Quantum-Ready Data Security: Safeguarding Information Beyond the Binary Framework
Abstract
In the rapidly advancing landscape of quantum computing, the potential for revolutionary processing power also brings forth significant challenges to cybersecurity. This white paper provides an overview of quantum computing and the risks it poses to data security. It examines solutions emerging to help enterprises test and adopt quantum-safe cryptography, including cloud-based quantum services for experimentation. A detailed framework is provided for how companies can become “quantum-ready” by listing their usage, assessing risks, testing new protocols, and formulating a migration strategy. With diligent preparation using cloud platforms, enterprises can ensure their long-term security in an era of transformative quantum capabilities.
The Exponential Power of Quantum Computing
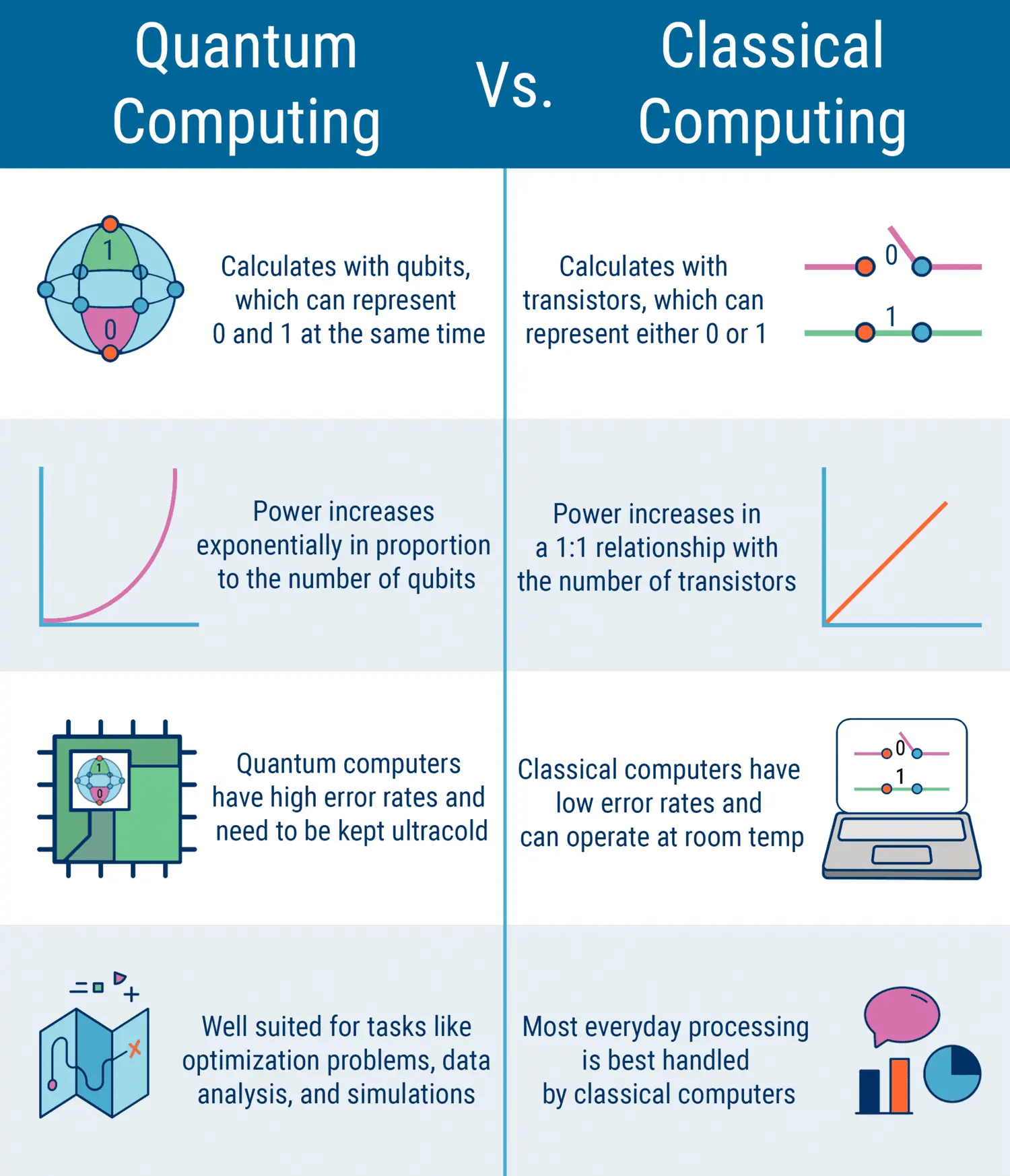
Classical computers process information in binary bits with discrete 0 and 1 states. Quantum computation utilises quantum bits (qubits) that can exist in a superposition of 0 and 1 simultaneously. This property, along with quantum entanglement and parallelism, will allow quantum computers to solve complex problems and execute calculations far beyond traditional systems.
