3 Must-Haves in Your Cybersecurity Incident Response Plan

Cyber-attacks never issue any prior intimation or warning; it just happens anytime. Basically, with cybersecurity incidents, it is a matter of “when” rather than “if.” These incidents have an adverse effect and receive significant media coverage. It results in the auditors, clients, and stakeholders expecting the organization to be completely prepared for such situations by presenting a proposal on managing such cybersecurity incidents as they impact the brand, reputation, employees, clients, and other shareholders. So, the risk management and security team need to prepare a detailed document of an incident response plan.
What is Incident Response?
Dealing with security breaches in any organization is known as the incident response. The incident response aims to identify the attack, limit the damage caused, and eliminate the incident source. Some examples are breaching laws and policies or inappropriate acts regarding sensitive information and assets. With the increase in data breaches, a lack of incident response plans can take more prolonged recovery time, resulting in increased cost and damaging the organization’s information security effectiveness. Therefore, incident response is a critical activity to secure any organization.
Importance of Incident Response
By responding to an incident instantly, an organization can reduce losses, restore services, and mitigate exploited vulnerabilities. Incident response acts as a vanguard for any organization. It helps establish and encourage the best cyber hygiene practices that will help prevent future security breaches. In addition, a reliable incident response helps identify any security threat and block them before they can exploit an organization’s vulnerabilities.
A response strategy should be designed to keep a broad range of incidents that could occur. A minor incident can also cause a significant impact on the organization and damage the reputation, which could lead to data loss and other technical issues affecting productivity. It can also lead to severe consequences like legal issues and financial penalties, costing millions.
Three Must-Haves for Your Cybersecurity Incident Response
Here are three important factors that an organization should consider while working on its cybersecurity incident response. It will help them prepare themselves better for any future incidents.
Build an Incident Response Plan
It is built to counter cyber-related incidents and threats. According to the IBM 2021 report for the data breach, the cost rose from $3.86 million in 2020 to $4.24 million in 2021. So here is a roadmap on how to build an incident response plan.
- Developing the Map for Response Process: The incident response plan should be very detailed and systematic on how to proceed in the situation of crisis. The person in charge or incident coordinator should handle each step, track the process, and keep the communication rolling.
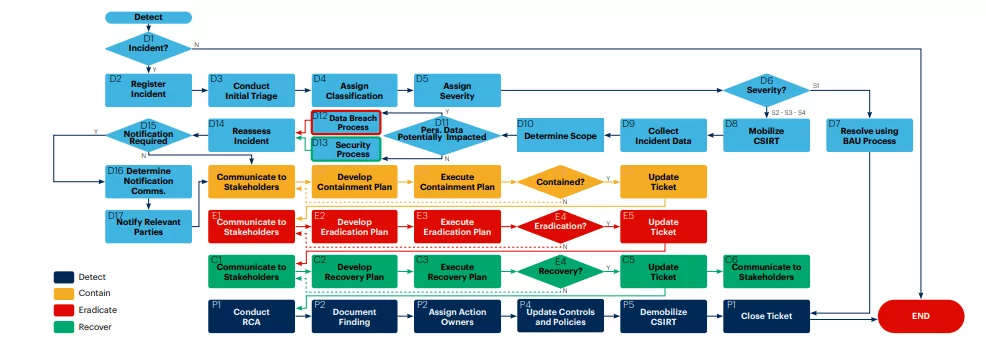
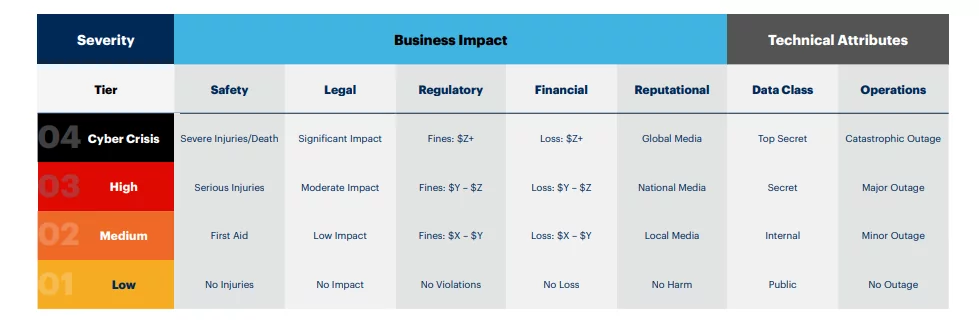
- Defining Severity Tiers During Security Incidents: All the security incidents should be prioritized and assigned a severity tier. It helps guide any incident escalation occurrence, set the service-level contracts, and communicate the information regarding the potential impact of an incident on the organization. The severity also helps define the roles for the people who will be assisting, along with the path to follow and what playbook is to be used in such a scenario.
