Bug Bounty vs. Penetration Testing: Which One Is Right for You?
Introduction to Web & Mobile Application Security Assessment
Web and Mobile applications have become an integral part of our lives, handling sensitive data and performing critical functions. Safeguarding the security of these applications holds utmost significance. In the realm of web and mobile app security assessment, two prominent approaches stand out: Bug Bounty programs and Penetration Testing.
In this blog post, we will explore the intricacies of these approaches, analyzing their advantages, drawbacks, and the key considerations involved in choosing the most appropriate one for your organization.
The History of Bug Bounty Programs
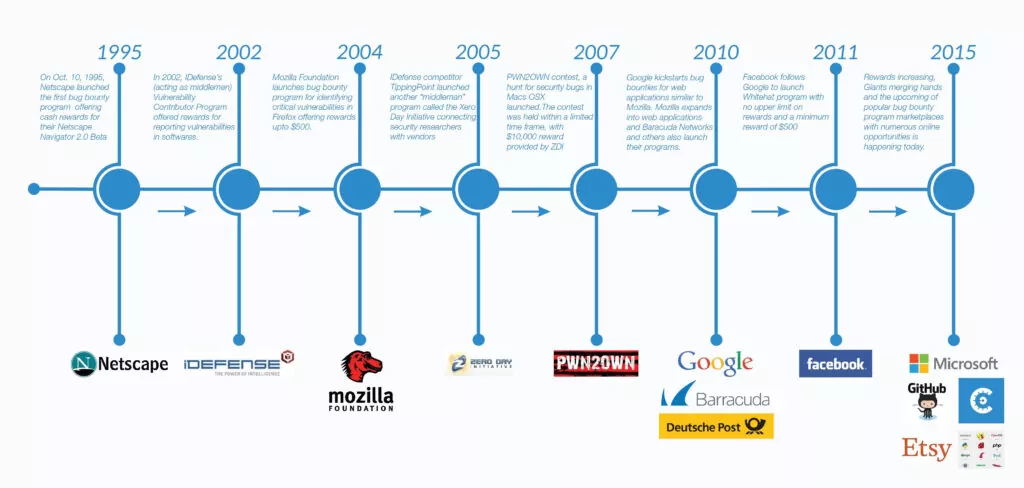
https://www.cobalt.io/blog/the-history-of-bug-bounty-programs
What is Bug Bounty Programs ?
Bug bounty programs, often referred to as vulnerability rewards programs (VRPs), provide incentives for ethical hackers to discover and disclose software vulnerabilities. They supplement traditional security measures like penetration tests and code audits. Hackers must adhere to program policies to avoid legal consequences, such as disclosing vulnerabilities prematurely. Bug bounty programs harness the collective intelligence of the security community, providing a broader range of perspectives and skills. Participants receive monetary rewards based on the severity of the vulnerabilities discovered. By responsibly reporting flaws, hackers contribute to overall security and prevent data breaches or disruptions. Bug bounty programs also boost hackers’ professional reputation and may lead to career opportunities in cybersecurity. These initiatives enhance software security, fostering a cooperative relationship between hackers and organizations for a more secure digital ecosystem.
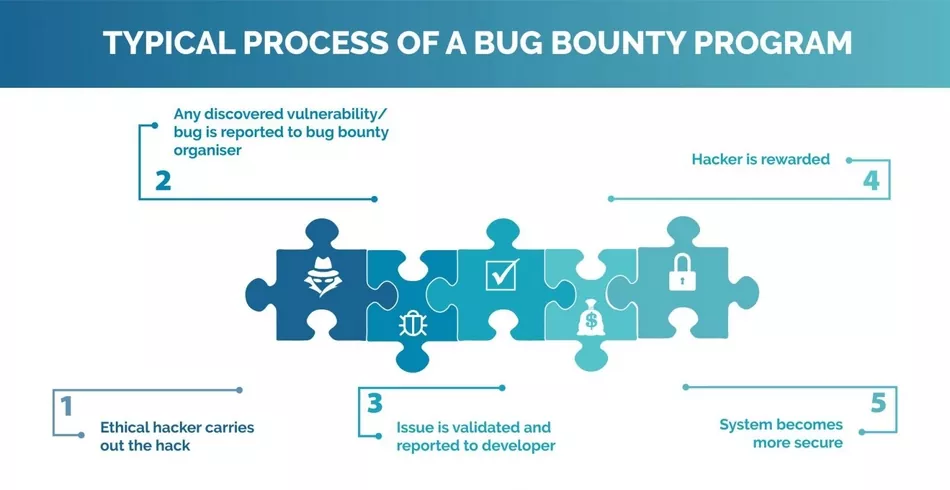
https://cybersecurityasean.com/expert-opinions-opinion-byline/bug-bounty-explained
Bug Bounty Programs
Bug Bounty programs have gained popularity in recent years as an effective way to identify vulnerabilities in web & mobile applications. In such programs, organizations invite security researchers, known as bug hunters, to discover and report security flaws in their applications. These programs operate on the principle of incentivizing researchers by offering financial rewards for valid bug reports. Let’s explore the key aspects of Bug Bounty programs:
• Bug Bounty programs engage a community of skilled researchers who scrutinize web & mobile apps for security vulnerabilities.
