Hibernate Query Language (HQL) Injection

HQL is the abbreviation for Hibernate Query Language. Hibernate can be classified as ORM or Object-Relational Mapping. It maps class definitions with similar SQL tables that are present within the source code. It is an object-oriented query language that is similar to SQL. However, it works with persistent objects and their properties instead of operating on tables and columns. Hibernate translates HQL queries into conventional SQL queries that act on the database.
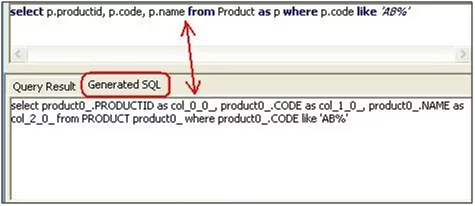
Figure 1: Hibernate query language
ORM (Object Relational Mapping)
Object-Relational Mapping (ORM) is a well-known programming technique that helps to convert data between object-oriented programming languages (e.g., C#, Java, etc.) and relational databases. RDBMS represents the data in tabular format, but OOPS follows the concept of objects, and it represents data as a connected graph of objects.
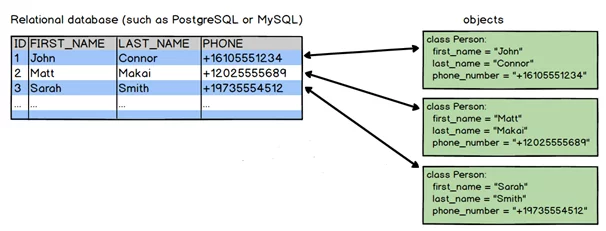
Figure 2: Object-relational mapping
SQL database management systems (DBMS) can only store as they are not object-oriented. They can even manipulate scalar values like integers and strings, which are organized within tables. Therefore, object values must be converted into groups of more exact figures for storage in the database (and convert them back upon retrieval), or only use simple scalar values within the program.
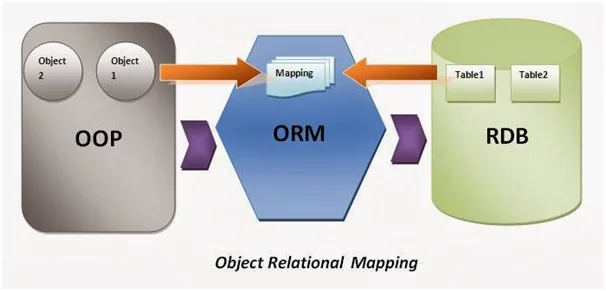
Figure 3: Object-relational mapping
Hibernate
Hibernate is an Object-Relational Mapping solution that is used for JAVA. It maps Java classes to database tables and Java data types to SQL data types, giving you retrieval facilities and data queries.
Whenever we write a query, it does not directly go to the database. It is first going to hibernate engine that parses the query and interprets it, later it gets converted to SQL. Any error message we get during testing can come from either hibernate engine or database.
SQL Injection versus ORM / Hibernate Query Language injection
HQL has some restrictions over SQL injection, for example – No union, no function to create easy delay, no system function, no metadata tables available, etc.
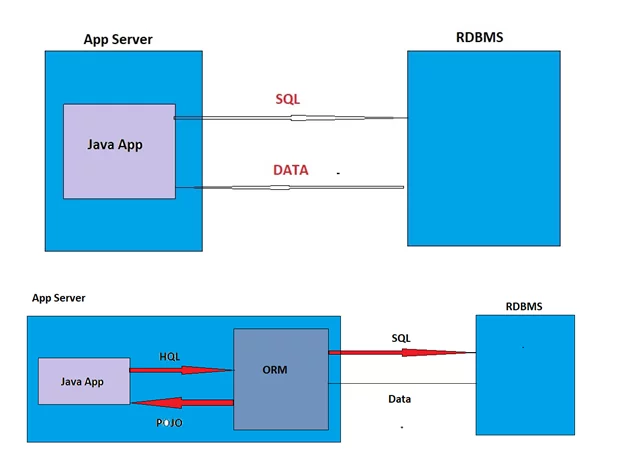
Figure 4: SQL vs. HQL
Approach and Methodology For Hibernate Query Language injection
HQL injection is an attack that uses SQL Injection. This attack is carried out against an ORM-generated data access object model. It is an attack identical to a SQL Injection, but the injection vulnerability exists in code generated by the ORM layer.
If an injection is present in HQL syntax, it cannot be exploited as a standard SQL injection. It happens because the HQL language has its syntax, which is more restricted (for example, there is no way to query unmapped tables). If you are getting “org.hibernate.QueryException” after inserting some special characters in any application parameter, then it is possible that HQL Injection is already present.
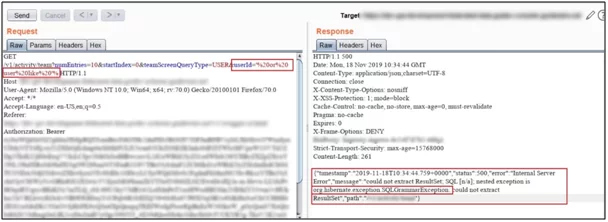
Figure 5: HQL error
As proceeding further, we need to break the syntax and form our payloads to exploit it further. Different RDBMS uses different escaping techniques. For example – MySQL Database escape character ‘with \*. Please note HQL does not support UNION queries. Also, the malicious input will always be between the percentage symbols.
Example:
HQL List Columns
from Student
where name like ‘%’
and DOESNT_EXIST=1 and ”=’%’ —
and register= true
HQL Error Based
from Student
where firstName like ‘%11′
and (select password from User where username=’admin’)=1
or ”=’%’
and register = true
Conclusion
In this post, you get to know that an additional layer of security is not provided in Hibernate. As a result, hackers can easily break through the HQL language to compromise data. It is possible because the old tricks are still fully functional to break out through the HQL language.
Reference:
https://en.wikipedia.org/wiki/Object%E2%80%93relational_mapping
https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/HQL%20Injection.md
https://www.fullstackpython.com/object-relational-mappers-orms.html
https://www.tutorialspoint.com/hibernate/hibernate_query_language.htm
http://interviewquestionjava.blogspot.com/2014/01/framework-orm-object-relational-mapping.html
https://blog.h3xstream.com/2014/02/hql-for-pentesters.html
Author,
Prashasti Rikhari
Attack & PenTest Team
Varutra Consulting Pvt. Ltd