The Benefits of SEBI Security Audit and Governance: Safeguarding Investors’ Interests
Introduction
In an increasingly interconnected world, the financial industry is becoming more vulnerable to cyber threats and attacks. As a result, it has become crucial for regulatory authorities to ensure that the securities market remains resilient and secure against these threats.
The Securities and Exchange Board of India (SEBI) has recognized the importance of safeguarding the integrity of data and protecting the interests of investors. To achieve this, SEBI has introduced a comprehensive framework for cybersecurity and mandates security audits for market intermediaries and listed companies. In this blog post, we will explore the SEBI Security Audit and the Cyber Security Framework, shedding light on the benefits they offer and their critical role in safeguarding the Indian securities market.

Understanding SEBI Security Audit and the Cyber Security Framework
SEBI Security Audit: A Necessity for Market Intermediaries
The SEBI Security Audit is a critical component of SEBI’s cybersecurity framework, designed to protect the Indian securities market from cyber threats. SEBI, as the regulator for the securities market in India, has introduced this audit to ensure that market intermediaries and listed companies implement robust cybersecurity measures. It is a proactive approach to enhance market resilience and safeguard the rights of investors.
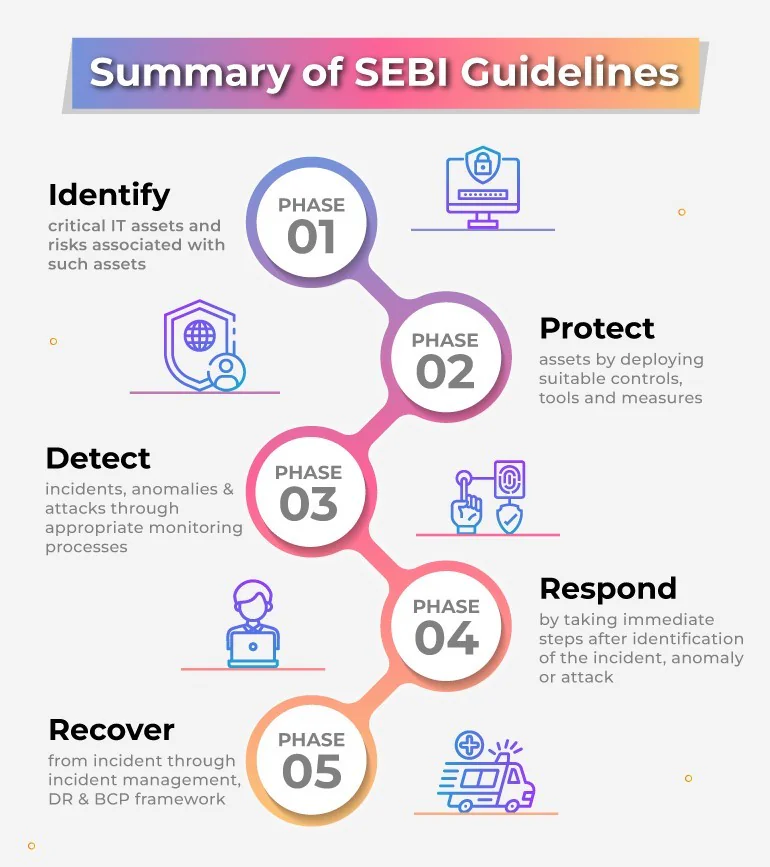
Cyber Security Framework: Building Resilience
The SEBI Cyber Security Framework, outlined by SEBI in its circular SEBI/HO/MIRSD/CIR/PB/2018/147 dated December 03, 2018, focuses on improving the cyber security and cyber resilience of stockbrokers and depository participants. This framework applies to all data created, received, or maintained by these entities during their operations, regardless of the form or location of the data.
Applicability
All stockbrokers are mandated to conduct an audit and ensure compliance with the guidelines outlined by SEBI. This audit is to be carried out by a Certified Information Systems Auditor (CISA).
The Objectives of SEBI System Audit
• Monitor stock exchange activities for data integrity and privacy.
• Protect investors’ rights.
• Maintain a strong cybersecurity framework as per SEBI guidelines.
