Using SecLists for Penetration Testing

Introduction to SecLists
Seclists is something that comes very handy to a pen tester. The simple reason is, it has a collection of all the wordlist lists that is related to different technologies, web servers, and web shells that can be helpful while performing penetration testing on any particular target.
How to Install SecLists?
All the Kali machine has the option of seclists. To run it for pentesting, we need to install it in our system. There are a couple of different ways of installing it on our machine.
- We can install it by cloning the seclists repository from GitHub and importing the same into the system. Then, we just have to run the install command.
- Another way is to connect to the seclists repository online and then, run the install command in the system to install it.
Here is also an alternate method of installing the lists in the system. There will not be any problem in installing seclists directly by connecting to the package online if your system is up-to-date. In case, your system is not up-to-date then you may come across some issues while installing. In such a scenario, you can opt for updating the index package in the sources.list file. Edit the file and add the following path for the kali index in the file.
Path to add in the file:
https://mirrors.ocf.berkeley.edu/kali-images/current/
After adding this index path to the file, save the file and then run the following command in the terminal to install the seclists in your system.
Command:
sudo apt-get install seclists
After installing, you can access the seclists under the path: /usr/share/seclists. There are different types of lists that are included in this folder.
- Discovery
- Fuzzing
- IOC’s
- Miscellaneous
- Passwords
- Pattern-Matching
- Payloads
- Usernames
- Web-Shells
Below is the tree representation of seclists. The tree displays its directory structure.
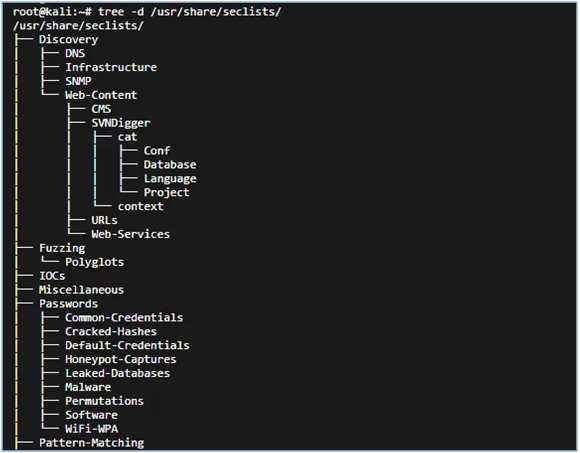
Fig: Tree structure of Seclists
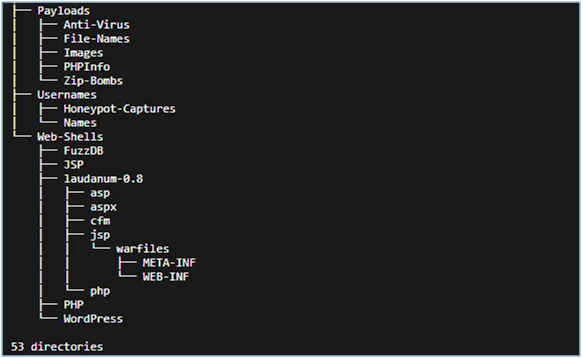
Fig: Tree structure of seclists
How to use SecLists?
Seclists contains a lot of different wordlists that are used for multiple purposes with different available tools. These lists are segregated according to usage. In this blog, we will discuss a couple of the seclists categories and how to use them.
- Discovery: It is the initial phase in pentesting. Once the target is fixed, an attacker will try to gather information about the target and move forward accordingly.
This phase includes enumerating the target for different things like subdomains, open ports, running services, etc. The discovery module includes different sub-categories like DNS, Infrastructure, SNMP, Web-Content, and more that can be used for enumerating the target.
Eg: The below example shows how we can automate the process of sub-domain enumeration using dirb and seclists.
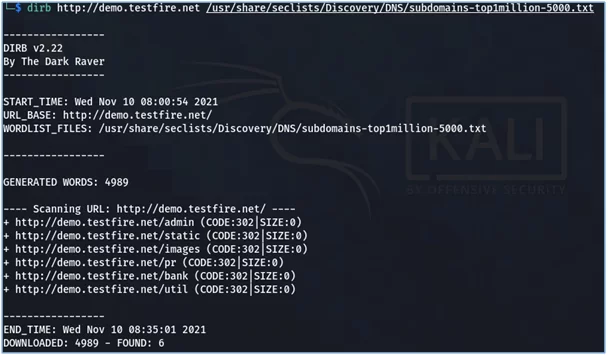
Fig: Subdomain enumeration using dirb
In the above-shown example the command that was used is as follows:
- dirb http://demo.testfire.net /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt.
Here in this command, the first part is the URL of the target i.e., http://demo.testfire.net and we have given the path of the wordlist that is used from the discovery module of seclists.
And below you can see different subdomains found for the given target.
- Fuzzing: Fuzzing is a technique where an attacker might try to feed large volumes of inaccurate data like payloads into an input field until a bug or a vulnerability is found. The fuzzing module of seclists contains the following wordlist related to different types of attacks.
Fig: Wordlists in fuzzing module of Seclists
There are different lists related to Databases, LFI, SQLi, XSS, etc. using which you can fuzz for the respective attacks.
Conclusion
This way you can successfully learn how to install and run seclists in your system and use them for pentesting. There are various penetration methods like android penetration testing with drozer, AWS pentesting, and much more that you can read in our blog section.
Author
Pralekya H.
Associate Security Consultant
Attack & Pentest Team,
Varutra Consulting Pvt. Ltd.