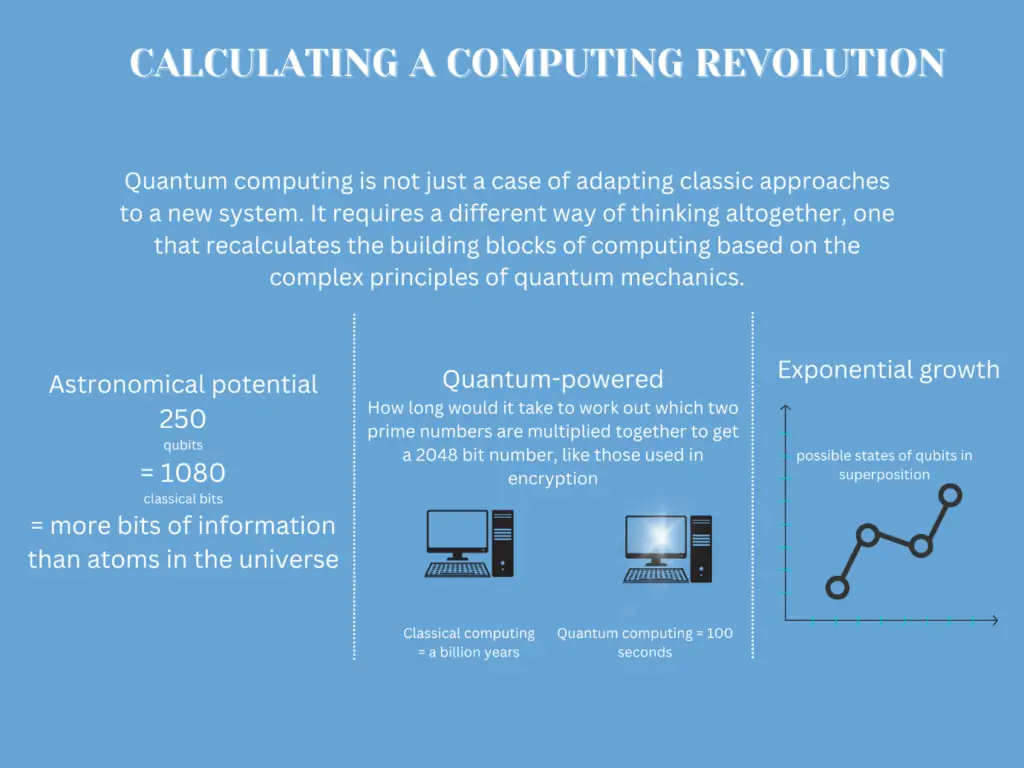
While fully realized, large-scale quantum computing is still years away, the pace of advancement in recent years has been startling. Technology giants like IBM, Google, Honeywell, and Microsoft are making rapid strides in developing quantum hardware and systems. Smaller startups like Rigetti, IonQ, and D-Wave are also pushing the boundaries of quantum capabilities.
The global quantum computing market is projected to grow from $507 million in 2020 to over $65 billion by 2027. (Allied Market Research)
Global Technology Company Investments in Quantum Computing

The table below demonstrates the annual doubling of qubit counts among major quantum players:

Table 1: Exponential Increase in Qubits Among Providers
*Sources: IBM, Google, Microsoft, AWS, Rigetti, IonQ
The Quantum Threat to Data Encryption
Modern data security relies extensively on cryptography to protect confidentiality and enable trust. Widely used public key algorithms including RSA, ECC, Diffie-Hellman, and DSA are vulnerable to being broken by quantum computers due to Shor’s algorithm.
•55% of organizations have no plan in place to upgrade to post-quantum cryptography before algorithms become vulnerable. (Thales)
•63% of healthcare organizations experienced a quantum-vulnerable data breach in the past 2 years. (PwC)
•81% of financial services firms say quantum computing could have a highly disruptive impact on their cybersecurity model. (Fitch Solutions)
This will enable quantum-enabled adversaries to:
•Decrypt any data secured by public-key encryption, including historical communications and stored data.
•Impersonate users and devices protected by public-key digital certificates.
•Break the public key infrastructure (PKI) system underpinning security online.
This would impact industries such as:
Healthcare: Medical records, clinical data, patient information
Finance: Transactions, investments, account credentials
Government: Classified communications, intelligence data
Transitioning to post-quantum cryptography resistant to quantum attacks will soon become an imperative.
