Secure Software Development Lifecycle (SDLC)
Since the threat landscape in the software development ecosystem is ever-evolving, we need to reconsider the security controls used throughout the software development and delivery process to protect software against attackers. Organizations must ensure that they provide not only innovative software products but also ensure that security is embedded throughout the Software Development Lifecycle (SDLC). To achieve a secure Software Development Lifecycle (SDLC), it is essential to take some important measures and use the right tools for the job. This helps to integrate security in every phase of the SDLC.
What Is a Secure Software Development Lifecycle (SDLC)?
Security is integrated and implemented in all phases of the software development and delivery cycle in a secure SDLC (SSDLC). In the SDLC, security issues are brought up in the later stages, which requires more time and cost to fix them. The SSDLC helps developers to identify and address security issues as soon as possible in the initial stages itself without any delay.
To achieve an SSDLC, organizations must adopt a DevSecOps approach and the latest set of security patches and processes. With this new approach, all aspects of the SDLC are addressed, and security is embedded in the entire software development process, helping in detecting and remediating security issues faster. The SSDLC requires updating processes to enable frequent and early testing of security, the integration of automated application security testing tools throughout the development lifecycle and making the DevOps, security, and development teams work together towards the common goal of secure software development and delivery.
As per the State of Application Security Report shared recently by Forrester, security professionals working in software development companies are working to achieve an SSDLC and are using testing tools early in the development process.
Importance of Securing the Software Development Lifecycle (SDLC)
Securing the SDLC becomes important because attackers are targeting the application layer over the past years. According to the report on reducing enterprise AppSec risks published by the Ponemon Institute, the highest level of security risk is associated with the application layer.
What concerns organizations the most?
A recently published research report reveals that the most critical challenge for organizations is the inability to promptly detect vulnerabilities and threats along with the inability to perform quick patching in production. In the research study, most of the research participants, who were IT security practitioners, agreed that it may take a long time (even months) to perform patching in the production phase.
How to Achieve a Secure Software Development Lifecycle (SDLC)?
An important principle in the Secure SDLC is shifting security left, which requires the security and development teams to incorporate updated tools and security practices in the entire development lifecycle. By using shift-left security, organizations can save a lot of money, effort, and time because remediating security issues post production incurs more cost and effort than remediating them in the earlier stages of the SDLC.
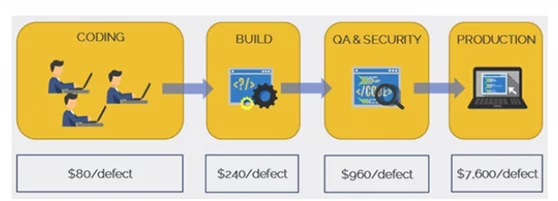
Cost of fixing a security issue
Integration of Security into all Secure Software Development Lifecycle (SDLC) Phase
In the SDLC, every step needs its own tools and security enforcement. To address potential risks immediately, integrate automated detection, prioritization, and remediation tools with the IDEs, code repositories, bug tracking tools, and build servers of your team.
Security is incorporated in all stages of the Software Development Lifecycle (SDLC):
#1 Planning
In the Planning phase, both security experts and developers must consider common risks that may attract attention during development and plan for it.
#2 Requirements and Analysis
In the Requirements and Analysis phase, various important decisions are taken such as which technology, languages, and frameworks will be used. In this stage, security experts must think about the vulnerabilities that may harm the security of the selected development tools to help make suitable security choices throughout the process of software design and development.
#3 Architecture and Design
In the Architecture and Design phase, security and development teams must follow the design and architecture guidelines to mitigate the risks that were identified and analyzed during the earlier stages. Addressing vulnerabilities in this stage will ensure that they do not damage the software in the development phase. In order to make the development process simpler and more secure, processes such as architecture risk analysis and threat modeling can be used.
#4 Development
In this stage of the SDLC, teams must follow secure coding standards. Developers should also consider security vulnerabilities in the code while performing the routine code review in order to make sure the project has the defined functions and features.
#5 Testing
This phase helps improve application security by including security testing and the use of automated DevSecOps tools. The DevSecOps approach allows continuous testing throughout the SDLC. To ensure your products and SDLC are secure from the beginning, frequent and early testing is necessary. This means teams must begin security testing in the initial development stages itself and ensure that testing does not stop at the later stages (deployment and implementation stages).
#6 Maintenance
As the real world is different from the testing environment, teams must be well-prepared to address previously unidentified risks or errors and perform configurations properly. They must follow security best practices, even after deployment and implementation, throughout software maintenance. Also, they must continuously update products and ensure they are protected against new vulnerabilities and are compatible with the modern tools that will be used.
Pay Close Attention to Open-Source Security
It is essential to address the risk of known vulnerabilities in open-source components to ensure a secure SDLC. Paying close attention to open-source security management in the SDLC is important because most software products today use up to 80% of open-source code. For effective open-source security management, Software Composition Analysis (SCA) tools can be used because they are specifically made to track open-source usage, alert developers in real-time about any open-source risks that are present in their code, and offer actionable prioritization and remediation insights along with automated fixes.
Shift Left to Ensure a Secure Software Development Lifecycle (SDLC)
The DevSecOps approach requires security and development teams to implement the right security practices and tools from the initial stages of the DevOps pipeline and incorporate them throughout all phases of the SDLC. By securing the SDLC, you can provide secure services and products to your customers without missing tight deadlines.
Since most attacks are targeted towards the application layer, the need for more secure apps increases. This makes a Secure SDLC a top requirement for organizations developing applications that you can achieve by making action plan to develop secure software.
Reference
https://www.whitesourcesoftware.com/resources/blog/how-to-secure-your-sdlc/
Author,
Rohit Sharma
Audit & Compliance Team
Varutra Consulting Pvt. Ltd.




