Navigating Top 5 Network Security Challenges With Zero Trust

Gone are the days when people regularly go to the office and work using the corporate network. Therefore, the hub-and-spoke network has branched out the corporate network to other branch offices and remote users for the past couple of years. In addition, they have designed and optimized means to connect with the centralized and secured data center. As a result, network services from the data center are expanding, leading to a security barrier between the trusted corporate network and the outside one. Therefore, the primary reason for an enterprise to integrate a Zero Trust strategy in 2021 was to modernize its cyber security program as it enables secure remote access for its employees and other third parties.
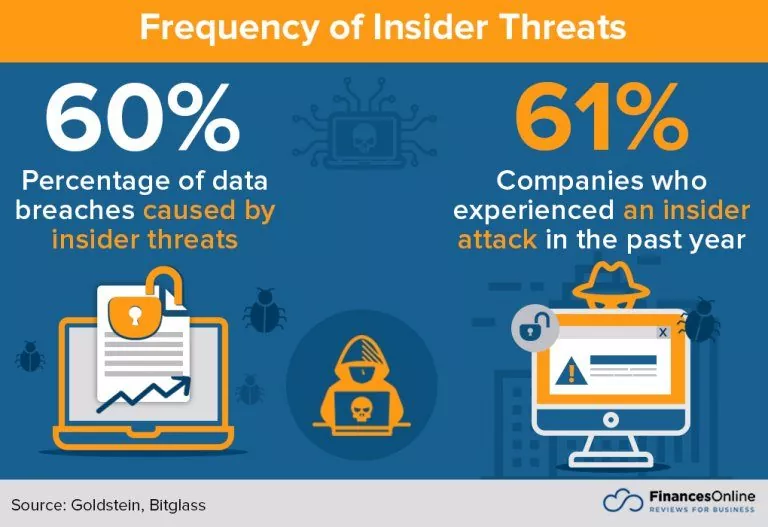
Previously, the security professionals used firewalls and other gateways to secure the network perimeters. Previously, the network’s infrastructure was based on an internal and trusted network vs the external and untrusted one. But gradually, there has been a rise in a new network security model, i.e., Zero Trust. It does not secure the network perimeter as its predecessors but requires every user inside who will access the network to get authorized before the access is granted. This security is necessary when organizations use cloud infrastructure and follow hybrid and remote modules. Many reports show that insider threats are responsible for around 60% of data breaches, which can be intentional and accidental.
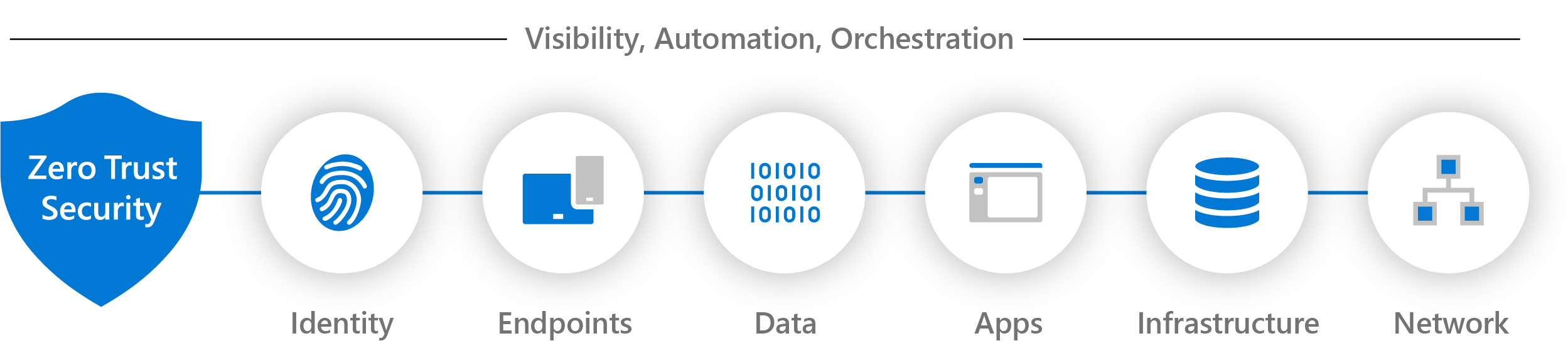
Navigating the Network Security Challenges with Zero Trust
Here are the top 5 network security challenges the organizations encounter and how zero trust helps mitigate them.
Unknown Risks Interrupting the Business and Causing Loss
As technology advances daily, threat actors are also looking for ways and means to breach the firewalls. Once these firewalls are breached, the data is in danger of exploitation. Traditional security measures are ineffective when it comes to preventing advanced attacks. Virtual firewalls can also be of no use once the threat actors penetrate as they can easily exploit the vulnerabilities. They can even infect other applications and systems connected to that network. Once the hackers achieve the critical mass, they can easily encrypt all the data, thus preventing the organization from properly functioning.
Mitigation with Zero Trust
Zero Trust only enables the authorized users to access the application or system, thus eliminating or limiting a large number of people from gaining access. In addition, it helps prevent insider threats, thus securing the network. A zero trust establishes a secure connection throughout the network by validating the authenticity of the user by its geolocation, device posture, IP address, and more. This procedure can be carried out without the user’s knowledge and interrupting their work.