• Organizations define the scope of the Bug Bounty program, specifying the target platforms, types of vulnerabilities, and reward structures.
• These programs offer several benefits, such as accessing a diverse pool of expertise, encouraging continuous testing, and reducing the risk of undiscovered vulnerabilities.
• However, Bug Bounty programs also have limitations, including higher costs, potential for duplicate reports, and challenges in managing the influx of bug reports.
Penetration Testing
Penetration Testing, also known as Ethical Hacking, is a comprehensive security assessment approach that simulates real-world attacks to identify vulnerabilities in mobile applications. Skilled security professionals conduct controlled tests to exploit vulnerabilities and gain insights into the overall security posture of an application.
• Penetration Testing involves simulating various attack scenarios on applications to uncover weaknesses that could be exploited by malicious actors.
• Different methodologies, such as black-box, white-box, and gray-box testing, provide different levels of information and access to the testers.
• Penetration Testing offers advantages like thorough assessments, tailored testing based on the application’s specific characteristics, and detailed reports outlining discovered vulnerabilities.
• It also has limitations, such as requiring specialized expertise, time-intensive engagements, and the need for periodic testing to account for evolving threats.
Key Differences and Considerations Between Bug Bounty vs. Penetration Testing
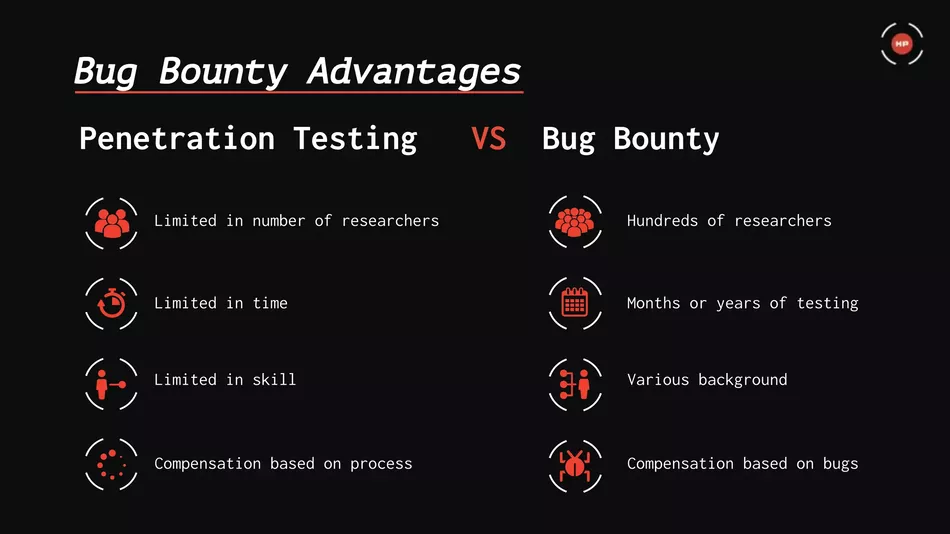
https://www.slideshare.net/HackenProof/bug-bounty-for-blockchain-projects-by-evgenia-broshevan-project-lead-at-hackenproof
While both Bug Bounty programs and Penetration Testing aim to enhance web & mobile app security, there are fundamental differences to consider when choosing between the two approaches. Key factors to weigh include:
Cost considerations:
Bug Bounty programs require financial investment for rewards and program management, while Penetration Testing engagements involve paying for professional services.
Expertise requirements:
Bug Bounty programs leverage the collective knowledge of security researchers, whereas Penetration Testing relies on the skills and expertise of hired professionals.
Time frame:
Bug Bounty programs operate continuously, allowing ongoing testing, while Penetration Testing projects have predefined timelines.
Scope:
Bug Bounty programs typically have a broader scope, targeting multiple vulnerabilities and platforms, while Penetration Testing can be tailored to focus on specific areas of concern.
