The Importance of Application Programming Interface (API) Security in the Age of Digital Transformation
An API, or Application Programming Interface, is a set of protocols and tools for building software applications. It provides a way for different software components to communicate and share information with each other, enabling developers to build more powerful and flexible applications. APIs have become increasingly popular in modern technology because they allow developers to quickly and easily integrate different services and data sources into their applications. This reduces development time and costs, while also enabling greater innovation and collaboration among developers. APIs are used in a wide range of industries, from Social Media and E-commerce to Healthcare and Finance, and have become a key driver of digital transformation and innovation.
https://blog.miraclesoft.com/api-security/
Overview of the Importance of API Security
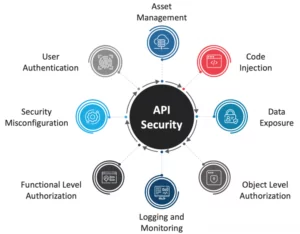
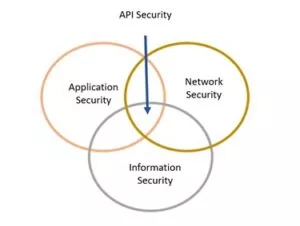
API security is critical in ensuring the integrity, confidentiality, and availability of data and services exposed through APIs. APIs act as the interface between different applications and systems, enabling them to communicate and share information seamlessly. API security is essential to protect against unauthorized access, data breaches, and other cyber threats that can compromise sensitive information.
 https://www.indusface.com/blog/what-is-api-security-and-why-is-it-important/
https://www.indusface.com/blog/what-is-api-security-and-why-is-it-important/
APIs are used extensively in Todays technology landscape, including mobile applications, cloud services, and IoT devices. As a result, APIs are exposed to a wide range of potential security threats, such as injection attacks, broken authentication and access control, and inadequate encryption.
API security is crucial in protecting against these threats, and it involves implementing security measures such as authentication, authorization, encryption, and rate limiting to ensure that only authorized requests are processed and that sensitive data is transmitted securely.
Here are 10 possible ways in which cyber attacks can occur through APIs:
There are numerous ways in which API (Application Programming Interface) cyber attacks can happen. Here are 10 common methods:
Authentication flaws
APIs can be vulnerable to attacks when there are flaws in the authentication mechanisms. This can include weak passwords, insufficient encryption, or unsecured transmission channels.
Authorization errors:
If an API allows users to access more data or functionality than they should be allowed, it can create a vulnerability for cyber attacks.
SQL injection:
Attackers can exploit weaknesses in the API code to insert malicious SQL statements into API requests, which can then allow unauthorized access to the database.
Cross-site scripting (XSS):
This attack involves injecting malicious code into an API response, which can then be executed on a user’s web browser, potentially stealing user data or credentials.
Malware injection:
Attackers can inject malware into the API code, which can then infect and compromise the systems that access the API.
Man-in-the-middle (MITM) attacks:
This attack involves intercepting API requests and responses to steal data, modify or delete data, or impersonate users.
Brute-force attacks:
These attacks attempt to guess usernames and passwords by repeatedly trying different combinations until the correct one is found.
API endpoint vulnerabilities:
APIs can have vulnerabilities in specific endpoints that can be exploited by attackers to gain unauthorized access to data or functionality.
Social engineering:
Attackers can use social engineering techniques, such as phishing or spear-phishing, to trick users into revealing sensitive information or credentials that can be used to exploit the API.
Securing APIs: Tools & Technologies Overview
There are several ways commonly used to secure APIs.
Authentication and Authorization:
Use secure authentication mechanisms, such as OAuth 2.0, OpenID Connect, and JSON Web Tokens (JWT) to ensure that only authorized users or applications can access the API.
Rate Limiting:
Implement rate limiting to prevent malicious or abusive users from overwhelming the API with requests. Tools like Kong, Tyk, and Apigee can help with this.
Input Validation:
Validate all incoming requests to the API to ensure that they meet the expected format and structure. This can be done using tools like JSON Schema or Swagger.
Encryption:
Use encryption to protect sensitive data transmitted over the API, such as personally identifiable information (PII) or financial information. HTTPS/TLS encryption can be used for this.
Firewall Protection:
Use firewalls to block unauthorized access and prevent attacks such as SQL injection or cross-site scripting (XSS).
API Gateways:
Implement an API gateway to act as a single entry point to the API, which can help to control access, rate-limiting, and provide additional security measures. Tools like Kong, Apigee, and AWS API Gateway can be used.
API Monitoring and Logging:
Monitor the API for suspicious activity, such as unusual traffic patterns or repeated failed requests. Use logging to record all API activity for auditing and troubleshooting purposes. Tools like Sumo Logic, Loggly, and Splunk can be used for this.
Containerization:
Use containerization technologies such as Docker and Kubernetes to isolate the API and limit its attack surface.
API Security Testing:
Conduct regular security testing on the API to identify vulnerabilities and ensure that it meets security standards. Tools like OWASP ZAP, Burp Suite, and Nessus can be used for this.
Continuous Integration and Deployment:
Use continuous integration and deployment (CI/CD) practices to ensure that all security updates and patches are quickly applied to the API. Tools like Jenkins, Travis CI, and CircleCI can be used for this.
Overall, API security testing is important for protecting sensitive data, preventing attacks, maintaining trust, and meeting compliance requirements. It is an essential aspect of software development that should not be overlooked.
Conclusion
APIs are essential for software applications to communicate with other systems. However, without proper security measures in place, they can be vulnerable to cybercriminal attacks. Securing your APIs is crucial for protecting your customers’ data, maintaining your brand reputation, and complying with regulations such as General Data Protection Regulation (GDPR) and Payment Card Industry Data Security Standard (PCI DSS). Breaching these regulations can lead to legal and financial penalties. To ensure API security, implement strong authentication and authorization mechanisms, encrypt data in transit and at rest, monitor and log API activity, and conduct regular security audits. API security is an ongoing process that requires constant monitoring and updating to stay ahead of evolving threats. Take proactive steps to secure your APIs and protect your business from cyberattacks to maintain your brand reputation and retain customers.
Research, References & Resources :
https://www.techtarget.com/searchapparchitecture/tip/10-API-security-guidelines-and-best-practices
https://blog.axway.com/learning-center/digital-security/keys-oauth/api-security-best-practices
https://www.techtarget.com/searchapparchitecture/tip/10-API-security-guidelines-and-best-practices
https://www.f5.com/labs/learning-center/securing-apis-10-best-practices-for-keeping-your-data-and-infrastructure-safe
https://www.orientsoftware.com/blog/api-security-best-practices/
https://www.indusface.com/blog/20-api-security-tips-every-enterprise-should-implement/
https://nordicapis.com/10-api-security-best-practices/
https://itcompanies.net/blog/api-attacks-vulnerabilities#:~:text=Common%20API%20Attack%20Types%20%26%20Vulnerabilities%201%201.,…%208%208.%20Insufficient%20Logging%20%26%20Monitoring%20
https:/curity.io/resources/learn/api-security-best-practices/
https://betterprogramming.pub/10-essential-tips-for-writing-secure-rest-api-e297990d48c5
https://restfulapi.net/security-essentials/
https://developer.okta.com/blog/2019/09/04/securing-rest-apis
https://www.toptal.com/nodejs/secure-rest-api-in-nodejs
https://docs.microsoft.com/en-us/azure/architecture/best-practices/api-design
https://www.neuralegion.com/blog/api-security/