How Managed Data Security Can Benefit Your Business?

Many people are now moving towards digital transformation for communicating, work, or entertainment. This global digital moment has facilitated industries and transformed markets in delivering their services. However, even though it has simplified the ways of working, it has also opened the doors to cyber-criminals looking for ways and means to exploit the user’s sensitive information. An organization collects a lot of data daily. This valuable data includes critical clients & customers data, finance data, and much more. Organizations generally have well-defined databases for their address book, locations, leads, etc. These databases are interconnected and form a Graphical User Interface (GUI) displayed on their screen, irrespective of the organization’s size or field. It requires a strategy to manage and provide data security for sensitive information compiled together in a database from external and internal cyber-attacks.
Many instances state that not all organizations cannot identify and mitigate the data breach, despite understanding the challenging situation. As per IBM’s report on Data Breach Cost, the average cost is around $3.86 million. Additionally, IDG Research Services stated that approximately 78% of IT leaders do not have a robust cyber security posture.
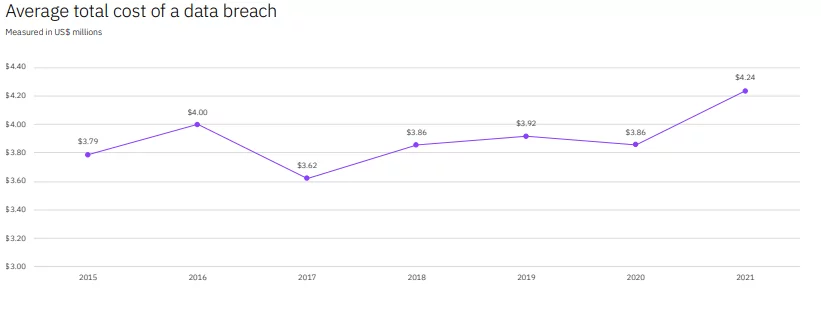
Source
What is Data Security?
Data security is one of the most significant factors of Data Management. Digital transformation has enabled everyone to capture everything in detail if they are online. However, most organizations have started focusing on the work-from-home module due to the pandemic. As a result, there are occasions when an employee tends to use devices that fall outside the corporate sight or monitoring equipment which is challenging and hinders the smooth functioning of data security management. The reason is that the personal devices do not have a proper security application setup which can compromise the system and affect the entire organization. Therefore, the government has provided data control regulations such as Health Insurance Portability and Accountability Act (HIPAA) or European General Data Protection Regulation (GDPR) for proper guidance to organizations to improve their data security management or be fined accordingly. Also, in MacAfee security report stated that 40.4% of IT security experts say that the security alerts they get lack the applicable intelligence required to investigate. Another 31.9% ignore the warnings due to many false positives.
What is Data Security Management?
There are multiple definitions for data security management, but everyone has one straightforward meaning, i.e., the proper and seamless management of data security for any organization. Organizations should have a clear interpretation of data security and have seamless communication as it helps them properly integrate the services. Here is how the data security management works:
- It is a practice that ensures all information is secured while it is in your possession from any unauthorized access.
- It blends both digital and physical data for seamless protection.
- It administers data procurement, storage, recovery, usage, and erasure so that any data is not damaged.
- It implements the latest technologies that act as a defense against any internal threats or malicious acts.
- Encourages the service providers to carry out tests to check their applications’ data security to prevent any data leakage.
- They also encourage and create awareness among individuals on protecting themselves against cyber-criminals and educate them about best cybersecurity practices.
- Using encrypted cloud storage or secure networks for data sharing and transferring.
- Checking the security of any external devices used for any data sharing.