Post-Quantum Cryptographic Algorithms
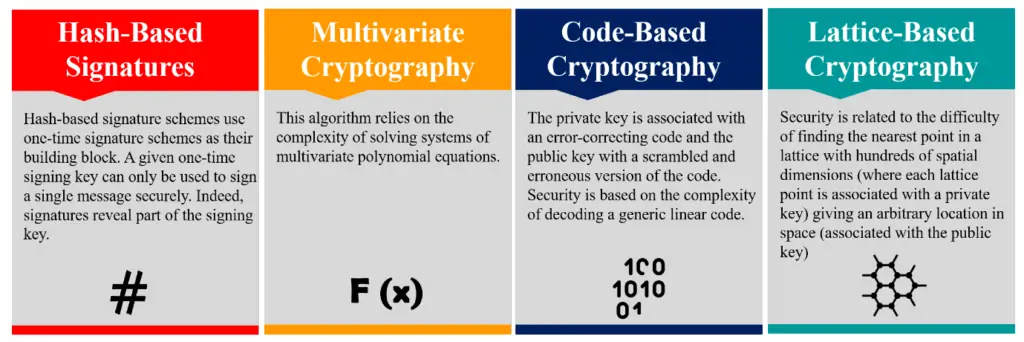
Research is advancing on cryptographic algorithms resilient to quantum computing:
a.Hash-based Cryptography
Schemes like SPHINCS+ utilize cryptographic hash functions rather than mathematical problems. Hash-based signatures are stateless and efficient on conventional systems.
b. Multivariate Cryptography
Schemes like Rainbow utilize systems of multivariate polynomial equations over finite fields, which become intractable for quantum algorithms.
These post-quantum protocols form the basis for securing systems into the quantum era.
https://www.varutra.com/wp-admin/admin.php?page=aioseo
c.Code-based Cryptography
Based on error-correcting codes, algorithms like Classic McEliece provide relatively efficient and conservative security guarantees. However, key and ciphertext sizes are generally large.
d.Lattice-based Cryptography
Algorithms like Crystals-Kyber and Falcon rely on lattice mathematical structures. Kyber is an encryption and key exchange protocol while Falcon provides digital signatures.
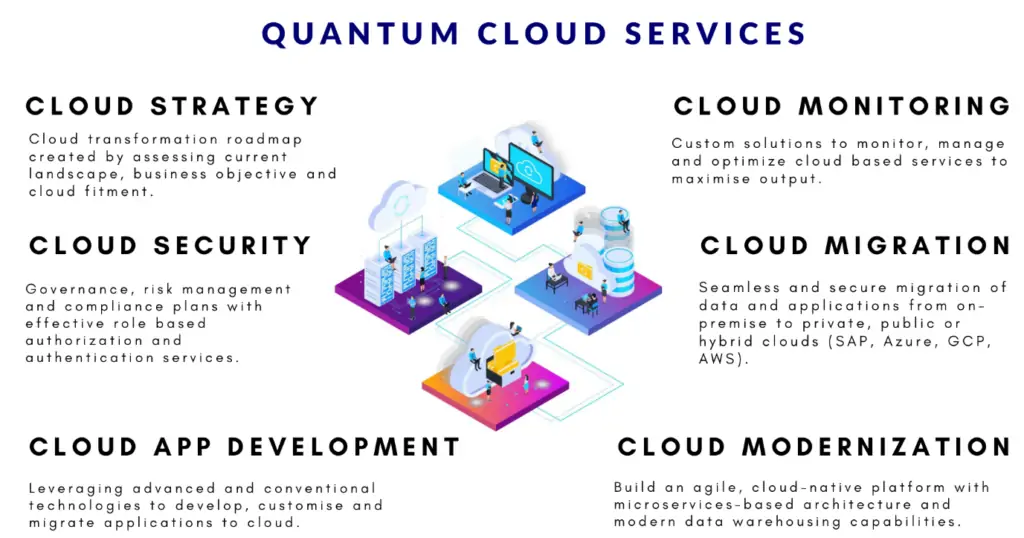
Quantum-Safe Cloud Platforms

Leading cloud providers offer early access to quantum-safe technologies:
1.Amazon Braket
Amazon’s quantum computing service provides a hardware-agnostic developer toolkit (Braket SDK) and access to quantum hardware from Rigetti, IonQ and D-Wave.
2.Azure Quantum
Microsoft Azure Quantum allows developers to get started with the Q# quantum programming language. It offers quantum algorithm libraries and quantum-safe cryptography tools.
3.IBM Quantum Experience
The IBM Quantum Experience gives users access to real quantum hardware and simulators to run experiments using Qiskit, IBM’s open-source quantum development kit.
These cloud platforms enable enterprises to explore, test, and prepare for the coming quantum disruption.
These risks extend to enterprise systems, cloud platforms, connected devices, and digital transactions online. While symmetric cryptography like AES is considered quantum-safe, the pervasive use of weak public-key mechanisms could be devastating.
