Advisory | Microsoft Zero Day – Windows Task Scheduler Local Privilege Escalation Vulnerability

Introduction to Microsoft Zero Day Vulnerability
A previously unknown zero day vulnerability has been disclosed in the Microsoft’s Windows operating system that could help a local user or malicious program to obtain system privileges on the targeted machine.
The vulnerability is a privilege escalation issue which resides in the Windows’ task scheduler program and occurred due to errors in the handling of Advanced Local Procedure Call (ALPC) systems.
Advanced local procedure call (ALPC) is an internal mechanism, available only to Windows operating system components, that facilitates high-speed and secure data transfer between one or more processes in the user mode.
Exploit for this vulnerability has been shared by a hacker named “SandboxEscaper” and the exploit code is currently available on public repositories like GitHub. However the current exploit works only in windows 64 bit operating systems. For a complete solution, we have to wait for Microsoft to respond until the scheduled September 11 Patch.
Affected Versions
1) Windows 10
2) Windows Server 2016
The exploit would need modifications to work on operating systems other than 64-bit (i.e., 32-bit OS). Also it hard codes prnms003 driver, which doesn’t exist in certain versions (e.g. on Windows 7 it can be prnms001). Compatibility with other windows versions may be possible with modification of the publicly available exploit source code.
How to Detect?
It is possible that the original windows processes can be replaced with the malicious program shared by the hacker. So we can detect those exploits by checking whether the original windows processes have been replaced.
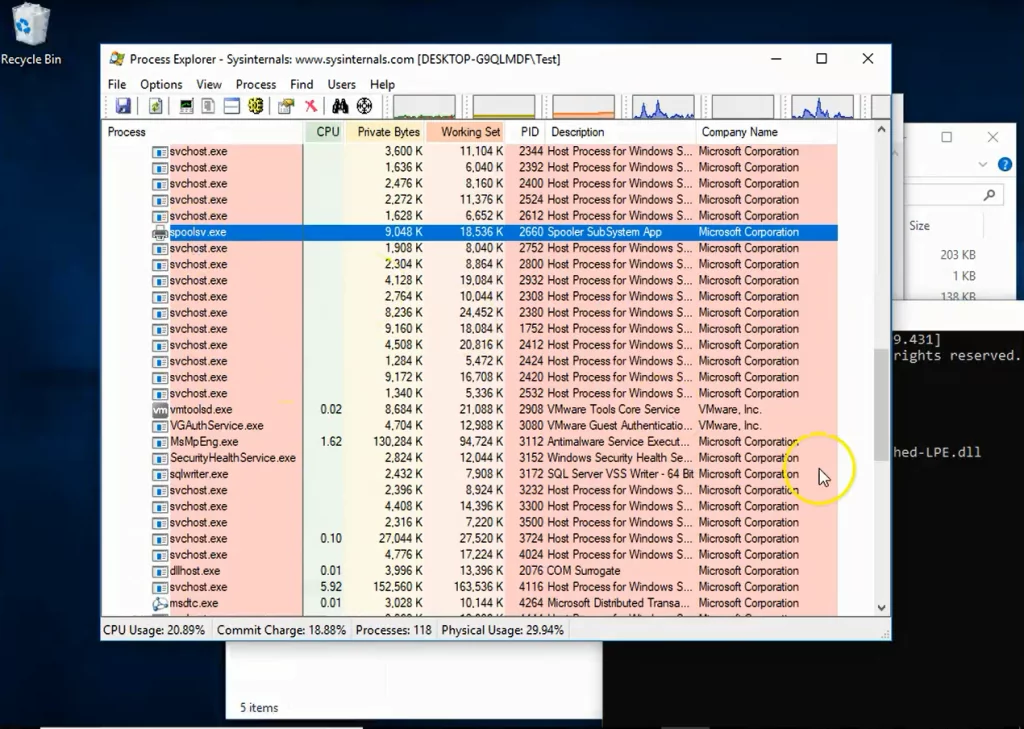
- Look for spoolsv.exe under abnormal processes (or another Spooler exploit).
