Thick Client Penetration Testing: Unveiling Vulnerabilities Beyond the Surface
In the rapidly evolving landscape of cybersecurity, organizations face an increasing challenge to secure their software applications and protect sensitive data. Among the arsenal of defense mechanisms, penetration testing, or “pen testing,” has emerged as a vital practice to identify and mitigate vulnerabilities. In this article, we delve into the fascinating world of thick client penetration testing, exploring its importance, methodologies, and real-world implications.
Understanding Penetration Testing
Penetration testing, often referred to as “Pentest” or “pen testing,” is a proactive approach employed by security professionals to assess the security posture of an organization’s software applications. Its primary objective is to identify vulnerabilities, analyze potential threats, and simulate real-world attacks to ensure the confidentiality, integrity, and availability of critical assets.
The Crucial Role of Penetration Testing
Statistics reveal that in 2021, a staggering 63% of organizations experienced security breaches due to application vulnerabilities. This alarming figure underscores the urgency of conducting thorough testing and assessment. Penetration testing enables organizations to identify weaknesses and address them before malicious actors exploit them, potentially resulting in data breaches, financial loss, and reputational damage.
What is Thick Client Penetration Testing?
Thick client penetration testing (TCPT) is a type of security assessment that focuses on identifying and exploiting vulnerabilities in thick client applications. Thick clients are software applications that are installed on a user’s computer and run locally. They are often used for tasks such as accessing corporate networks, managing financial data, or controlling industrial equipment.
TCPT is a complex and challenging type of penetration testing. This is because thick clients often use proprietary protocols and technologies, making them difficult to analyze. Additionally, TCPT often requires a deep understanding of the application’s functionality and behavior in order to identify potential vulnerabilities.
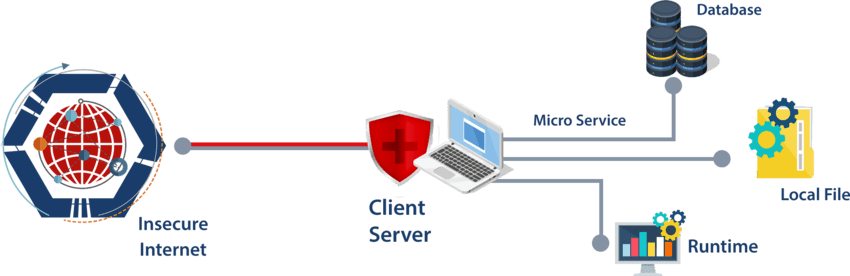
Thick Client Application Security Testing (qrcsolutionz.com)
Why is Thick Client Penetration Testing Important?
Thick clients are often used to access sensitive data and systems. As a result, they can be a valuable target for attackers. In recent years, there have been a number of high-profile attacks against thick clients, resulting in the theft of sensitive data and the disruption of critical business operations.
TCPT can help organizations to identify and mitigate vulnerabilities in their thick client applications. This can help to protect sensitive data and systems from attack.
The Unique Challenges of Thick Client Penetration Testing
Thick clients present distinctive security challenges compared to web-based applications, as they interact directly with users’ operating systems and local resources. Conducting thorough penetration testing on thick client applications requires expertise in various domains, including reverse engineering, protocol analysis, and secure code review.
How is Thick Client Penetration Testing Conducted?
TCPT typically follows a five-step process:
Information gathering:
The pentester gathers information about the target application, such as its version, the operating system it runs on, and the technologies it uses.
Vulnerability identification:
The tester uses a variety of tools and techniques to identify potential vulnerabilities in the target application.
Vulnerability exploitation:
The security tester attempts to exploit the identified vulnerabilities to gain unauthorized access to the target application.
Vulnerability remediation:
The pentester works with the application owner to remediate the identified vulnerabilities.
Reporting:
The testing professional produces a report that summarizes the findings of the TCPT engagement.
Types of Thick Client Penetration Testing
Thick client penetration testing encompasses various approaches tailored to different aspects of application security. These include:
Source code analysis:
This involves examining the source code of a thick client application to identify vulnerabilities, coding errors, or potential security weaknesses. It helps security professionals understand the logic and structure of the application and discover any flaws that could be exploited.
Binary analysis:
Binary analysis focuses on analyzing the compiled executable file of a thick client application. It involves examining the binary code, understanding its functionality, and identifying any security vulnerabilities or malicious behavior. This analysis is crucial for uncovering hidden threats and understanding how the application operates at a lower level.
Reverse engineering:
Reverse engineering involves the process of deconstructing a thick client application to understand its inner workings and extract valuable information. Security professionals use reverse engineering techniques to analyze the application’s algorithms, protocols, and data structures. It helps identify vulnerabilities and provides insights into potential attack vectors.
Protocol analysis:
Protocol analysis involves analyzing the communication protocols used by the thick client application. Security experts examine network traffic, dissect the protocols, and identify potential security vulnerabilities or weaknesses. This analysis helps in understanding how the application communicates with servers or other components and uncovering any weaknesses that can be exploited.
Runtime analysis:
Runtime analysis involves monitoring the execution of a thick client application in real-time. Security professionals use various tools and techniques to observe the application’s behavior, track system calls, monitor memory usage, and detect any abnormal activities or security-related events. Runtime analysis helps identify runtime vulnerabilities, memory corruption issues, or unexpected behavior that could be exploited by attackers.Each method focuses on different aspects of the thick client application to uncover vulnerabilities and weaknesses in its design, implementation, or configuration.
Input Validation and Boundary Testing:
Rigorous input validation and boundary testing are crucial to ensure thick client applications can handle unexpected user inputs securely. By fuzzing input fields, attempting buffer overflow attacks, and testing for injection vulnerabilities, testers can uncover potential weaknesses and fortify application defenses.