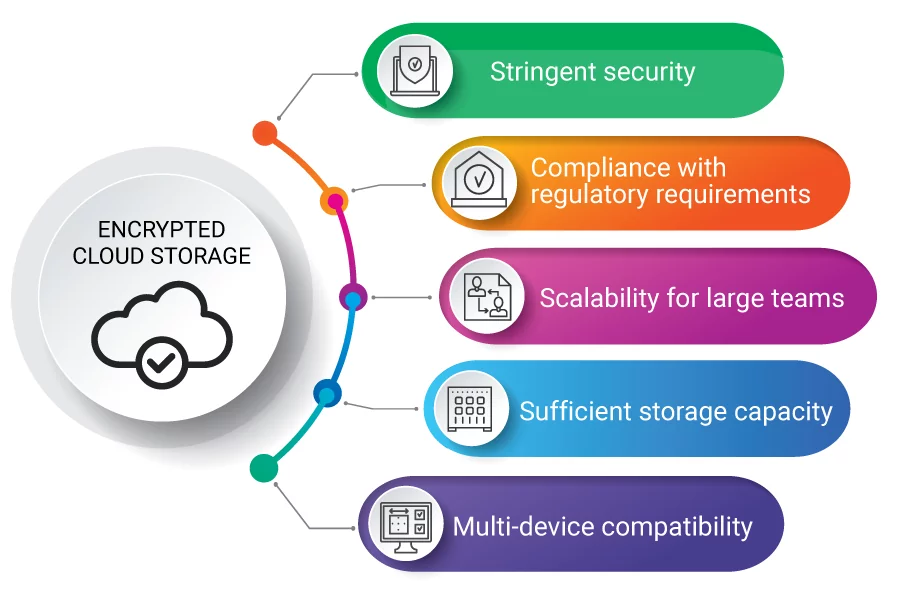
Data security management is the best practice that protects you and your organization from any unintentional mistakes that will open a backdoor for any cyber-criminal who is just waiting for an opportunity to steal or corrupt your sensitive data.
Improving Business Security with Managed Data Security
The Managed Data Security protects sensitive data across the organization while preventing data leakage and ensuring compliance is followed. Its primary function is to secure the structured and non-structured databases and constantly monitor the data traffic. In addition, it is a methodology that oversees and controls IT management integration and other supplementary security solutions to provide data protection.
It is necessary to have effective and efficient compliance with an affirmation to activities through a centralized audit repository seamlessly integrated into the workflow automation platform. It maintains the compliance aspect so that the organization can smoothly carry on with their workflow to understand that automation is operating on their processes and improving their time efficiency. Furthermore, it monitors the user behavior on authentication against database, inbound and outbound network traffic, and looks out for any data exfiltration or transfer. Identifying such threats beforehand can prevent potential damage to the organization and secure its sensitive data.
Source
What are the Benefits of Managed Data Security?
Here are some benefits of managed data security:
- Keep track of your sensitive and private data.
- Providing complete visibility and comprehensive analysis of your database activities.
- Examining and implementing policies that include authorization of control to sensitive information, privilege user actions, and database change control.
- Automating compliance auditing processes.
- Evaluation for database vulnerabilities.
- Identifies and tracks any configuration vulnerabilities.
- Tracking users’ actions for any suspicious activity.
- Building a reliable and single integrated audit repository of heterogeneous databases and systems.
- Less work for the IT team as it provides filtered action-oriented insights.
Conclusion
It is necessary to understand the risks regarding the database and the users who are using them as it helps identify any risks associated with them. It then helps implement UBA (User Behavior Analytics), which assists in categorizing the user behavior to identify any abnormal activity with malicious intent. By understanding the pattern, the organization will gain visibility and freedom to create context-driven cases. For example, suppose an employee has logged in late at night, has inconsistent remote access, or has unusual downloads. In that case, a risk score is given to the user based on their activity, pattern, and time. It will help in securing sensitive data.
Therefore, everyone is so concerned about data security. Protecting data is necessary as hackers are waiting to exploit any vulnerability they can find.
Reference
https://www.jigsawacademy.com/blogs/cyber-security/importance-of-data-security/
Author,
Sanjana Yadav,
Marketing Department,
Varutra Consulting Pvt. Ltd.