• Ensure compliance with SEBI guidelines and Terms of Reference (ToR).
• Combat fraud using a balanced approach of regulations and self-regulation.
The Four Phases of SEBI System Audit:
The SEBI System Audit, with its four distinct phases, is a comprehensive process designed to evaluate an organization’s cybersecurity posture and ensure adherence to SEBI guidelines. It plays a crucial role in enhancing cybersecurity, protecting investor interests, and maintaining the integrity of the financial systems in India.
a.Audit Planning:
The first phase of the SEBI System Audit involves meticulous planning to ensure a systematic and effective audit process.
Identification of Scope:
Auditors determine the scope of the audit by defining the systems, processes, and assets to be examined. This can include hardware, software, networks, and specific business processes.
Resource Allocation:
Auditors allocate necessary resources such as personnel, tools, and technology for the audit.
Audit Strategy:
A well-defined audit strategy is developed, outlining the audit approach, objectives, and criteria to be evaluated.
Documentation:
All necessary documentation, including audit plans, checklists, and procedures, is prepared during this phase.
b. Risk Assessment and Business Process Analysis:
This phase focuses on assessing potential risks to information security and understanding the critical business processes.
Risk Identification:
Auditors identify potential risks to the organization’s information systems and data. This includes external and internal threats, vulnerabilities, and possible attack vectors.
Risk Assessment:
Each identified risk is assessed for its potential impact on the organization. This process helps prioritize risks based on their severity and likelihood.
Business Process Analysis:
Auditors examine key business processes, including data flow, access controls, and dependencies. This analysis helps in understanding how security measures impact daily operations.
c. Audit Performance (Compliance and System Review):
This phase involves the actual evaluation of the systems and processes to ensure compliance with SEBI guidelines and a comprehensive system review.
Compliance Review:
Auditors assess whether the organization complies with SEBI’s cybersecurity guidelines. They check if the recommended security measures are in place.
System Review:
Auditors perform a thorough review of the organization’s information systems, infrastructure, and policies. This includes examining technical controls, security configurations, access controls, and data protection mechanisms.
Vulnerability Assessment:
Auditors may use vulnerability scanning tools to identify vulnerabilities within the systems. This includes identifying weak points in networks, applications, and configurations.
d. Reporting:
The final phase involves preparing and presenting a detailed report that includes audit findings, recommendations, and potential areas of improvement.
Audit Findings:
Auditors compile a list of findings, including any non-compliance issues, vulnerabilities, and weaknesses discovered during the audit.
Recommendations:
Auditors provide actionable recommendations to address the identified issues. These recommendations may include technical changes, process improvements, or policy adjustments.
Report Preparation:
A comprehensive audit report is prepared, detailing the audit process, objectives, findings, and recommendations.
Presentation:
Auditors present the findings and recommendations to the organization’s management and stakeholders. This presentation ensures that all relevant parties understand the audit results and the path forward.
SEBI’s Role in Cyber Security
SEBI plays a significant role in ensuring the cybersecurity of the securities market:
Regulatory Framework:
SEBI establishes and maintains a regulatory framework that outlines guidelines and regulations related to technology and cybersecurity in the securities market. This framework sets the standards for ensuring the integrity, confidentiality, and availability of data and systems.
Cyber Security and Market Infrastructure Institutions:
SEBI mandates stringent cybersecurity measures for market infrastructure institutions, including stock exchanges and depositories. Guidelines are in place to secure trading systems, protect data, and enhance the resilience of critical market infrastructure against cyber threats.
Incident Reporting and Response:
SEBI requires market participants to promptly report any cybersecurity incidents or breaches. This ensures that timely action can be taken to investigate, contain, and respond to cyber threats effectively. SEBI may also provide guidelines for incident response and recovery.
Cyber Security Audits:
SEBI conducts or mandates cybersecurity audits for market intermediaries and infrastructure institutions. These audits assess the effectiveness of cybersecurity measures, identify vulnerabilities, and ensure compliance with regulatory standards. Recommendations for improvements may be provided based on audit findings.