Transitioning to post-quantum cryptographic (PQC) algorithms resistant to quantum attacks across enterprise IT infrastructure, cloud environments, and connected systems will soon be mandatory. Every application and protocol relying on vulnerable public key encryption needs to be assessed and upgraded.
Cloud-Based Quantum Security Solutions
Fortunately, intensive research is already underway on new quantum-safe cryptographic algorithms and protocols resistant to cryptanalysis from quantum computers. Cloud platforms are making some of these post-quantum technologies available to experiment with:
Quantum Computing Access: Services like Amazon Braket, Azure Quantum, and IBM Quantum Experience provide access to real quantum hardware and simulators to run algorithms. These allow developers and researchers to gain hands-on quantum experience.
Quantum-Safe Crypto Libraries: Microsoft’s Azure Quantum SDK, Amazon’s Quantum Solutions Lab, and IBM’s QISKit provide software libraries with post-quantum cryptographic algorithms to test quantum-safe encryption, signatures, and key exchange.
Quantum Key Distribution (QKD): AWS and Azure are actively researching Quantum Key Distribution (QKD) to facilitate the secure distribution of symmetric keys for communication. This capability ensures perfectly secure key exchanges, even over public channels.
Quantum-Safe Certificates: Services like DigiCert Quantum Origin generate digital certificates secured with post-quantum cryptography to future-proof authentication and encryption of data.
These types of services allow enterprises to develop skills, pilot quantum-safe capabilities, and prepare for the coming quantum disruption.
Framework for Becoming Quantum-Ready
For enterprises, the window to prepare for the post-quantum future is rapidly closing. Organizations should begin assessing their risk exposure and formulating a migration plan using the following framework:
Step 1 – Inventory Cryptographic Usage
•Catalogue all encryption implementations across on-premise & cloud systems.
•Identify use of vulnerable asymmetric algorithms like RSA, ECC, DH, DSA.
•Classify risk level of different applications and data types.
Step 2 – Conduct Risk Analysis
•Assess business impact of quantum breaks of existing cryptography per application.
•Prioritize order to upgrade based on potential damage.
•Review systems with highest sensitivity, such as payment processing or employee/customer PII.
Leading Post-Quantum Cryptography Algorithm Types

Step 3 – Test Quantum-Safe Cryptography
•Utilize cloud platforms with post-quantum cryptography libraries to pilot quantum-safe implementations.
•Experiment with quantum-safe key exchange, encryption, and signature protocols.
•Evaluate performance impacts during testing.
Step 4 – Follow Standards Development
•Monitor guidance from NIST, IETF, and ETSI on post-quantum standards.
•Be prepared to implement new quantum-safe protocols like CRYSTALS-Kyber as standards solidify.
NIST Post-Quantum Cryptography Standards Timeline:

Step 5 – Formulate Migration Strategy
•Develop cryptographic roadmap to systematically transition vulnerable systems to quantum-safe algorithms aligned with industry standards.
•Prioritize most sensitive data protection mechanisms and high-value systems.
•Budget for enterprise-wide upgrades to quantum-safe cryptography when standards finalize.
Conclusion
Quantum computing represents one of the most disruptive upcoming changes to enterprise security. While the full implications are still years away, every organization needs to begin their journey to become quantum-safe now. By leveraging cloud-based quantum technologies and developing a quantum migration strategy, companies can upgrade their data protections to withstand the new quantum threat horizon. Building quantum-readiness will soon be a prerequisite for any enterprise handling sensitive data.
Image Reference
Image Source https://www.cbinsights.com/research/quantum-computing-classical-computing-comparison-infographic/
Image source https://www.quantumdtech.com/cloud_services
Image Source: https://www.mdpi.com/2624-831X/2/1/5
Image Source: https://www.linkedin.com/pulse/quantum-cloud-computing-platforms-dr-vamsi-mohan-vandrangi/
References
https://www.cigionline.org/articles/quantum-threat-cyber-security/
https://www.techtarget.com/searchdatacenter/feature/Explore-the-impact-of-quantum-computing-on-cryptography
https://www3.weforum.org/docs/WEF_Quantum_Readiness_Toolkit_2023.pdf
https://www.koombea.com/blog/quantum-cloud-computing-solutions/
https://www.predictiveanalyticstoday.com/what-is-quantum-computing/
https://www.rolandberger.com/en/Insights/Publications/Quantum-technology-is-leaping-into-our-lives.html
https://www.quantumdtech.com/cloud_services
https://www.mdpi.com/2624-831X/2/1/5
https://www.linkedin.com/pulse/quantum-cloud-computing-platforms-dr-vamsi-mohan-vandrangi/