Complexity Leading to Operational Inadequacy
Enterprises now have a scattered infrastructure which means they have both hardware and cloud-based infrastructure for the smooth transitioning of their business. It means not every application or device can be accessed by every employee. So, securing the network perimeter for this distributed infrastructure can be difficult and complex. In addition, many applications are not limited to a single cloud environment but have dependencies across a multi-cloud environment. It makes providing secure network connectivity between the cloud and data center very complex as it requires transit gateways, site-to-site VPNs, firewalls, and peering policies which all prove to be very challenging.
Limiting the Complexity with Zero Trust
Zero trust integrated with the network secures the private application, SaaS, and the internet using a single platform. The unified zero trust platform utilizes a single management console that is easy to configure and manage and offers better security than other perimeter security options. In addition, it simplifies the operations and troubleshooting by increasing the visibility across the clouds, users, and workload.
Poor User Experience Caused Due to Loss of Productivity & Collaboration
People are now working from various locations, i.e., remote work locations and corporate offices. Therefore, they need a good internet connection to do their work efficiently. However, the application is occasionally inaccessible due to any issue or responding slowly, leading to declining productivity. Also, the hub-and-spoke network infrastructure requires the remote and other branch offices to connect to the central office as it is the primary data center through firewalls with MPLs and VPNs for all the remote users. As this architecture extends to various locations, it increases the traffic in the network, leading to unpredictable latency and other issues, thus causing poor user experience.
Zero Trust Enhancing the User Experience
Zero trust provides direct connections to users irrespective of location and device while addressing user performance issues by enforcing policies. By doing so, they eliminate the traffic in the network that causes latency. The zero trust platform monitors every connected user; if there are any issues, it works to resolve them automatically. Furthermore, to enhance productivity and employee collaboration, it oversees all the applications, and in case of any problem, it immediately mitigates it with its DEM (Digital Experience Monitoring) capabilities.
Slow Transformation Due to Siloed IT Teams
It can be very challenging for the organization and other teams like operations, IT, networking, and more to suddenly replace the hardware infrastructure and move to a cloud-based and zero trust solution. It embarks a significant shift from the traditional way of operating. In addition, changing the mindset of people who are used to working in a certain way can be very challenging. People may think they lack the skill and knowledge to work on cloud-based applications.
Zero Trust Tackling the Functional Silos
The working of security and operation management is simplified with zero trust. Earlier, the network, operations, and security team needed to collaborate to transition away from a perimeter-based approach. But transitioning reduces the IT team’s burden as earlier they had to monitor, maintain and supervise the hardware, but cloud-based zero trust is easily manageable.
Inefficient Arrangements Increasing Cost of the Infrastructure
Earlier, the network infrastructure was quite expensive due to protocols like MPLs and required constant maintenance. Also, additional bandwidth that is needed due to unnecessary traffic causes an increase in the cost. There is also the cost of installation, configuration, troubleshooting, and testing. But this cost can be cut by moving to cloud-based SaaS applications.
Cost Cutting with Zero Trust Cloud Transformation
Switching to zero trust enables the organization to optimize its cost and improve its security by eliminating high-cost applications and infrastructure. The zero trust is fast, secure, and provides direct access and safe cloud-to-cloud interconnectivity. It does not require over-purchasing equipment and extensive planning and is designed to scale the business requirements.
Conclusion
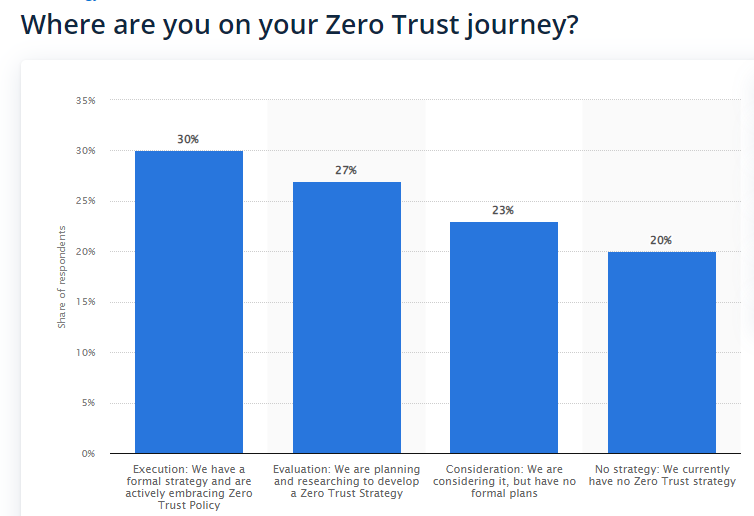
As of the January 2022 report of Zero Trust adoption status worldwide 2022 from Statistica, over 40% of respondents implement the Zero Trust strategy to improve the overall security posture and enhance productivity and user experience. At the same time, 35% of respondents are motivated by the idea of reduced security costs.
Organizations need to migrate from the old and traditional networking means to enjoy fast and secure connections to the zero trust solution. Unlike VPNs and firewalls, zero trust is solely based on the principle of privileged access. First, the connection is authorized, then the user can access the applications as they are now connected to the network.
Reference
https://www.zscaler.com/resources/infographics/five-network-security-challenges.pdf
Author,
Sanjana Yadav,
Marketing Department
Varutra Consulting Private Limited




