Cloud Security Can Help Improve Threat Detection and Reduce Burnout

Most industries are now moving towards work from anywhere (remote work) or hybrid. As a result, people frequently use various messaging apps like email, slack, texts, video calls, and project management tools to stay connected with their teams working from different locations. However, it may often lead to server or system fatigue due to overloading of notifications and results in employee burnout and not investigated alerts.
According to a global IT survey report from Orca Security, 60% of people receive more than 500 alerts a day. However, overloading such warnings can seriously implicate the business-like critical security alerts getting missed out, burnout among the cybersecurity professionals, and more. So, to improve the detection rates and provide extra assistance to the cybersecurity employees, organizations are now collaborating with cloud security services that help in threat intelligence accumulation, effective detection rates, and minimizing the impact and time taken in recovery from data breaches.
Definition of Cloud Security and Its Major Security Risks
Cloud security can be defined as the security practices and strategies taken to protect the data and applications hosted in the cloud. Occasionally, even well-secured data in the cloud can encounter cyberattacks; therefore, organizations take means and precautions to prevent such attacks. Furthermore, cloud computing is considered more secure than on-premises computing; thus, more and more businesses are moving towards cloud computing.

Source: Norton
Here are some significant cloud security risks:
- Data getting leaked or exposed.
- Unauthorized access from third-party trying to gain access to the internal communication or information.
- The employees have access to all the internal information.
- Threat actors use malicious attacks like DDoS attacks, malware infections, etc., to cripple the infrastructure of the cloud.
The main objective of cloud security is to reduce the threats posed by the threat actors and protect the data.
How are New Vulnerabilities Created Due to the Expansion of IT Infrastructure?
Digital transformation by implementing the latest technologies for better services and products has become a core of most businesses. Moreover, as the business’ infrastructure is expanding, they are collaborating with the cloud providers for their services, extending the attack surface.
The definition of attack surface proposed by the US National Institute of Standards and Technology is “The set of points on the boundary of a system, a system element, or an environment where an attacker can try to enter, cause an effect on, or extract data from, that system, system element, or environment.” It means when the attack surface expands, more endpoints will be created, making cloud security more complex and creating new opportunities for potential breaches complicating the cybersecurity team’s work.
Cybersecurity Personnel Trying to Keep Up With the Increasing Notifications & Alerts
A KPMG and Oracle report stated that 40% of CISOs’ primary challenge is detecting and reacting immediately to cloud-related incidents. While cloud infrastructure contains a lot of information, so sometimes they even overload during events. In addition, as more and more applications and devices are added, more alerts and occasions when a critical warning is missed due to a human error. According to CISCOs 2020 Benchmark Report, many organizations are falling behind in investigating alerts. In 2020, the alert investigation percentage plunged to 48% compared to 56% in 2017.
The Gap in Cybersecurity Skills
According to a report from the ISSA (Information System Security Association) and analyst ESG (Enterprise Strategy Group), there are shortages in three groups, i.e., security analysis and investigation, cloud security, and application security. In the report, there is a mention of skill shortage affecting the well-being of the employees. Around 38% of the employees mention that shortage of skilled cybersecurity professionals leads to more employee burnout.
Burnout is not the employee problem but a problem at the organizational level. In a report from 1Password, cybersecurity professionals who are burned out are more likely to miss out on some alerts, look past specific security policies, and possibly do the bare minimum at work.
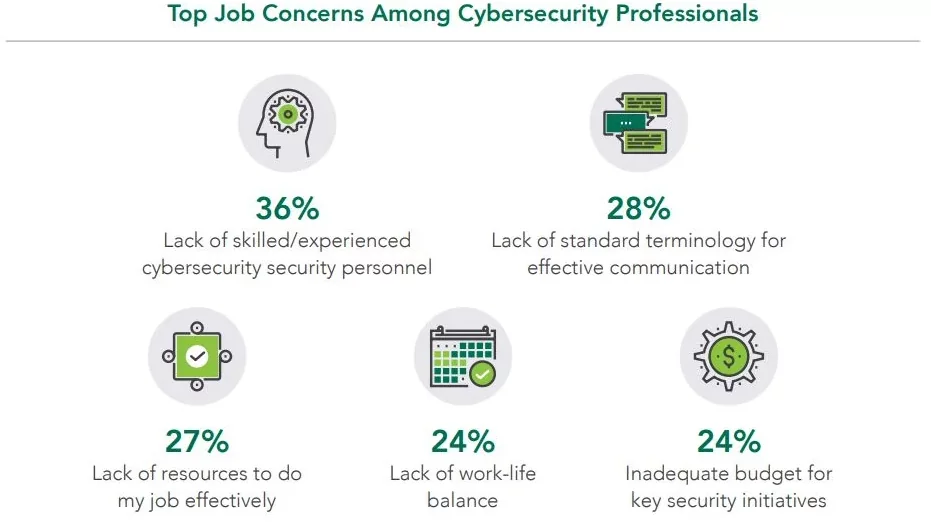
Source: Tech Monitor
How Can Cloud Security Help in Creating a More Effective Response Model?