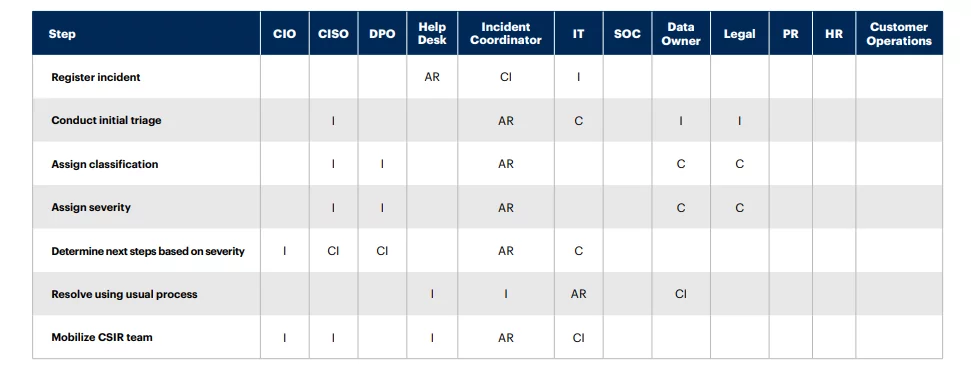
- Assigning of Roles and Responsibilities: Delivering an effective and efficient incident response is an obligation of a team. The maintenance of the RACI chart should be designed so that all the roles and responsibilities for an incident response should be visible clearly across the organization. The common stakeholders included are legal, c-suite, HR, and privacy teams.
Detailed Response Guides and Playbooks
Create detailed and descriptive response playbooks or guides for managing particular cyber incident scenarios. For example, as per Coveware, more than 80% of ransomware attacks lead to stealing sensitive data and encryption.
- Creating Response Playbooks and Guides: It is recommended that the CSIR team from any organization should create a specific playbook or guide for different types of incidents that may occur. Let’s take ransomware as an example and create a sample response playbook. It should be very descriptive and provide detailed steps for any general security incident response plan.
- Develop a Response Process for a Ransomware Attack: Design a response process for a ransomware attack along with a decision tree. This procedure is used to create a response process, allocate roles & responsibilities of the people involved, and develop a secondary report that the CSIR team can utilize to govern their response.
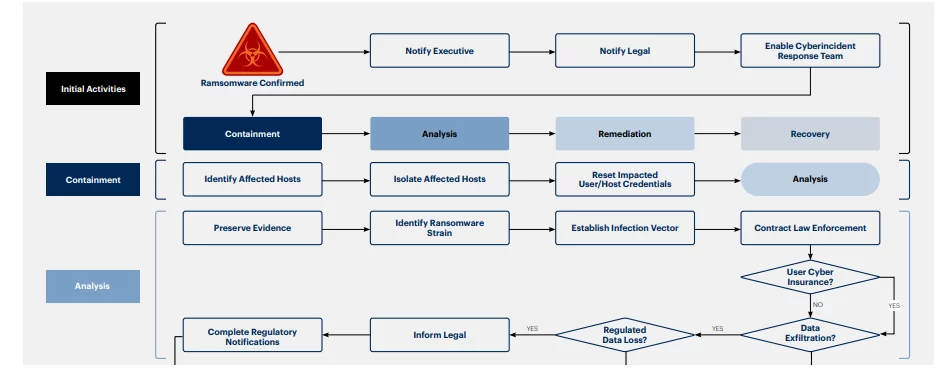
- Compile the Detailed Report on Response Procedures: Collaborating with the SMEs (Subject Matter Experts) to compile a report about a detailed ransomware response procedure. The procedure should consist of specific tools, suggestions, examples, and more which should ultimately help identify the responsible team or person for every step.

Performing Routine Tests
Conduct routine tests to practice the cyber incident response plans. In a report from Coveware, an average of 23 days is created during the ransomware attack.
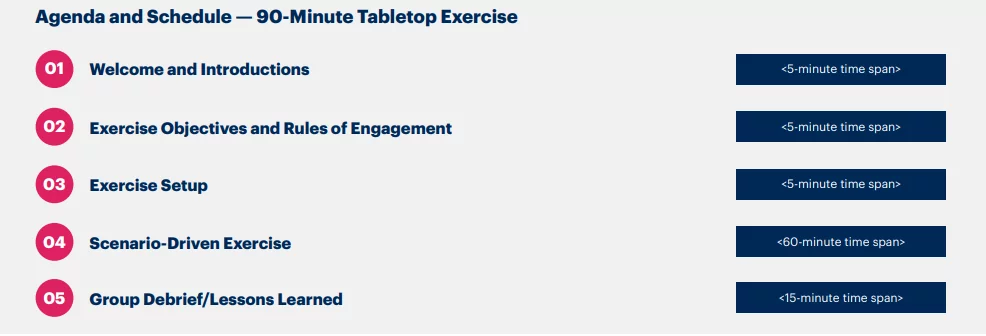
- Designing Agenda and Sending Participation Invites: Tabletop exercises for an incident response should include both the leadership and decision-makers of the organization. For a tabletop to succeed, it is suggested to provide specific objectives and a well-defined structure covering pre-planned scenarios to which participants will be reacting.
