CRLF Injection
Before going into details on what and how to find and perform CRLF injection and what are the measure one should take from this to happen, we will first get to know a little bit about what exactly is CRLF (Carriage Return Line Feed) and why it is used.
So, what exactly is CRLF (Carriage Return Line Feed)?
In CRLF, CR stands for Carriage Return and LR stands for Line Feed. Carriage Return is represented by “\r” (ASCII value 13) and Line Feed is represented by “\n” (ASCII value 10).Carriage Return refers to end of a line, and Line Feed refers to a new line. Thus, CR and LF both combined are used to denote ending of a line.
When a request is sent to a web server, it sends back a response containing HTTP headers and the content. These HTTP headers and the HTML response i.e. the web content in the response from the server are separated by a combination of some special characters; these characters are CR and LF.So basically, CRLF is used to separate HTTP headers and HTML content in a response from the server.So, in short CRLF is used to denote a new line.
CRLF characters are used by most of the servers like Microsoft IIS, Apache, and all others. Mostly in Windows both CR and LF are used to terminate a line, whereas in LINUX/UNIX only LF is used. Many protocols like MIME, NNTP and most widely HTTP use CR-LF sequence. The HTTP protocol always uses CR-LF sequence to terminate a line.
What is CRLF injection?
CRLF injection vulnerability attack is where an attacker will try to inject a CRLF sequence into an unexpected input field of an application. This input of an unexpected CRLF sequence will trick the application to perform in such a way where potential security flaws may arise. Using CRLF injection the attackers can further exploit various vulnerabilities like XSS (Cross-Site Scripting), Web cache poisoning, Script injection, Phishing attacks, client session hijacking, etc. The vulnerabilities can range from medium to high severity.
There are 2 most important use cases for CRLF injection. First one being Log poisoning and the second one is HTTP response splitting.
- Log poisoning: In this case the attacker will try to falsify the log entries by adding an end of line and an extra line. This will confuse the system administrators or hide other attacks.
- HTTP response splitting: In this case the attacker will use CRLF injection to add HTTP headers to the response. This will help in performing other attacks, like XSS which can further lead to information disclosure.
Cause of CRLF injection:
CRLF injection is mostly found in HTTP request. This may arise when a web application accepts a user input without properly validating it from an untrusted source.
How to check if the website or web app is vulnerable to CRLF injection or not?
For checking if a particular website is vulnerable to this type of injection, first we have to check whether there is any user input field in that page, that is later being used to set the response cookie. This is the key indicator that something is there in the application when we can manipulate in setting a cookie. If there is any input of this kind, then we can check for any “GET” method and then try to insert %0d%0a into that GET response and check whether the website is vulnerable to CRLF injection.
Examples of CRLF:
- Request: GET /%0d%0aSet-Cookie:CRLFInjection=P HTTP/1.1
Look at the above GET request, if the attacker is able to successfully inject CRLF sequence into this website then the attacker will be able to set the cookie for the website as shown above.
- Let’s look at another example where the attacker will successfully be able to add logs in a system to trick the system administrator.
Log: 123.123.123.123 – 08:15 – /index.php?page=home
Suppose there is a log file in an admin panel. The pattern of the output stream is “IP-Time-Visited path” as shown above.
If the attacker can successfully perform CRLF injection into this file, then he will be able to add fake log entries. To do so he will try something like what is shown below to change the request.
Request: /index.php?page=home&%0d%0a127.0.0.1 – 08:15 –
/index.php?page=home&restrictedaction=edit
After successfully executing this request the log entries in the admin panel will look like:
Logs: 123.123.123.123 – 08:15 – /index.php?page=home&
127.0.0.1 – 08:15 – /index.php?page=home&restrictedaction=edit
Thus, by exploiting CRLF injection the attacker was able to successfully add fake log entries into the admin panel log file.
Impacts of CRLF injection:
There are lot of impacts and scenarios that can arise from exploiting CRLF injection. Like CRLF injection can be used to inject malicious scripts and perform XSS, it can also be used to set client-side cookies, etc. We will not discuss all the impacts; here we will just try some of them.
- Client-Side Cookie injection: Here in this scenario we are trying to set a fake cookie in the application by exploiting CRLF injection vulnerability.
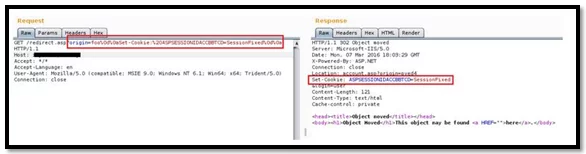
- Redirection and javascript execution: In this scenario we are injection a malicious script in a redirection request in combination with the CRLF characters and trying to bypass the filter.
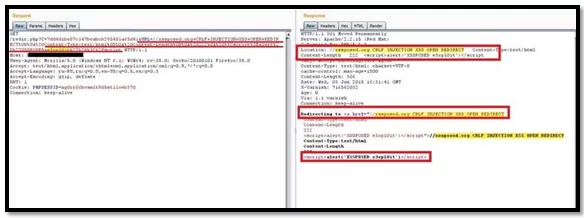
Mitigations:
Mitigation recommended for prevention of CRLF injection are as follows –
- Always sanitize and validate user supplied inputs.
- Always encode CR-LF and other special characters.
- Validate every input before they reach to response headers.
- Disable unnecessary headers.
That was it about CRLF injection in this blog. Hope this was help in understanding about the vulnerability.
Thank You.
Author,
Pralekya H.
Attack & Pentest Team
Varutra Consulting Pvt. Ltd.