Fundamental of Cyber Resilience & How It Affects SOC Services?

Introduction
The Security Operation Centre (SOC) is the backbone of every organization’s security defenses.
Back in the day, the SOC focused mainly on fulfilling and assessing regulatory compliance. However, since SOCs first arose in the mid-90s, they have evolved at a very speed and show no signs of slowing down.
The pandemic made us realize that many SOC teams have to rethink and restructure the way they work. For many, the focus became making sure that employees could work effectively from home, which resulted in the increased dependency on cloud-based applications and services. This change was prone to serious security risks and elevated the role of SOCs.
Investments required for loud-based infrastructure widened an organization’s already broad threat surface and left corporate networks exposed to new vulnerabilities. As SOCs continue to mature, they are exploring their objectives and making more concerted efforts to stop threats before they can cause damage, rather than simply detecting and responding to threats regularly.
While companies have started bringing associates back to the office since COVID-19 restrictions eased, remote working is here to stay and needs many changes to ensure operational resilience.
What is Cyber Resilience?
Cyber resilience is nothing but the ability to continuously deliver the intended outcome despite adverse cyber events.
 Source: Microfocus
Source: Microfocus
How Does Cyber Resilience Works Based on 5 Strategies?
An organization is cyber resilient when it can defend against cyber threats, have adequate cybersecurity risk management, and can accelerate guaranteed business continuity during and after cyber incidents.
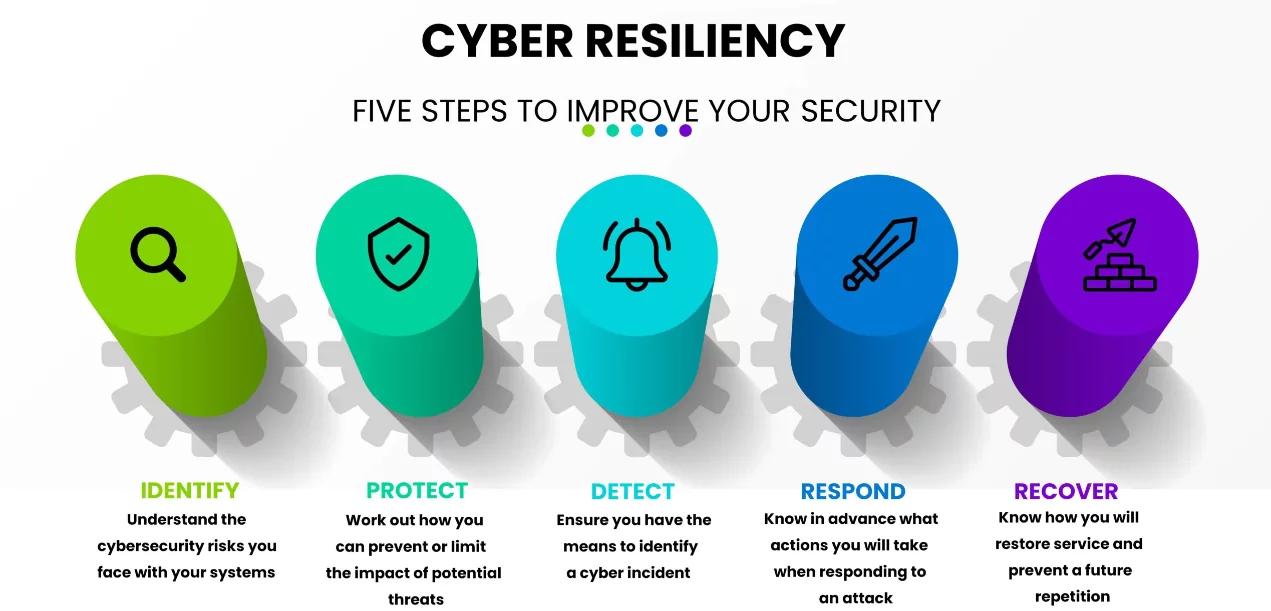
Source: AMHD Services
Identify
The identify phase is all about developing a greater organizational understanding of the existing cybersecurity vulnerabilities within your networks, systems, and data, as well as understanding the business context of that risk and the resources needed to support your core operational functions You’ll be able to better focus and prioritize your cybersecurity efforts and align them with your risk management strategy and business needs.
