ISO 27017- Information Security Control for Cloud Services

The use of cloud services is increasing worldwide as industries continue to grow. With this dynamic growth in cloud technology, issues of security arise. Businesses must consider the risk of protecting sensitive data and explore various available options to protect them. The primary problem while selecting cloud service providers (CSPs) is businesses’ security and privacy-related concerns. The fact that all the company’s data will be stored in an external firewall. Cyber-attacks to such cloud infrastructures can cause a domino effect and, as a result, can affect other business clients as well which can be minimized by complying Information Security Control – ISO 27017.
Definition & Importance of ISO 27017
ISO/IEC27017 is specially designed for assisting in recommending and implementing the controls for cloud-based industries. They are essential for organizations storing sensitive data in the cloud and CSPs that offer cloud-based services to other sectors. This standard was modified according to the ISO 27002 standard that permits a specific control integration as per the needs of cloud organizations.
The standard substantially covers issues like asset ownership, initiating the recovery action when CSP gets dissolved, assets disposing of that contains:
- Sensitive data.
- Compiling and storing data.
- Alignment of security management for different networks like physical and virtual, and much more.
ISO/IEC 27017 standard enables the organizations to commit for a long duration. The organizations already have an international standardized framework based on their cloud security, but integration with all the requirements can quickly reduce the operation and reputation risk. This way, organizations can seamlessly work towards their sustainable future.
Significance of ISO 27017 Standard
The ISO/IEC 27017 provides guidelines for the cyber security controls applicable for the use of cloud services. They also offer supplementary assistance for the 37 controls that are specified in ISO/IEC 27002 and 7 extra controls related to cloud computing that addresses the following parameters:
- Who will be responsible for the interaction between the CSPs and the client?
- Eradication or return of the assets after the contract has expired.
- Taking precautions of client’s virtual conditions like protection and separation.
- Configuring the Virtual Machine.
- Monitoring the activity of the client.
- Procedures and admin operations related to cloud conditions of the client.
- Alignment of the cloud network with the virtual environment.
Architecture of ISO 27017 Standard
Standard is defined as, “Information technology – Security Techniques – Code of Practice for the Information Security Controls based on ISO/IEC 27002 for cloud services”.
ISO/IEC 27017:2015 has eighteen segregations along with a long annex that covers the followings:
- Scope
- Standard references
- Abbreviations and definitions used
- Concepts specific to the cloud industry
- Policies regarding information security
- Cybersecurity organizations
- HR security
- Asset management
- Cryptography
- Access control
- Securing the communication
- Securing operations
- Environmental and physical security
- Compliance
- Relationships with supplier
- System acquisition and development, along with its maintenance
- Data security incident management
- Data security regarding business continuity management
Here is the list of some most popular cloud computing services that follow the standard:
- Amazon Web Services
- Microsoft Office 365
- Microsoft Azure
- Microsoft Intune
- Google Cloud Platform
- Nutanix Xi Cloud
- Cisco Webex
What are Cloud Service Models?
Before carrying out the cybersecurity assessment, you should know how cloud services are provided to the clients. Some of the most common cloud service models currently available in the market are:
- IaaS (Infrastructure as a Service): It only offers basic computing infrastructure like networks, physical and virtual machines, backup, and more.
- SaaS (Software as a Service): It offers final users access to software and databases like ERPs, file sharing, emails, and more.
- PaaS (Platform as a Service): It offers services like computing infrastructure, conditions suitable for software developers like databases, operating systems, execution environment for a programming language, and more.
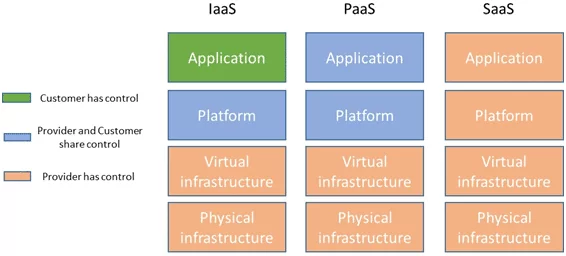
Figure 1 – Assets control by cloud service models
Benefits of ISO 27017
- Developing a long-term Strategy: By following the ISO/IEC 27012 guidelines, you can quickly minimize the prominent risk and issues related to cloud security. It makes you look reliable to your potential investors and sponsors. In addition, by mitigating the risk of cyber-attacks and data breaches, you can gain a competitive advantage.
- Maintaining Transparency: Third-party assessments help the organization by demonstrating to the stakeholders about the worldwide security practices and your ability to meet the industry set standards efficiently.
- Reduction of Reputation Risks: With the implementation of the strategy based on ISO/IEC 27017, you can analyze the vulnerabilities and quickly mitigate any risk of the data breach. If required, an external assessment can be carried out to identify the risk further and reduce them.
- Meeting Compliance: By implementing ISO/IEC 27017, you follow the national and international regulations. In addition, it helps in mitigating the risk of regulatory penalties and fines associated with various cyber-attacks and data breaches.
Conclusion
ISO 27017 is considered the most appealing standard to organizations as it offers various cloud-related services that cover all the issues that come with cloud computing. In addition, it is the perfect basic standard that protects the organization’s sensitive information and provides the framework to manage cloud security.
Author,
Rohit Sharma
Audit & Compliance Team
Varutra Consulting Pvt. Ltd.




