What to Expect When You’ve Been Hit with Ransomware?

Ransomware is malicious software or malware that gains access to the system, denies you any admission to your network, system, or files, and demands payment in return. Cybercriminals make hundreds and thousands of bucks by exploiting the victims and have made it into a business.
Ransomware-as-a-Service
Ransomware as a Service is a service that is provided to cybercriminals with low technical skills so that they can carry out ransomware attacks. The malware is created by highly skilled threat actors and is available in the market for buyers with low risk and high gain motives.
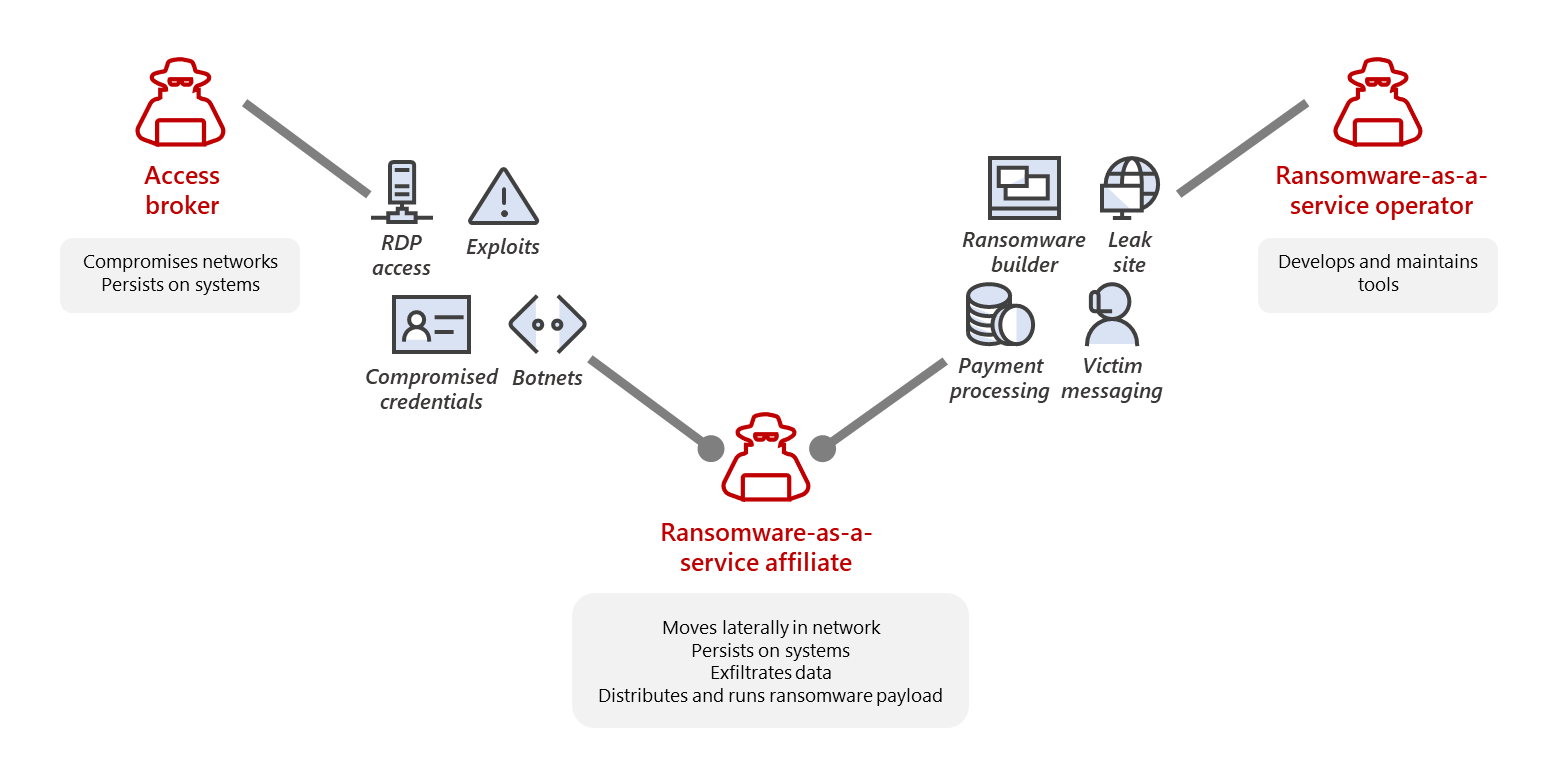 Source: Microsoft
Source: Microsoft
Steps to Follow After Ransomware Attack
Here are some steps to be followed in case of a ransomware attack.
Step 1: Neutralizing and Containing the Ransomware Attack
After the ransomware attack, determining its root cause and isolating it immediately is the first step. Next, it is recommended that you disable your internet connection. This way, you can prevent spreading ransomware in the entire systems/ devices connected to the same network. In the second step, you must assess the damage caused by checking the affected software, applications, and systems. This way, you will know how much damage is caused and what process you can follow for damage control. Thirdly, a contingency incident response plan should always help the organization deal with such a scenario. Finally, a ransomware attack on organizations can cause financial loss and question the organization’s integrity as the client data is compromised. Lastly, you should contact them so they can provide the proper guidance or steps on what to do.
