Increased use of Multi-factor Authentication

What is Multi-Factor Authentication (MFA)?
Multi-Factor Authentication (MFA) refers to an authentication method that necessitates the user to provide more than one verification factor for gaining access to resources/information such as an application, online account, or information. MFA is an additional security feature for identity verification to reduce the threat of cyber-attacks. MFA combines more than one independent credential; namely what the user already knows (e.g., user credentials), and what the user has (e.g., a security token/pin), and what the user is (via biometrics).
Why is Multi-Factor Authentication important?
The prime advantage of MFA is it requires more than a username and password to verify the identity of a user, thereby enhancing the organization’s security. This is because user credentials like usernames and passwords are vulnerable to brute force attacks and any attacker can steal them. Implementing MFA(a fingerprint or physical hardware key) will reduce the chances of compromising the organization’s security.
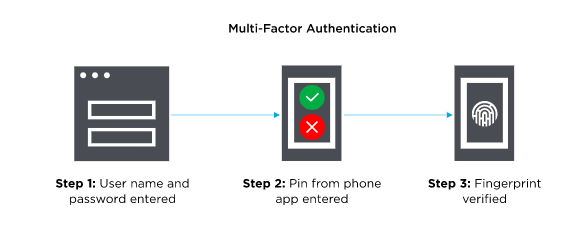
How Does Multi-Factor Authentication Work?
MFA requires extra verification factors than user credentials (User ID and password). The additional verification information/factor can be a One-Time Password received via email/SMS, a mobile app notification, etc. Users can login to an account or access restricted resources/information only when they pass through MFA.
MFA Authentication Methods
MFA works by combining two or more authentication factors or additional information. Four types of additional authentication factors can be used to verify the identity of a user in most MFA authentication methodologies:
- Knowledge (What the user knows)
It refers to the information that is known to only the user so it is used as a common authentication step. Examples of this authentication factor include passwords, PINs, OTPs, security questions, etc. Using this form of authentication alone can be dangerous because attackers can easily hack this information.
- Possession (What the user has)
This authentication method involves using a physical asset or information sent only to the user. Examples of this form of authentication include code sent to the user via SMS, Soft tokens (e.g., OTP, application notifications, etc.), Hard tokens (e.g., smart cards, USB tokens, etc.). Even if an attacker steals a user’s credentials, they cannot login/access restricted resources/information because of this authentication factor.
- Inherence (What the user is)
This authentication factor uses any biological traits of the user that were confirmed for login verification, including biometric verification methods. This includes verification of fingerprint scan, face recognition, voice, retina scan, and related other verification techniques.
- Adaptive (Where/ When the user is)
Adaptive authentication is a new way of authentication using a location and time. It is also known as risk-based authentication as it analyzes some additional factors considering the user’s behavior and context while authenticating. This authentication involves the use of Artificial Intelligence and GPS to highlight a user’s location with activities. This includes access from an unidentified device, public device, public network/ Wi-Fi, home location with time, office location with time, etc., which can help to calculate the risk level.
Scope of MFA
It is normally easy to implement MFA for employees at work. However, it is not the same for customers because customers want to have an easy and streamlined experience. They may not use apps or websites that have a complicated login process so they might not use MFA if they are allowed to skip it. Service providers are encouraging customers to use MFA for their account security purpose.
Multi-Factor authentication will break their dependency on using only passwords. Currently, it has been proven to provide higher-level security over just simply using passwords. By using the FIDO2 standard, MFA can be performed using password-less options like biometrics, security keys, and mobile-device-based solutions. This helps to improve the security of online services and end-users.
References –
https://www.onelogin.com/learn/what-is-mfa
https://searchsecurity.techtarget.com/definition/multifactor-authentication-MFA
https://www.pingidentity.com/en/company/blog/posts/2017/what-is-multi-factor-authentication-mfa.html
https://www.sugarshot.io/what-is-multi-factor-authentication/
Author,
Trupal Patel
Audit and Compliance Team,
Varutra Consulting Pvt. Ltd.




