7 Best Practices for Social Media Security and Privacy

Social media is an excellent digital platform for people to mingle and interact with each other. It is a platform for not only an individual but also organizations. They, too, can find great opportunities to promote and expand their reach. It is a powerful source of communication and can provide a robust global presence. Nowadays, several organizations are using social media as an essential tool for branding. They offer an excellent platform for engagement with customers and clients but can also damage if their security is not adequately managed. Therefore, organizations or individuals must take proper measures to maintain social media security and privacy.
As said, every new technology has its merits but challenges as well. For example, social media platform does help create brand awareness and engagement with the public, but it also has a specific risk as it creates open pathways that may not be secure.
Threats That Impact Social Media Security and Privacy
Here are the top 5 threats that affect social media security and privacy:
Social Engineering
It comprises a wide range of attacks that depend on taking advantage of human emotions and interactions to manipulate the victim. In addition, the attacks take advantage of the victims by giving away sensitive information. Therefore, this attack involves multiple steps to launch the attack successfully.
Phishing
The phishing attack is carried out either by SMS or email. The treat actor pretends to be a legitimate user or someone familiar so that the victim can easily fall prey to such an attack. The threat actors send an email or SMS containing malicious attachments or links. The virus or malware infects the system when the victim clicks on it or opens the attachment.
Malware
Threat actors promote malicious links containing social media malware to infect the system. There are different types of malware like spyware, ransomware, trojan, virus, and more. After the malware has infected the system, stealing sensitive information, taking total control of the system, or corrupting the system is very easy.
Impersonating a Brand
There is another significant risk of social media that impacts the brand. Threat actors can try to impersonate the legitimate brand page or group and trick the victims (employees and individuals) into providing sensitive information. Additionally, they may create a fake page and group, tricking the victim into revealing sensitive information, which can now be used against the brand impacting its reputation and even harming the victim.
Catfishing
Catfishing is a technique where the threat actor uses the information and image of a person and targets the victim into revealing sensitive and personal information. This attack is famous on social media as using a fake identity; the catfisher tricks the victim into associating with them and helps them with their goal.

Best Practises to Enhance Social Media Security
Following are best practices that will help individuals and organizations enhance the security of their social media platforms.
Enabling Multi-Factor Authentication
Multi-factor authentication is a security method to protect the organization or the individuals. It requires users to provide more authentication factors to prove they are legitimate or authorized to access the application, software, systems, server, account, or more. This extra layer helps provide security against identity theft, stealing sensitive information, and more. In most social media platforms, there is an option of privacy and security setting where users can activate or use various security methods that will help them secure their information on social media.
Avoid Re-using the Passwords
It is recommended that a person uses a different password for every account. It is advised that if one account is compromised, it will be easy for the threat actor to compromise all the victim accounts if they have the same passwords. Using a powerful password management tool is also suggested to track multiple passwords and ensure the passwords are tricky and cannot be guessed easily. Nowadays, on every platform where the user must register, creating a password with capital and small letters and special characters and numbers is suggested. This way, they can make a complex and unique password and take the measures to secure that password for that platform and ensuring not using the same for a different platform.
Regularly Updating Security Settings for All the Social Media Platforms
An updated version of the application or software is launched where the previously found bug or issue is resolved. Some are the case with any social media platform, so always keep in mind to update applications and software. The internet is filled with people looking for means to infect devices and steal data. Any carelessness from the user’s side can be an opportunity for the threat actors.
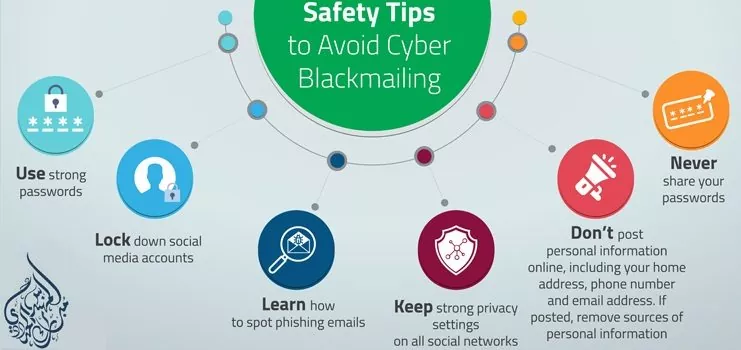
Limiting the Social Connection
Social media is a digital platform where one can socialize by meeting many people, but not everyone is a friend. Therefore, people should vary and be careful while making connections. Several reports state that threat actors create fake social media profiles to look for their targets. They can pretend to be a legitimate person and trick you into revealing sensitive information or convincing you to download malware on your device. So, be cautious and sensible with whom you connect on social media.
Oversee Social Media Security Risks
Be updated regarding any threat news regarding social media platforms and respond accordingly. In case of any vulnerability exploitation or hacking incident, check your account as that could lead to a data breach. Therefore, be careful of the data posted on the internet. Once on the internet, it always remains on the internet. Many researchers have said that several job recruiters have rejected candidates based on the data they have found on the internet, especially on their social media pages.
What do Phishing Attacks Looks Like?
One of the most famous attacks is phishing attacks. Therefore, people should be aware of the different types of phishing attacks that are going around. One should always be vigilant while making connections. Always check for direct messages on social media and don’t open any links or attachments from any unknown person. The attackers can trick you into the opening and downloading malicious attachments and infecting your device. This way, they can access the device and sensitive data.
Look Out for Spoofs
There are several cases of brand impersonation on the social media platform. One should be constantly vigilant, and if they come across such an incident, they should immediately report it to the authorities and inform other associated people. This way, we can prevent the threat actor’s efforts to fool people. Changing passwords from time to time and monitoring their social media accounts for any suspicious activity.
Conclusion
Security is a shared responsibility that starts with the user. They need to take basic cyber hygiene steps like installing anti-virus and anti-malware software in the system and updating their system regularly as there may be the latest security updates. Although the social media security issues are not new, as people’s engagement through social media has increased in the past few years, it has raised a red flag regarding security. One can only create awareness that will help the people maintain the security of the social media platform. Therefore, it is suggested to monitor their accounts for any security tips regularly and maintain the privacy of their account. As it is said, one’s safety is in their hand, and not get enamored by the threat actor’s tricks and endanger their data.
References
https://www.fortinet.com/blog/industry-trends/
https://privacysavvy.com/security/social/
https://usa.kaspersky.com/resource-center/preemptive-safety/
https://us.norton.com/internetsecurity-privacy-5-tips-for-social-media-security-and-privacy.html#
https://www.technology.pitt.edu/security/
Author,
Sanjana Yadav
Marketing Department,
Varutra Consulting Private Limited