Step 2: Investigation
Once the containment and neutralization of the ransomware attack are complete, you need to investigate the attack. If you cannot carry out this procedure, you can always seek assistance from the cyber security consultancies that provide such services. For example, Varutra is a security organization that offers various cybersecurity services like application security, cloud security, information security maturity assessment, SOC & global threat management services, and more.
- Threat actors may have been keeping a watch on the network, or it is most likely that they were already in the network for a few days or weeks. As ransomware is an attack, exploring the victim’s target to find sensitive information to demand high ransom is the motive.
- There are various means through which the threat actor can penetrate the network and gain access. Sending an email or SMS with a malicious link pretending to be a legitimate user is one of the most common methods. The network is infected with ransomware when the victim clicks on the link. There are chances that these threat actors are targeting multiple domains or accounts to launch a large-scale ransomware attack.
- The threat actors are well aware of the network. They may know all about the victim’s servers and endpoint of where the sensitive information and backups are present. There is also a chance that they may have already created a backdoor in the network so they can quickly come and go at their convenience.
- The encrypting of data is the main ransomware event. However, hackers may also try to locate the backup of the data to encrypt, delete or uninstall the backups, so they can quickly corner the victim into paying the ransom.
- Hackers may also try to learn and identify the security application installed in the system and disable it before the ransomware attack. It is only possible if they have been in the network for a couple of days or weeks studying the network before carrying out the attack.
- Cybercriminals try to encrypt the files when there is no IT security professional online, as encrypting a file takes a long time. So, most of the time, these take place during a weekend or night when no experts are present, and they cannot identify such procedure is being carried out.
- The launching of the ransomware attack is not the end. The main aim is to extort money, so threat actors try to blackmail the victim into exposing sensitive information online if their demands are not met, or they can launch another full-scale attack. Of course, they guarantee they will delete the data if the ransom is paid, but one can never be so sure.
Step 3: How to improve the security?
The following steps will help in improving your security posture.
- Create cybersecurity awareness among the employees and train them about basic cyber hygiene to maintain the security posture.
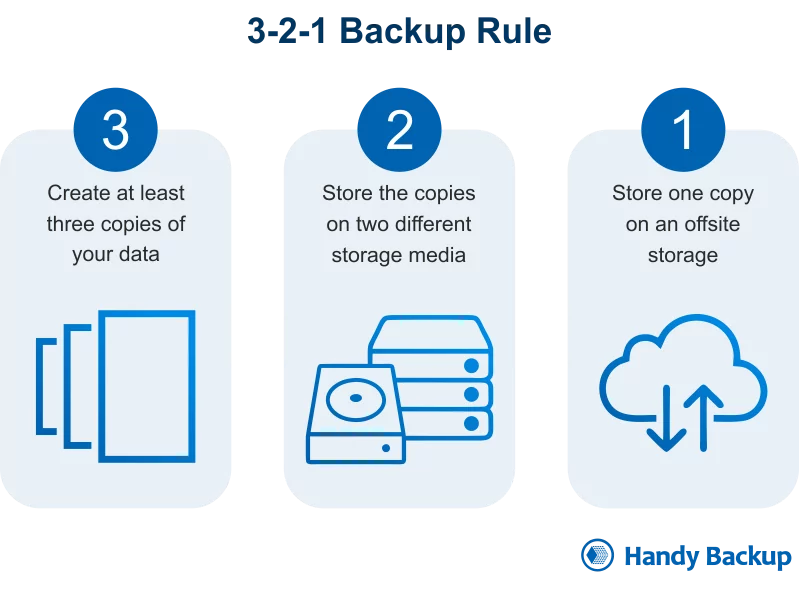
- Keep backups of sensitive information and update them regularly. A standard recommendation for backing up the data follows the 3-2-1 method. Create three (3) copies of data using two (2) different systems and keep at least one (1) offline.
- Monitor your network security 24/7 for any malicious activity as it will help prevent ransomware attacks before launching.
- As you know about the attack, disable the access of the attacked network from the other network or servers. It will restrict the movement of ransomware and prevent it from spreading to different servers and networks.
How to Avoid Ransomware Attacks?
The best way to avoid malware/ ransomware is to be cautious. Unfortunately, the ransomware distributors are tech-savvy and just waiting for the victim to make a single mistake to gain the system’s access. Here are some tips that may help in avoiding ransomware attacks:
- Updating all the software and applications installed in the system regularly.
- Installing anti-virus and anti-malware applications and regularly scanning the system for any malicious applications.
- Don’t click on any random link as it may be infected with ransomware or virus.
- Always create a backup of your data as a precaution.
- Always create an incident response plan beforehand as a precaution.
Conclusion
Handling the aftereffects of ransomware can be a troublesome and stressful experience. So, the organizations must take a step back and evaluate the whole scenario to check for any room for security improvement and learn from their past mistakes. If precautions are not taken, the attacker may make a second attempt. Therefore, organizations should have a recovery solution already prepared to deal with the effect of the attack.
Reference
Sophos
Pure Storage
FBI Official Website
Alvaka Networks
Kaspersky
Author,
Sanjana Yadav,
Marketing Department,
Varutra Consulting Pvt. Ltd.




