Security Threat Intelligence Standards – STIX and TAXII

Introduction:
Security Threat Intelligence Standards (STIX and TAXII) make day-to-day SOC operations go uninterrupted with a shared strategy that provides a collaborative response to cybersecurity threats.
MITRE is one such organization that collaborates with industry and government institutions to develop a common approach towards cybersecurity by providing registries of baseline security data, establishing standardized languages for accurately communicating cybersecurity information, and defining proper utilization. One of MITRE’s first efforts to label security vulnerability was the Common Vulnerabilities and Exposures (CVE®). It is the standard for naming vulnerabilities that allows security devices, programs, and entities to be linked. CVE compatibility has been reached in over 100 products and services from over 75 vendors.
As we speak, MITRE is currently working on two new projects for exchanging cyber threat information: the Trusted Automated eXchange of Indicator Information (TAXIITM) and the Structured Threat Information eXpression (STIXTM), that are being funded by the United States Department of Homeland Security.
Security Threat Intelligence Standards:
TAXII is a chain of protocols that are used for safe and secure sharing of cyber-threat data for real-time observation, protection, and reducing cyber-attacks. While, STIX is a standard format for cyber-threat data, including cyber observables, indicators of compromise, incidents, and TTP (techniques, tactics, and procedures). In the areas of vulnerability management, software testing, application compliance, asset management, enterprise reporting, ransomware protection, configuration management, incident management, remediation, and threat knowledge sharing, TAXII and STIX together help communities in sharing the coordinated threat intelligence and facilitate collective defense.
STIX
MITRE and the OASIS Cyber Threat Intelligence (CTI) Technical Committee developed Structured Threat Information Expression (STIXTM), an international standard language and serialization format that has been adopted by many bits of intelligence exchange groups and organizations for exchanging cyber threat intelligence (CTI) in an order to describe the threat.
STIX 2.1 standard introduces STIX Domain Objects (SDO), which is an object-based method for organizing threat information that makes it easy to use the details required to make network security assessments. These objects are described as STIX Relationship Objects (SROs), which show how they relate to other objects, giving a clear picture of the danger. There are currently 18 STIX objects available to identify threat data, which can be grouped or linked to each other to indicate certain types of relationships to aid in the classification of threats.
- Attack Pattern: A form of TTP that describes the methods used by attackers to breach targets.
- Campaign: A collection of hostile behavior that represents a series of malicious actions against a particular range of targets over time.
- The course of Action: A suggestion by an information provider to a user regarding the steps they should take concerning that intelligence.
- Grouping: Unlike a STIX Bundle which explicitly conveys no context, this asserts that the referenced STIX Objects have a similar context.
- Identity: People, organizations, programs, or groups (e.g., ACME, Inc.) as well as divisions of individuals, organizations, structures, or groups (e.g., the finance sector).
- Indicator: This contains a pattern for detecting illegal or disruptive cyber activity.
- Infrastructure: Represents a form of TTP and defines all facilities, computing programs, and relative physical or virtual resources (e.g., C2 servers used in an attack, database servers attacked by an attack, and so on).
- Intrusion Set: A collection of adversarial activities and services with similar characteristics that are thought to be coordinated by a single organization.
- Location: A geographic location that is represented by this object.
- Malware: Malicious code that is represented by this type of TTP.
- Malware Analysis: The meta-data and its effects are collected by performing a static or dynamic analysis on any malware.
- Note: Provides descriptive text to offer additional meaning and/or analysis that is not found in the STIX Objects.
- Observed Data: Using the STIX Cyber-observable Objects, conveys knowledge about cybersecurity-related organizations such as databases, applications, and networks (SCOs).
- Opinion: An assessment of the accuracy of knowledge that is contained in a STIX Object created.
- Report: A collection of security intelligence on one or more areas, such as a summary of a threat actor, malware, or attack strategy, as well as background and related data.
- Threat Actor: Persons, organizations, or entities who are suspected of acting maliciously.
- Tool: Legitimate tools that threaten groups and are used to carry out attacks.
- Vulnerability: A flaw in software that a hacker can exploit to obtain access to sensitive information.
Two STIX Relationship Objects (SROs) are described in STIX 2:
- Relationship: A term that is used to explain how two SDOs or SCOs are connected.
- Sighting: The assumption that something in CTI has been identified (e.g., an indication, virus, weapon, threat actor, etc.).
TAXII
The Trusted Automated Sharing of Intelligence Information (TAXIITM)is a framework that provides detailed information on how data regarding cyber-threat can be shared using HTTPS via message and service exchange. It was designed to provide extensive support to STIX content.
The three principal models for TAXII include:
- Peer to Peer
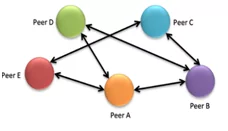
Figure 1 Peer-to-peer – multiple groups share information
Image Source: https://www.first.org/resources/papers/munich2016/wunder-stix-taxii-Overview.pdf
Peer to Peer is a sharing method in which two or more organizations communicate and exchange information directly. It can be ad hoc, where information is provided on an as-needed basis without prior coordination.
- Hub and Spoke
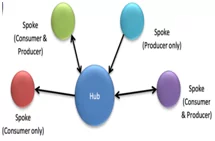
Figure 2 Hib and Spoke – one source as primary repository while others facilitate information exchange
Image Source: https://www.first.org/resources/papers/munich2016/wunder-stix-taxii-Overview.pdf
Hub and Spoke is a sharing strategy in which one organization serves as the primary repository for information, or hub, while other organizations, or spokes, facilitate information exchange. The Hub can be used to create and/or consume information by the Spokes.