Risk Management:
SEBI emphasizes the importance of risk management practices in cybersecurity. Market participants are encouraged to conduct periodic cybersecurity drills and simulations to test their readiness to respond to cyber threats. This proactive approach enhances the overall cybersecurity posture of the securities market.
Key Elements of SEBI Security Audit
• Hardening of Hardware and Software:
Ensure secure hardware and software deployment, strong passwords, and network protection.
• Application Security in Customer Facing Applications:
Implement robust security measures, especially for publicly accessible customer-facing apps as per SEBI guidelines.
• Certification of Off-the-Shelf Products:
Core products must have Indian Common Criteria Certification; custom software undergoes rigorous testing for security and compliance.
• Patch Management:
Establish procedures for patch identification, categorization, and prioritization; testing ensures updates don’t disrupt systems.
• Disposal of Data, Systems, and Storage Devices:
Enforce secure disposal policies for storage media, identifying data value and lifetime.
• Vulnerability Assessment and Penetration Testing (VAPT):
Conduct regular assessments and yearly penetration tests; report and remedy vulnerabilities in off-the-shelf products or vendor apps.
• Monitoring and Detection:
Implement security monitoring for unauthorized activities and changes; monitor logs for timely attack detection.
• Response and Recovery:
Investigate alerts, prevent cyberattacks, mitigate effects, and adhere to recovery plans defining responsibilities, RTO, and RPO.
• Sharing of Information:
Share quarterly reports on cyberattacks, threats, and mitigation measures to enhance industry-wide cybersecurity.
• Training and Education:
Build cybersecurity awareness through periodic training programs for both technical and non-technical staff.
• Systems Managed by Vendors:
Ensure vendors adhere to cybersecurity guidelines and obtain self-certifications for compliance.
• Systems Managed by MIIs:
Market Infrastructure Institutions (MIIs) are responsible for cyber resilience when offering internet services.
• Periodic Audit:
Conduct annual audits for compliance, performed by CERT-IN empanelled auditors or independent CISA/CISM qualified auditors.
Benefits of SEBI Security Audit
Enhanced Transparency and Accountability:
Security audits provide investors with an objective and transparent assessment of a company’s financial health and compliance with regulatory standards. This transparency fosters investor confidence and helps them make informed investment decisions based on reliable information.
Early Detection of Fraud and Irregularities: Security audits are designed to uncover potential irregularities, accounting errors, or fraudulent activities within a company. By identifying these issues early on, the audit process can prevent them from escalating and causing significant losses to investors.
Strengthened Internal Controls:
A comprehensive security audit evaluates the effectiveness of a company’s internal controls, which are policies and procedures designed to safeguard assets, ensure compliance, and promote operational efficiency. Identifying weaknesses in internal controls helps companies enhance their risk management practices and protect investor funds.
Operational Efficiency Improvement:
Security audits often uncover operational inefficiencies and weaknesses in a company’s processes. By addressing these issues, companies can improve their overall efficiency, reduce costs, and enhance their competitive edge.
Enhanced Corporate Governance:
Security audits promote sound corporate governance practices by assessing a company’s adherence to regulatory requirements and ethical standards. Strong corporate governance fosters investor confidence and attracts long-term capital.
Conclusion
SEBI’s proactive stance via the Security Audit and Cyber Security Framework protects the Indian securities market and investors. Implementing robust cybersecurity measures and regular audits ensures readiness to combat threats and secure financial data. Beyond compliance, these measures boost investor confidence, drive proactive cybersecurity, and offer a competitive edge. SEBI enforces compliance and promotes cybersecurity awareness, preserving the integrity of the securities market. It’s vital for market intermediaries and listed companies to embrace these measures, safeguarding investor interests.
References :
https://www.sebi.gov.in/legal/circulars/dec-2018/cyber-security-and-cyber-resilience-framework-for-stock-brokers-depository-participants_41215.html
https://www.csoonline.com/article/644587/indias-stock-market-regulator-sebi-releases-cybersecurity-consultation-paper.html
https://www.mondaq.com/india/security/1395210/strengthening-cybersecurity-governance-sebis-new-disclosure-requirements
https://www.fortuneindia.com/investing/sebi-comes-up-with-framework-to-address-cybersecurity-risks-to-regulated-entities/113261