Tools Used for Thick Client Penetration Testing
A wide range of specialized tools is available to assist in conducting thorough thick client penetration testing. These tools aid in tasks such as reverse engineering, code analysis, protocol analysis, traffic interception, and vulnerability scanning.
• IDA Pro
• OllyDbg
• Wireshark
• Burp Suite
• Metasploit
Utilizing the right combination of tools helps penetration testers efficiently assess the security of thick client applications.
Best Practices for Thick Client Penetration Testing
To ensure the success and effectiveness of thick client penetration testing, several best practices should be followed.
a.Thorough Planning and Scoping:
Before conducting thick client penetration testing, it is essential to plan and define the scope of the engagement. This involves understanding the objectives, identifying the target application, determining the testing approach, and establishing the boundaries of the assessment. Thorough planning ensures that the testing activities are focused and aligned with the organization’s goals.
b.Obtaining Proper Authorization:
Penetration testing should never be performed without proper authorization from the application owner. Obtaining explicit permission ensures legal and ethical compliance. It is crucial to have a formal agreement in place that outlines the scope, duration, and limitations of the testing engagement. This authorization process protects both the tester and the organization from any potential legal consequences.
c.Maintaining Clear Communication with the Application Owner:
Effective communication with the application owner throughout the testing process is vital. It helps establish a clear understanding of expectations, provides updates on the progress and findings, and allows for timely resolution of any issues or concerns. Collaboration and open dialogue between the penetration tester and the application owner contribute to a successful engagement.
d. Documenting Findings and Recommendations:
Thorough documentation of findings is crucial in thick client penetration testing. It involves capturing details about identified vulnerabilities, their impact, and the steps taken to exploit them. Additionally, recommendations for remediation should be provided, including specific guidance on how to mitigate the identified vulnerabilities. Documentation serves as a valuable resource for the application owner to understand and address the security weaknesses.
e. Adhering to Ethical Guidelines:
Ethics play a fundamental role in thick client penetration testing. Testers must abide by ethical guidelines and professional standards throughout the engagement. This includes respecting privacy, ensuring confidentiality of sensitive information, and obtaining necessary permissions. Adhering to ethical principles helps maintain trust, credibility, and professionalism in the field of cybersecurity.
g. Keeping abreast of cutting-edge methodologies, technologies, and attack vectors:
The landscape of cybersecurity is constantly evolving, with new techniques, technologies, and attack vectors emerging regularly. Penetration testers must stay updated with these advancements to effectively assess the security of thick client applications. This involves continuous learning, researching, and staying informed about the latest trends, vulnerabilities, and countermeasures in the industry.
h. Regular Training, Knowledge Sharing, and Collaboration:
To enhance skills and ensure the adoption of industry best practices, regular training, knowledge sharing, and collaboration with the security community are essential. Attending relevant training programs, conferences, and workshops helps expand expertise. Sharing knowledge and experiences with peers through forums, online communities, and professional networks fosters a culture of continuous improvement and contributes to the overall success of thick client penetration testing.
The Benefits of Thick Client Penetration Testing
Thick client penetration testing offers numerous benefits for organizations:
Improved Security:
By identifying and mitigating vulnerabilities, thick client penetration testing helps improve the security posture of applications, reducing the risk of data breaches and unauthorized access.
Compliance:
Many regulatory frameworks, such as the Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA), require organizations to conduct regular penetration testing. By performing thorough thick client penetration testing, organizations can ensure compliance with these standards.
Risk Reduction:
Thick client penetration testing enables organizations to proactively identify and address vulnerabilities, reducing the risk of security incidents, financial loss, and reputational damage.
Real-World Implications and Success Stories
Let’s examine a couple of real-world examples that highlight the importance of thick client penetration testing:
Case Study 1: Banking Application Vulnerabilities:
A renowned banking application underwent a thorough thick client penetration test, revealing vulnerabilities in the application’s authentication mechanism. By exploiting these vulnerabilities, the tester gained unauthorized access to sensitive customer data, emphasizing the urgent need to address such flaws.
Case Study 2: Gaming Industry Breach:
In a high-profile gaming industry breach, thick client penetration testing exposed vulnerabilities in the game’s update mechanism, allowing hackers to inject malicious code into users’ machines. The consequences were devastating, with compromised user accounts, stolen personal information, and disrupted gaming experiences.
Conclusion
Thick client penetration testing plays a pivotal role in identifying and mitigating vulnerabilities within applications running on users’ local machines. By conducting thorough TCPT engagements, organizations can strengthen their security posture, protect sensitive data, meet compliance requirements, and ultimately safeguard their valuable assets from malicious actors.
Research , References & Resources :
https://medium.com/@david.valles/security-testing-of-thick-client-application-15612f326cac
https://securitywarrior9.blogspot.com/2017/08/intro-to-thick-client-penetration.html
https://www.netspi.com/resources/ebooks/4-types-of-thick-client-application-penetration-testing-vulnerabilities/
https://allabouttesting.org/thick-client-security-testing-short-tutorial/
https://infosecwriteups.com/thick-client-pentest-modern-approaches-and-techniques-part-1-7bb0f5f28e8e
https://www.geeksforgeeks.org/difference-between-thin-clients-and-thick-clients/
https://www.cyberark.com/resources/threat-research-blog/thick-client-penetration-testing-methodology
https://www.hackingarticles.in/thick-client-pentest-lab-setup-dvta-2/
https://www.hackingarticles.in/thick-client-penetration-testing-traffic-analysis/




