Why Zero-Trust Security Enables the “Work From Anywhere” Model?

COVID-19 compelled people to work from home (WFH), but now this option is being continued by multiple organizations across the globe. The concept of a hybrid and remote work environment is the new normal. It is possible because of the flexible work option that the employees get and is considered an ideal work model. It improves the employee’s productivity and gives overall work satisfaction.
Working on Zero-Trust Security
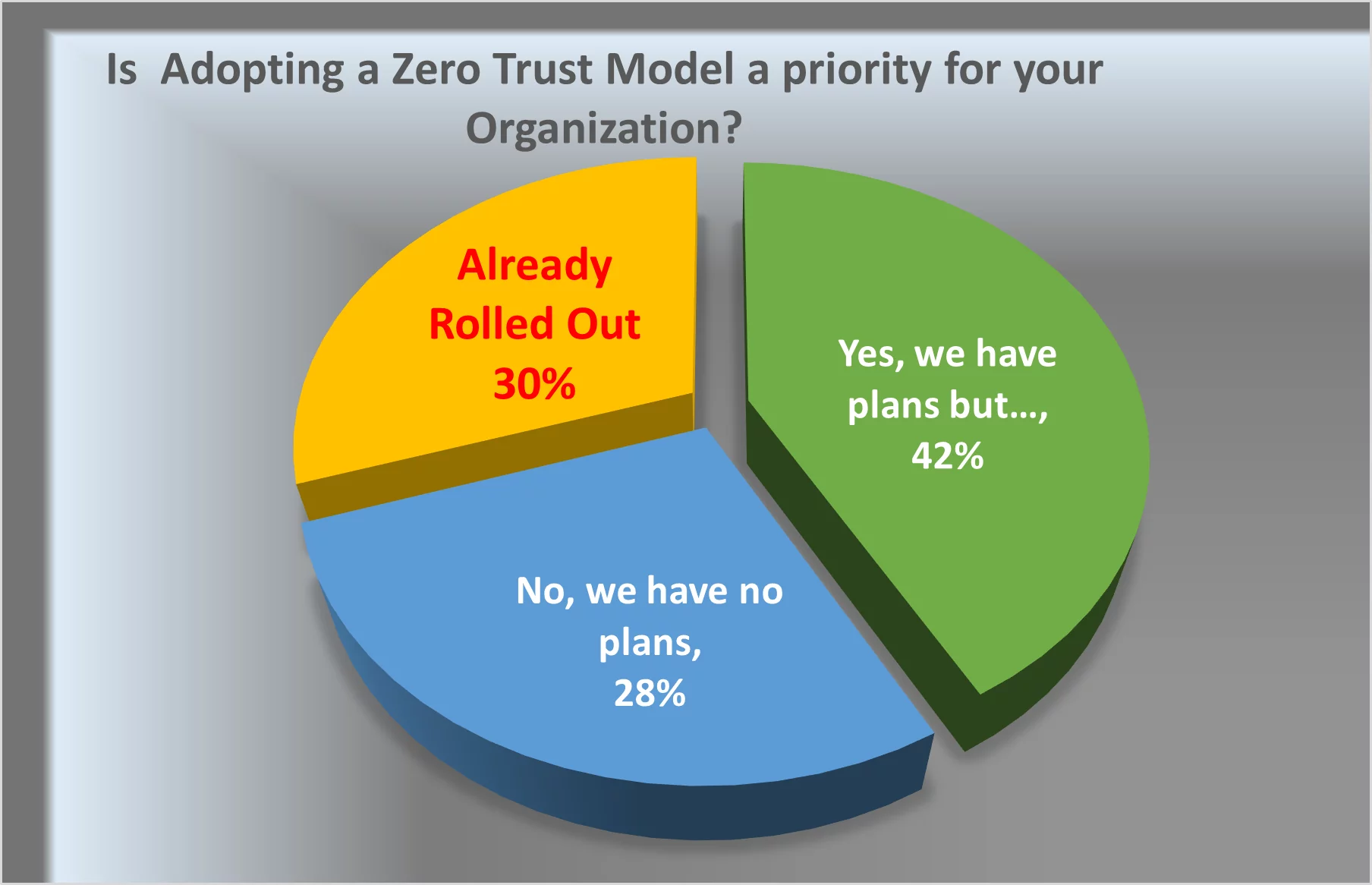
Though the remote work option is ideal for the employees, there are various complications in its successful implementation. For example, security is one of the major issues an organization comes across. Zero-Trust Network Access (ZTNA) is considered an excellent option for such a situation. Companies that fully implemented zero trust saved 43% on data breaches.