- Source/Subscriber
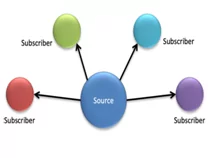
Figure 3 Source/subscriber – one single source of information
Image Source: https://www.first.org/resources/papers/munich2016/wunder-stix-taxii-Overview.pdf
A source/subscriber model can be described as one organization that serves as a single source of information and distributes it to subscribers.
To support the listed sharing models, TAXII defines two primary services:
- Collection – It is an interface for a logical registry of CTI objects that is provided by a TAXII Server. Here producer will be hosting a wide range of data, which can be requested by the TAXII Clients and Servers. The exchange of information will take place in a form of the request-response model.
- Channel – It assists the producers to push data into a large number of consumers. Then, the consumers collect data from a large number of producers via a publish-subscribe model in which TAXII Clients share information with other TAXII Clients. This whole procedure is managed by TAXII Server.
The Channel keywords are reserved in the TAXII 2.1 specification, but its resources are not defined will be defined in a later version of TAXII. Collections and Channels can be set up in a variety of ways and maybe grouped to meet the needs of a specific trust group.
For example, one or more API Roots may be supported by a TAXII server instance. API Roots are considered to be a logical category of TAXII Channels and Collections. It can be considered as instances of the TAXII API which can be accessed at various URLs, with each API Root serving as the “root” URL for that particular instance of TAXII API..
The TAXII uses existing protocols but mostly, they are found within a network that is using DNS Service logs. It also uses HTTPS for all connectivity and HTTP for content negotiation and its authentication.
The sharing of CTI represented in STIX was originally developed for TAXII but the support for exchanging STIX 2.1 content is expected to implement in the coming future for TAXII. On the other hand, TAXII can be used to exchange data in other formats. It’s notable to say that STIX and TAXII are separate standards with different architectures and serializations.
TAXII’s architecture concepts include minimizing the amount of organizational transition that is required for implementation, fast alignment with current sharing arrangements, and support for all commonly used threat sharing models, which also includes hub-and-spoke, peer-to-peer, and source-subscriber.
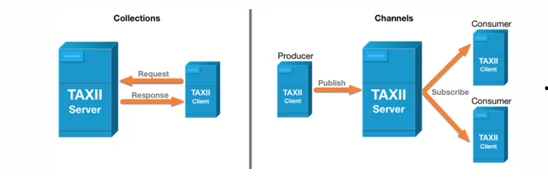
Figure 4: Primary Services
Image Source: https://www.anomali.com/resources/what-are-stix-taxii
Importance of Security Threat Intelligence Standards – STIX and TAXII:
STIX and TAXII are protocols that were created in an attempt to facilitate the detection and protection of cyber-attacks. They are machine-readable, therefore can be easily standardized, unlike prior ways of sharing. The “what” of threat intelligence is defined by STIX, while the “how” is defined by TAXII. It can be said that STIX/TAXII helps strengthen the security measures:
- Enhancement of the existing threat intelligence sharing capabilities
- Maintaining a balanced response between proactive and reactive detection
- Encouraging a comprehensive approach to threat intelligence strategy
STIX/TAXII is a transparent, community-driven initiative that offers free requirements to help in the automated expression of cyber threat information.
Use Cases of Security Threat Intelligence Standards – STIX and TAXII
Many use cases regarding cyber threat management are supported by the STIX/TAXII. Various government bodies and the Information Sharing & Analysis Centres (ISACs) have adopted them. It ranges in focus from industry to geolocation.
Sharing categorized information
Organizations can push and pull information into categories. For example, if one industry has encountered a phishing attack, then they can share this information in the phishing category which comes in the Information Sharing and Analysis Centre (ISAC). This information can directly be utilized by other organizations to enhance their defence systems.
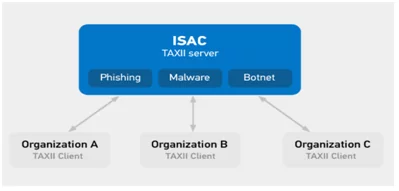
Figure 5: Use Case Scenario 1
Image Source: https://www.anomali.com/resources/what-are-stix-taxii
Sharing with Groups
Organizations that have ties with TAXII clients, can pull and push data into the TAXII servers within their trusted sharing groups. Certain groups within these ISACs may have the access to private groups and can easily get more detailed information.
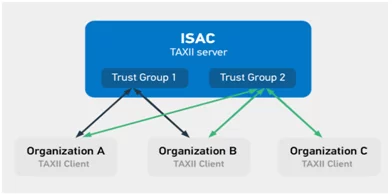
Figure 6: Use Case Scenario 2
Image Source: https://www.anomali.com/resources/what-are-stix-taxi
References:
- https://oasis-open.github.io/cti-documentation/stix/intro.html
- https://www.mitre.org/capabilities/cybersecurity/overview/cybersecurity-resources/standards
- https://www.first.org/resources/papers/munich2016/wunder-stix-taxii-Overview.pdf
Author,
Ram Mudigina
Associate Consultant
SOCGTM Team,
Varutra Consulting Pvt. Ltd.