Cloud security uses analytical monitoring and data science to design an effective security response model. It provides a consolidated view of risks and threats that results in alerts being reflected immediately. It means there won’t be extra time invested in the investigation of anomalies individually. The key features of cloud security consist of continuously monitoring the activities and configuration to identify threats and automatically respond to them by eliminating them.
Key Features to be Included for the Organization’s Cloud Security
Essential features are recommended to be included in the cloud security strategy for any organization.
Encryption
Encryption is a form of scrambling the data so that only an authorized person can access the data and understand it. For example, if a threat actor gains access to the organization’s cloud and obtains unencrypted data, it can be used for any malicious action. Still, if the data is encrypted, the threat actor won’t be able to use the data.
IAM (Identity and Access Management)
Using the IAM, the organization can track the users authorized to access the data and who will be denied. It is considered extremely important for cloud computing because the user’s identity can confirm their access privileges. In addition, identity and access management help reduce the threats of unauthorized personnel gaining access to the internal assets and authorized employees exceeding their benefits.
Cloud Firewall
A cloud firewall is an extra layer of protection around the cloud assets that block malicious traffic. Unlike the traditional firewall, it is a virtual security barrier hosted in the cloud infrastructure. It blocks malicious bot actions, DDoS attacks, and vulnerability exploits.
Proper Cloud Configuration
When an organization does not correctly configure its security settings, it can result in a data breach. Misconfigured cloud servers directly expose the data on the internet. Therefore, properly configuring the cybersecurity setting on the server must prevent the data from getting exposed.
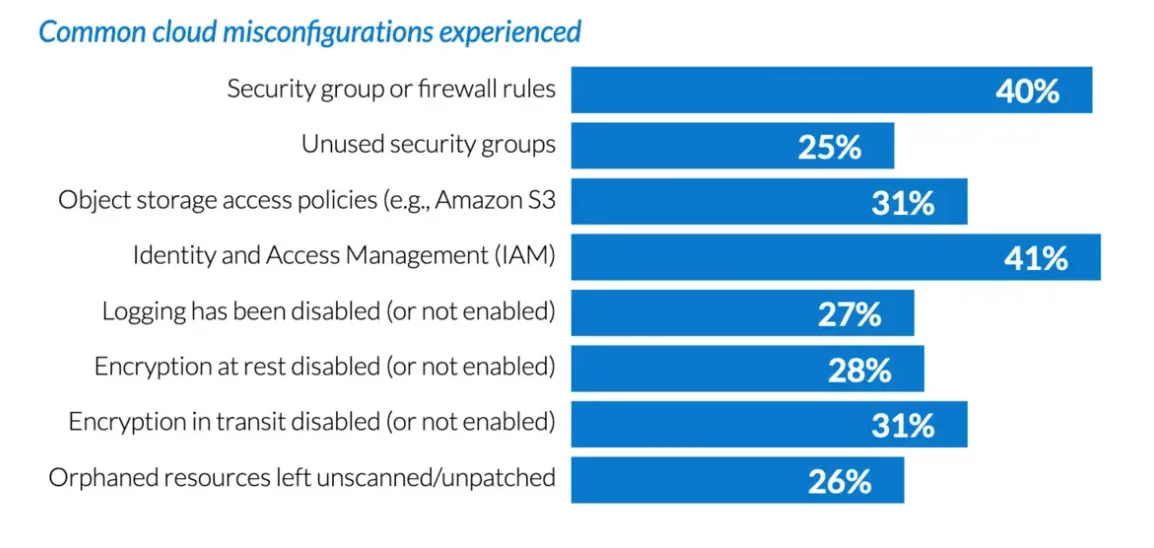
Source: Infoworld
Consistent Security Policies
It is mandatory for an organization to follow the proper security measures across the company’s cloud infrastructure, including private, public, and on-premises architecture. The threat actor may exploit any vulnerability if the security policies are inconsistent. It may result in the threat actor gaining access to the data and using it with some malicious intent.
Conclusion
Implementing the strategies in the cloud will enhance the security of the cloud, but sometimes it is also not enough. One should also take some steps to prevent a data breach. It is highly recommended that the organization create a backup for their cloud data on a different server or on-premises as a preventive means. If the data is lost or tampered with, the company will not lose all its information. It is also recommended that organizations should educate their employees and work on spreading cybersecurity awareness to maintain a proper security posture. There have been reports that many data breaches are due to phishing attacks or unknowingly downloading the malware due to a lack of awareness. Educating employees about security hygiene can minimize such risks by directly operating in the cloud.
Organizations can also seek the assistance of cybersecurity service providers like Varutra, who offers cloud security assistance. They provide security methodologies and services like cloud pen-testing, cloud security configuration audit, and cloud infrastructure architecture review that uphold the long-term evolution of the cloud and secure the cloud infrastructure.
Reference:
Oracle
Cloudflare
NIST
Author,
Sanjana Yadav,
Marketing Department,
Varutra Consulting Private Limited