ZTNA is designed for a smooth and secure WFH as it provides the same security options to the employees irrespective of their work location. In addition, it helps in reducing the attack surface by concealing the software and applications through a proxy point while browsing the internet.
ZTNA enforces granular, context-aware, and adaptive policies for secure and seamless Zero-Trust access to all the applications hosted across the cloud servers or corporate data centers. The employees access them from any remote location or device. ZTNA accesses the user identity, integrity of the device, user location, type of service, and other detailed elements. This procedure is carried out to provide access to the employees’ applications and restrict access to the applications they do not operate. Zero Trust Network Access helps in reducing the chances of an attack surface by blocking the ingenious threat actions from compromised devices or accounts.
ZTNA is built on Zero Trust, which emphasizes that the organizations should not trust or avoid the entities they are not familiar with, irrespective of their position in the security parameters. They should first check and verify the user and device before accessing any sensitive resources.
ZTNA acts as a key enabler for the Secure Access Service Edge or SASE. It transformed the security perimeter from static enterprise data centers to a more dynamic one. It is done by making it more policy-based and providing a cloud-delivered edge to support the access requirements of all the distributed workforce.
3 Scenarios Where Zero-Trust Security Enables Working from Anywhere Possible
WFH is not a simple task. It is not just limited to employees working from home but also how they can work in a secure environment. They need secure connectivity for the employees to access applications or resources stored in the data centers or cloud. So, it is crucial to keep everything consistent by integrating ZTNA, endpoint, and network security with the standard set of APIs and integration points.
Working From Home (WFH)
Employees who work from home connect their office devices like laptops, webcams, or more to the home network. Their home network may not be much more secure as it is connected to other devices and applications that may not be secure like other IoT devices (Internet of Things) or users. In addition, those users may stream some vulnerable sites that could lead to potential exploitation or attack, as these connections are outside the network security and control. By integrating ZTNA, the organization creates a secure tunnel that shields users from other issues that may exploit their home network. The ZTNA client on the endpoint will create a secure tunnel to provide the device’s identity and report its status to the endpoint. This procedure will help employees get access to the application on request.
Working On the Road
Employees seldom connect to an unknown or unsecured connection if an employee is traveling. It can raise the possibility of potential attacks as the system/ connection is not secure as the corporate network or offices. Connecting the office devices to such links could expose them to hackers or other miscellaneous attackers looking for such possibilities. Here ZTNA comes in very handy, as it only provides access to the people and devices permitted to access. Once the users are connected, it provides visibility and control that will help detect any malicious activity.
Working from the Office
In a corporate office, ZTNA provides smooth access to applications to the employees irrespective of their location, including the office. The user must provide access credentials from the office like MFA, multi-factor authentication, or endpoint validation for a smooth workflow. Once the employee is connected, they will get limited access, which means they can only access the applications they need to work on. The rest of the application access will be restricted for security reasons.
Conclusion
The work from anywhere option gives the employees the freedom to work from any place and flexibility. It is considered to be more productive compared to working from the office. ZTNA creates the same security protection and controls irrespective of the employee’s location to make this work model successful. Users can now quickly get secure access to the cloud and non-cloud resources without compromising them with consistent protocols and policies implemented across the network. It doesn’t matter where the employee is working from; zero-trust security should be applicable everywhere and offer a consistent experience for the users.
Author,
Sanjana Yadav,
Marketing Department,
Varutra Consulting Pvt. Ltd.




