Database Configuration Audit for Security and Compliance [Part-1]
Database Configuration Audit is the latest buzz word everyone is talking about and every organization wants to revamp their databases to produce and store a prioritized list of security improvements to the concept, requirements, design, or implementation.
Overview
Configuration Audit of a database includes noticing a database in order to know about the activities of its users. Database administrators and consultants frequently set up auditing for security purposes, for instance, to guarantee that those without the consent to access the data do not access it.
Database Auditing is the New Frontlines
Database Audit is a procedure of checking access to and modification of particular database objects and assets inside operational databases and holding a point-by-point record of the access where it very well may be utilized proactively to trigger activities and can be recovered and analyzed as required. Database audits are one of the significant compliance modules that should be set up appropriately yet rapidly so that the organization doesn’t pass up business scope requiring the storage of user information.
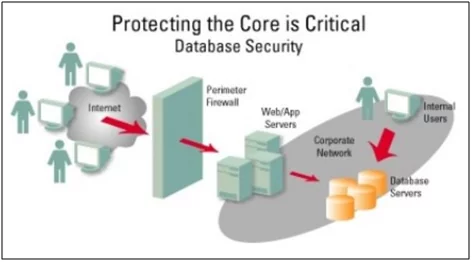
Fig: 1.0 Traditional Database
When DB auditing is empowered, each audited DB activity delivers an audit trail of data including, for example, what information DB object was affected, who played out the activity, and when.
Factors that Drive Requirements for Database Auditing
- Cost of Breach
Attackers are focusing on the database where records can be collected in mass on a worldwide scale. Around 88% of all cases in the current year’s investigation included insider negligence. Source: IOUG Data Security Report 2019, Joe McKendrick, Research Analyst.
Fig: 1.1 Database target Records
- Regulatory Compliance
Database surveillance is a key prerequisite in executing better security setups and to prevent losses from happening. The number of compliance issues is directly interrelated to the amount of data stored in the database i.e. Volume of information – > Increased availability of information – > Regulatory Compliance – > Increased number and kind of threats.
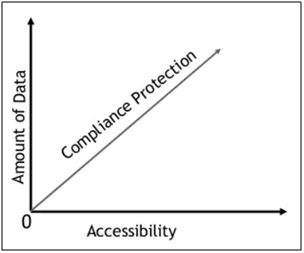
Fig: 1.2 Correlation Graph
- Database Leak PreventionConfiguration audit of a database assists with addressing questions like “Who got to or changed information?” and “When was it really changed?” and “What was the old content preceding the change?” Your ability to react to such requests can reflect the deciding moment of a compliance audit. Sometimes it may be imperative to review certain audit data more precisely to decide how, when, and who changed the data.

Fig: 1.3 Database Leak Scenario
There can be numerous users who may have permission to manipulate information, and it is significant that all classified and confined information should not be altered by other unauthorized users.
- Open Accessibility
Data today is additionally enormous and portable. You may have something on-premises just as some in the public cloud, which may request a lot of networking. Keeping up the availability of data will assist you with understanding plentiful volumes of data and furthermore distinguish the network asset requirement for better setup of your network framework.
Fig: 1.4 Data Availability
Database Configuration Audit Points
There are a few well-known strategies that can be implemented to audit your database structures. Although each Database offers various auditing properties, some basic items that can be audited at the configuration level include:
- Login and logoff efforts (both successful and unsuccessful efforts)
- Database server reboots
- Commands supplied by users with system administrator privileges
- Attempted integrity breach (where modified or inserted data does not match a referential, unique, or check constraint)
- Select, insert, update, and delete operations
- Stored procedure executions
- Unsuccessful efforts to access a database or a table (authorization failures)
- Changes to system catalog tables
- Row-level operations
Questions That Should be Answerable For Database Configuration Audit
As you explore the database access auditing necessities for your organization, you might assemble a rundown of the kinds of questions that you need your solution to have the option to reply. A decent database access auditing solution must have the option to give answers to at least the following questions:
- Who retrieved the data?
- At what date and time were the retrievals?
- What program or customer software was utilized to get to the data?
- Was the request successful; assuming it to be, what number of rows of data were recovered?
- From what area was the request issued?
- If the command were to modify the data, what data was modified? (A before and after picture of the modification should be accessible)
Obviously, there are various details behind every one of these questions. A strong database access auditing solution ought to give a free instrument for long-term storage and access to audit details.
Conclusion
Database configuration audit is progressively turning into a prerequisite for guaranteeing data security and compliance with industry and legislative guidelines. Be sure to contemplate the auditing capacities of your DBMS and to review any third-party database auditing tools to comprehend which of the techniques talked about here are utilized to support the auditability of your databases.
References:
- https://www.sqlshack.com/various-techniques-to-audit-sql-server-databases/
- https://blog.monyog.com/database-audit-log-monitoring-for-security-and-compliance/
- https://www.sqlshack.com/sql-server-auditing-server-database-audit-specifications/
Author,
Sankalp Mahajan
Attack & PenTest Team
Varutra Consulting Pvt. Ltd.