Choosing the Right Approach
When selecting the most suitable approach for your organization, several factors come into play. Considerations include the organization’s size, budget, risk tolerance, and specific security needs. To make an informed decision:
• Evaluate your organization’s resources and budgetary constraints.
• Assess the level of expertise available in-house or the capacity to manage external engagements.
• Understand the criticality of your applications and the potential impact of security breaches.
• Define the desired scope and depth of the security assessment.
• Consider the scalability of bug bounty programs for large-scale applications or complex systems.
• Evaluate the sensitivity of your organization’s data and determine the level of risk tolerance.
• Assess the frequency of code changes and the need for continuous security testing.
• Take into account the legal and contractual considerations associated with bug bounty programs or penetration testing engagements.
• Consider the potential impact on customer trust and reputation in the event of a security breach.
Complementary Approaches
Bug Bounty programs and Penetration Testing are not mutually exclusive. In fact, combining these approaches can provide a powerful and comprehensive security assessment for your web & mobile applications. Bug Bounty programs can be used as a continuous testing mechanism, inviting external researchers to supplement the efforts of in-house penetration testers. This symbiotic relationship can improve the chances of identifying vulnerabilities and fortifying the security of your mobile apps.
Best Practices and Recommendations
Here are some best practices and recommendations for bug bounty programs:
Set clear goals and expectations:
What do you hope to achieve with your bug bounty program? Do you want to find high-severity vulnerabilities? Increase the number of security researchers who are aware of your products and services? Improve your security posture overall? Once you know your goals, you can tailor your program accordingly.
Define the scope of your program:
What are the assets that you want to be included in your bug bounty program? This could include your website, mobile app, APIs, or other software. It is important to define the scope clearly so that security researchers know what they are allowed to test.
Set up a clear and transparent reporting process:
How do security researchers report bugs to your program? What information do you need from them? How will you triage and respond to reports? It is important to have a clear and transparent reporting process so that security researchers know how to get their bugs heard.
Communicate effectively with security researchers:
Security researchers are your partners in improving your security. It is important to communicate effectively with them so that you can work together to find and fix vulnerabilities. This includes providing timely feedback on reports, answering questions, and resolving issues.
Track your progress and make improvements:
Once you have launched your bug bounty program, it is important to track your progress and make improvements. This includes tracking the number of bugs found, the severity of the bugs, and the time it takes to fix bugs. You can use this information to see how your program is performing and make changes as needed.
Use a bug bounty platform:
A bug bounty platform can help you manage your program, track your progress, and communicate with security researchers. There are many different bug bounty platforms available, so you can choose one that meets your specific needs.
Get buy-in from stakeholders:
It is important to get buy-in from stakeholders before launching your bug bounty program. This includes your security team, legal team, and management team. Once you have buy-in, you will be able to launch your program and start finding and fixing vulnerabilities.
Promote your program.
Let people know about your bug bounty program. You can promote your program through your website, social media, and other channels. This will help you attract security researchers to your program and find more vulnerabilities.
By following these best practices and recommendations, you can create a bug bounty program that is successful in finding and fixing vulnerabilities.
Conclusion
When it comes to web & mobile application security assessment, Bug Bounty programs and Penetration Testing are two powerful approaches that can help identify vulnerabilities and enhance the security posture of your applications. While Bug Bounty programs tap into the collective knowledge of security researchers, Penetration Testing offers comprehensive assessments conducted by professionals. Ultimately, the decision between Bug Bounty and Penetration Testing depends on your organization’s specific needs, resources, and risk tolerance. Consider the factors outlined in this blog post to choose the right approach and fortify your web & mobile app security.
Resources:
https://yogosha.com/blog/penetration-testing-vs-bug-bounty/#:~:text=Bug%20bounty%20and%20penetration%20testing%20are%20two%20tools,budget%20or%20the%20maturity%20of%20the%20targeted%20system
https://www.hackerone.com/penetration-testing/bug-bounty-vs-penetration-testing-differences-explained
Pentest or Bug Bounty: Which approach to choose for your security tests?
https://www.bugcrowd.com/blog/pen-testing-and-bug-bounty-which-when-why/
https://informer.io/resources/difference-between-pentest-bug-bounty
https://www.bugcrowd.com/blog/bug-bounties-vs-penetration-testing/
https://www.oneconsult.com/en/blogs/pentesters-diary/penetration-testing-vs-bug-bounty-programs/
https://www.hackerone.com/vulnerability-management/bug-bounty-vs-vdp-which-program-right-you
https://nextdoorsec.com/penetration-testing-vs-bug-bounty/