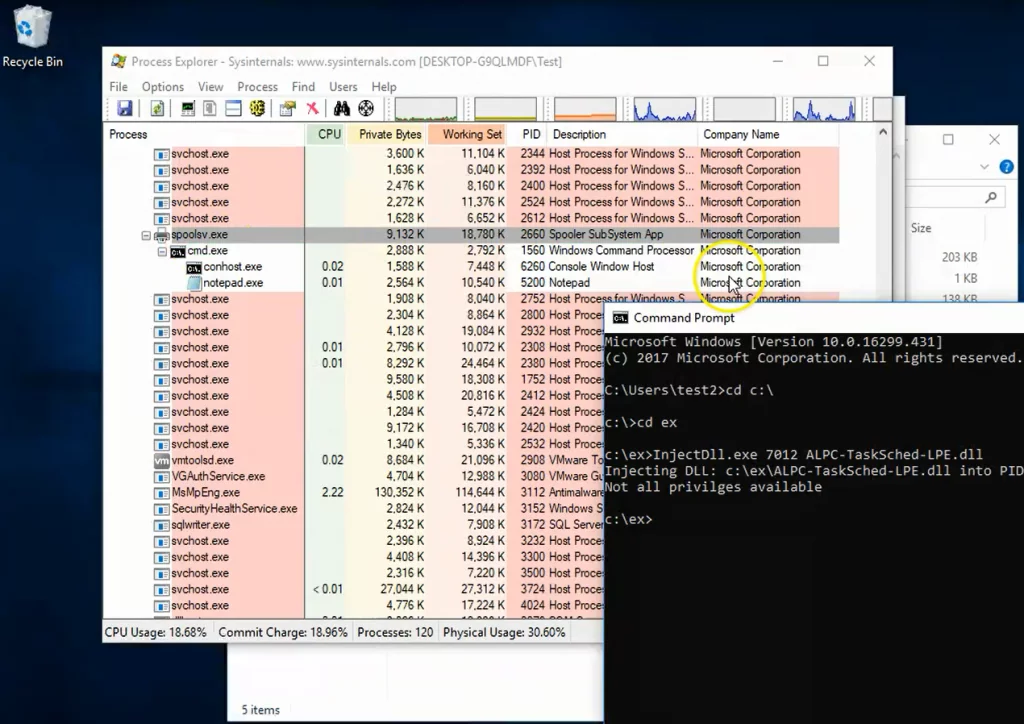
- Look for connhost.exe under abnormal processes (e.g. the Print Spooler).
Spoolsv.exe:
It is called Windows Print Spooler. This service spools print jobs and handles interaction with the printer. By disabling the Windows Print Spooler service you wouldn’t be able to print more than one document at a time, and any documents not immediately sent to the printer wouldn’t print.
Risk: If you turn off this service, you won’t be able to print or see your printers.
Fig: Checking for suspicious processes
Connhost.exe:
It is called Console Windows Host. This service is present in Windows 10 and using this, windows command prompt can show the same window frame like the other programs. It also allows you to operate the cmd prompt and users to drag and drop a file directly into it. This Microsoft Console Host program resides in “C:\Windows\System32” and should not be removed.
This process is closely related to windows CSRSS(Client Server Runtime System Service) a protected process you can’t terminate, which is responsible for console windows and the shutdown process, which are critical functions in Windows.
Risk: If you turn off this service, windows CSRSS service will also crash because conhost.exe runs under csrss.exe, so there is a high chance for the system to become unusable or shutdown.
Fig: Checking for suspicious processes
Recommendations for Microsoft Zero Day Vulnerability
- Do not remove/disable any original system processes without confirmation.
- Monitor and block any local users from gaining administrator privileges by using SIEM tools.
- Detect all the malicious processes by the name of genuine ones by using Behavioral Analysis.
- Network traffic analytics should continue to be used to detect anomalous traffic going across the network and to spot where users are behaving in a way that they historically don’t.
References
- https://www.kb.cert.org/vuls/id/906424
- https://doublepulsar.com/task-scheduler-alpc-exploit-high-level-analysis-ff08cda6ad4f
- https://threatpost.com/microsoft-windows-zero-day-found-in-task-scheduler/136977/
Author,