Microsoft O365 Mobile Device Management (MDM)

In a hybrid work environment, employees may often work remotely using mobile devices. Since these mobile devices connect to corporate networks and resources, attackers can use these mobile devices to target corporate networks by exploiting vulnerabilities or weaknesses present in them. Organizations do not have the same kind of control on mobile devices (that are used remotely) as they have on their corporate devices used in the office environment. Microsoft Office 365 can help organizations with Mobile Device Management (MDM) via a specific set of security policies and settings to prevent any potential risk to their networks.
What is Microsoft O365?
Microsoft Office 365 is a large and diversified ecosystem that includes Microsoft Teams, Exchange Online, Azure AD, SharePoint Online, and OneDrive for Business, among other services. Office 365 security extends the core protections provided by Exchange Online Protection (EOP), which is the cloud-based filtering service that offers protection to organizations against malware, spam, and other email-related threats. In all Microsoft 365 organizations, EOP is provided with Exchange Online mailboxes.
Global admins are frequently responsible for many sub-admins and thousands of users and need to keep track of many things. Microsoft Office 365 helps global admins by reducing their administrative tasks to a great extent.
Microsoft has integrated multiple applications onto the cloud platform, which is geared toward productivity and collaboration. Microsoft O365 is a collection of cloud services that provide security, collaboration, and compliance in addition to intelligence, mobility, and analytics. Businesses all around the world are empowering their people by increasing productivity while lowering expenses, using emails, file storage, and secure chats for teams.
Key protections offered by Office 365 include:
- Anti-Malware Protection
- Anti-Spam Protection
- Anti-Phishing Protection
- Anti-Spoofing Protection
What is Mobile Device Management?
Mobile Device Management (MDM) for Office 365 is a built-in feature that helps an organization to secure and manage all mobile devices being used by the organization’s users or employees, including Android phones, iPads, iPhones, and Windows phones. Through MDM, the organization can set up and manage device security policies, erase a device remotely, and examine detailed device data.
When it comes to security, adopting cloud technologies involves a shared responsibility structure, with Microsoft liable for some controls and the client for others, depending on the service delivery model chosen. To safeguard a customer’s cloud workloads, the customer must carefully examine and implement the suitable architecture as well as enable the required set of configuration options.
The in-built mobile device management features of Office 365 can be utilized by organizations to securely manage corporate mobile devices used by their employees. They even can manage employee-owned devices in a BYOD environment.
How Can O365 Help with Mobile Device Management (MDM)?
Organizations can leverage Office 365 for managing mobile devices that are used by their employees because O365 provides the following useful features:
- Device Management: O365 allows organizations to set security policies like passcode or PIN requirements and block jailbroken/rooted devices from accessing their corporate networks and data.
- Conditional Access: O365 enables organizations to set rules that allow access to only the mobile devices that are managed by them and are compliant with their organizational policies.
- Selective Wipe: With O365, organizations can remove or wipe corporate data from mobile devices without affecting the employee personal data. Remote wipe is very helpful when employee devices are stolen or lost.
Office 365 MDM Policies for Mobile Devices
Administrators can allow or block employee mobile devices from accessing O365 resources with the help of the following policy controls provided by O365:
- Security settings: Admins can use security settings to enforce security using a PIN/Passcode (with specific length and complexity), automatic device lock when devices are inactive, and data wipe after multiple failed log-in attempts for device security.
- Data encryption: This feature is available in Windows Phones 8.1 by default and can be implemented in Android phones as well. However, it cannot be enforced on iOS devices.
- Jailbroken device detection: Admins can use this feature to detect and block employee mobile devices that are jailbroken (iOS) or rooted (Android) from connecting to corporate O365 resources.
- Managed email profile: This feature can help admins to block users from using O365 email if they are using a manually created email profile. This feature is for only iOS devices and creates a new profile automatically for iOS users to access their emails.
Several other policy settings are available depending on the type of mobile devices, for example, blocking app stores, blocking screen capture, blocking removable storage, etc.
Process of Deploying O365 MDM
Admins can deploy O365 MDM by using the following process. The process includes the following steps:
- Auditing existing mobile devices
- Activating MDM for O365
- Creating MDM policies
- Enrolling end-user mobile devices
- Ongoing management and reporting
CIS Benchmark for O365:
Organizations can use the CIS Microsoft O365 Foundations Benchmark to establish the foundation level of security for implementing Microsoft O365. For securely configuring a system, the CIS benchmarks serve as configuration baselines and security best practices.
The benchmark should be viewed as a beginning point rather than a complete list of all security configurations and architecture. Every organization must continue to assess its workloads, specific situation, and compliance requirements and customize its environment accordingly.
The CIS benchmark consists of two levels that have different technical specifications:
- Level 1: This CIS benchmark level recommends minimum security settings that are to be configured on any system without resulting in any interruption of service or reduced functionality.
- Level 2: This CIS benchmark level provides guidance on security settings for highly secure environments and may result in reduced functionality.
The CIS Security Benchmark for O365 is divided into the following sections:
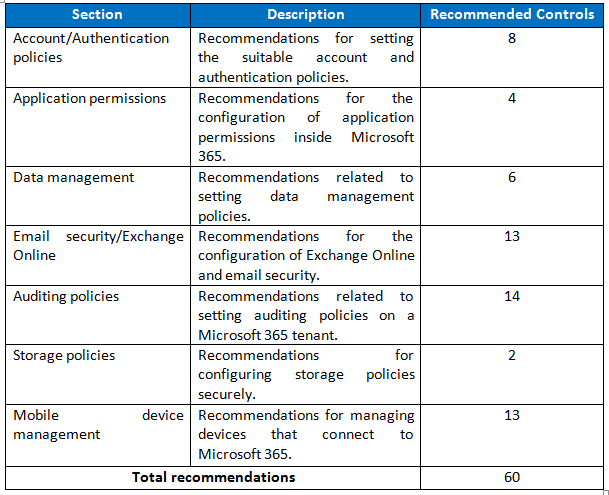
Organizations can use Microsoft Office 365 not only for performing business operations (e.g., making presentations, documentation, etc.) but also for managing remote devices that are used by their employees using various policy settings and features provided by Microsoft Office 365.
References:
https://workbench.cisecurity.org/
Configure your Microsoft 365 tenant for increased security – Office 365 | Microsoft Docs
Author,
Sachin Chavan
Attack & PenTest Team
Varutra Consulting Pvt.Ltd.