Protect
The protect phase is about flattening the appropriate cybersecurity measures to ensure better service delivery. These include the ‘first line of defense security applications to prevent, limit or contain the impact of potential threats.
Detect
The detect phase involves enabling the timely discovery of cyber incidents and defining the activities needed to identify and respond to a cybersecurity event.
Respond
The Respond function is all about taking the necessary action to deal with a live cybersecurity event and having incident management in place. It must support your organization’s capability to respond to and contain the impact of a potential cyber incident.
Recover
Recover is the final stage and important step, which looks at identifying the appropriate activities to restore service or operations affected by a cybersecurity incident and reduce the impact.
How Cyber Resilience Affects SOC Services and 5 Ways to Build In Cyber Resilience With Intelligent Threat Operations?
Having the best cybersecurity strategies in place will help us protect, detect and evolve from the latest Cybersecurity threats, which can be made more efficient by applying modern techniques and tactics as mentioned below.
Align cybersecurity priorities with business-value chains
In many organizations, business groups, IT departments, and risk functions frequently have conflicting agendas and unclear working relationships.
As a result, many organizations attempt to follow and apply the same cyber-risk controls everywhere in a similar manner. Most of the time, this results in a waste of time and money, but it can also result in a lack of priority for assets and functions critical to the business-value chains.
Security operations teams (SOC) must focus first on the business problem and consider the whole enterprise to identify and prioritize the top risks.
Cybersecurity budgets often compete with technology investments for limited funds, so security teams need to consider the entire enterprise, collaborating with a multidisciplinary team to consider security problems and risks from the standpoint of enabling the business.
Identify critical business resources to prioritize protection
A primary focus of cyber resilience is the identification and protection of the organization’s digital crown jewels. In any given enterprise, some of the data, systems, and applications are more critical as compared to others. In addition, some are more exposed to risk, while others are least likely to be targeted. The organization must focus its strongest protections on its most critical systems and assets, especially assets that meet a trifecta of criteria: highly critical for the business, exposed to greater risk, and likely to be targeted.
Conduct intelligence gathering to determine attacker motives
While threat modeling, risk reviews, and vulnerability analyses must focus on the value of an asset to the organization and potential shortcomings in defenses, the profile of adversaries who may attack the organization are also important. Threat Modeling states about attackers and how they operate, which helps to identify new gaps and direct funds to strengthen weak points that are likely to be targeted.
This is an intelligence data-driven process, but it’s critical. While an organization will want to have internal expertise, bringing in security consultants can help an organization with a second set of eyes. In addition to, third parties that specialize in threat intelligence and monitor a wide range of sources and most likely have resources that the average business may not afford.
In the end, improving defenses allows organizations to engage and stop attackers in real-time by combining threat intelligence, machine learning, and analytics resources within the IT function.
Create a cybersecurity capability to support resilience like SIEM Solution
SIEM systems provide real-time detection of known attacks. With the help of a framework like MITRE ATT&CK, which provides us a reference model for measuring the effectiveness of an organization’s detection strength and the vital impact of deploying other security technologies. Anomaly-detection models look for behavior that digresses from typical patterns, such as an unusual behavior by a user. An organization with an active-defense posture uses both SIEMs and anomaly-defense systems to provide more comprehensive threat detection.
Make a Note of Everything
Make a note of the latest cyber security threats through social media, newsletters, and forums, and have a periodical risk assessment, VAPT, to find and close the gaps on time to safeguard the organization from threats like Zero-day attacks.
Author,
Parag Bhamare,
Asst. Manager SOC,
Varutra Consulting Pvt. Ltd.