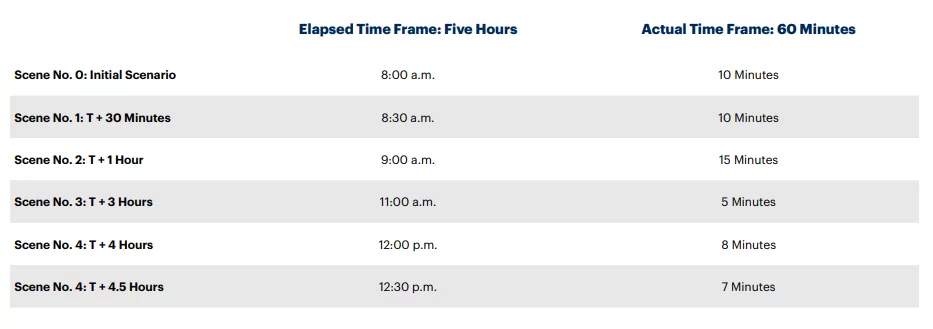
- Recreating Incident Scenes and Scenarios: For more effectiveness, a cybersecurity tabletop exercise should be structured to a previous scenario (for example, a past malware attack scenario). It should be further followed by some other scenarios due to additional information on incidents to which the participants must react. This structure will help recreate the uncertainty caused in the past and help in the evolution of actual incidents.
- Craft Threatening and Challenging Incident Scenarios: The tabletop exercise should comprise replicated challenging questions and scenes that a stakeholder should be able to address in an actual attack. For example: Challenging the participants to react to a hacker’s ransom demand for a ransomware attack as a tabletop exercise. Here are some significant points that are to be considered about the realities during ransom payment:
- It isn’t easy to recover encrypted files.
- Recovering data is a slow and tedious process that can take several weeks.
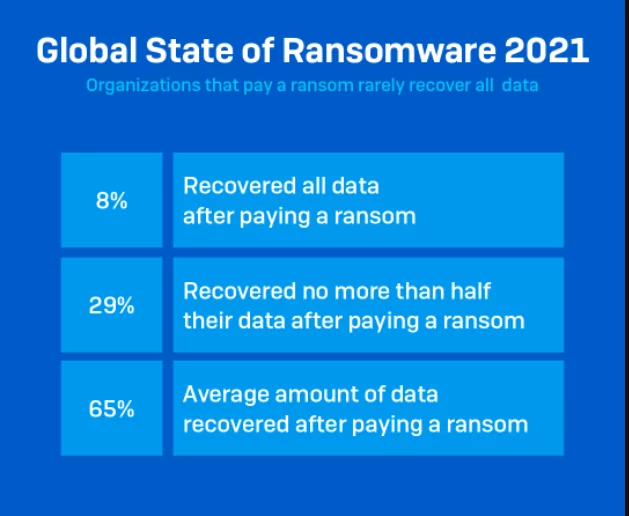
- On average, only 65% of data is usually recovered, and only 8% of organizations can successfully recover all the lost information.
- One can never be sure that the hackers have deleted the stolen data after collecting the ransom. They can even sell or disclose the data in the future if it has excellent value.
- There are chances that the decrypters provided by the hackers may fail and crash.
- By paying the ransom, you are encouraging criminal behavior.
- There are cases where paying ransom could be illegal.
Conclusion
The primary objective of incident response is to have seamless coordination between the team members and the other resources during a cyber incident. In addition, it will help minimize the impact and efficiently restore the organization’s operations through proper analysis, reporting, and response.
In modern Security Operations Centers (SOCs), advanced analytics plays a substantial role in identifying and investigating these cyber incidents. For example, UEBA (User and Entity Behavior Analytics) technology is used by several teams to determine the baselines of users or IT systems and automatically detect any abnormal behavior. This procedure makes the work more accessible for the security staff to identify any strange behavior or event that may contribute to a security incident.
Reference
Author,
Sanjana Yadav,
Marketing Department,
Varutra Consulting Pvt. Ltd.




