corrected within 30 days will attract a fine of $10,000 to $50,000.
- A violation that occurred due to negligence and was not corrected within 30 days will attract the maximum fine of $50,000
The HIPAA council imposes penalties as per the category and nature of the data breach that occurred. Also, it often considers the actions being taken by the covered entity and the business associate to tackle and handle the situation. The risk factor is also considered while imposing the fine on the covered entity, the risk associated with the PII data that has been breached is also calculated. The penalties can vary and a maximum of $1,50,000 can be charged for every violation per year.
The financial violations are followed up by any civil and criminal charges that might be filed against the covered entity and the business associate by the victims of the data breach.
The organizations and entities or business associates that are very commonly subjected to the enforcement action and impositions are private medical practitioners, hospitals, and outpatient facilities such as pain clinics or rehabilitation centers, insurance groups, and pharmacies. The very common disclosures to the HHS are presented as:
- The entity might have misused the PII and not maintained authorization.
- Proper protection mechanism might not have been placed in the unit for protecting the PII data.
- There might be certain unavailability due to which the patient might not be able to access the PII data.
- The PII data is disclosed to the third parties on a larger scale than that has been approved by the council.
- Lapses by the institution to have a proper mechanism in place for administrative and technical safeguards.
Mandates regarding the HIPAA Risk Assessment
The HIPAA Council has also stated the objectives and tasks associated with the Risk Assessment Activity. It clearly identifies and states the level of assessment matrix to be implemented in order that the risk factors are handled properly. Mandates regarding the risk assessment are:
- The Covered entity needs to identify the PII data and e-PHR data the organization creates; it needs to administer the risk when the data is in motion or data is at rest.
- Factors that are responsible for generating the risk, for example, internal factors, organizational factors, internal threats, and external threat agents should be considered while performing the risk assessment.
- The threats that may have a high impact probably on the data associated with the e-PHR should be monitored to ensure that there are sufficient parameters in place to handle the risk elements.
- The business impact analysis or the analysis should be done by the covered entity to evaluate the process in place to ensure that the e-PHI will not be affected as a result of the data breach
- The policies and the procedure should be documented and made available as per the hierarchy or access related to the people.
References
https://digitalguardian.com/blog/what-hipaa-compliance
Author,
Omkar Gaikwad
Audit and Compliance Department
Varutra Consulting Pvt. Ltd.




