AWS Pentesting – Part – 1

Nowadays, we have experienced many data breaches exposing different vulnerabilities like s3 buckets, compromised AWS cloud environments, and many more so avoid this it is important to perform AWS Pentesting.
To understand the attacks on AWS, one must be aware of the different services provided by AWS.
In this blog, we will understand the different services provided by AWS, data breaches on AWS cloud services, tools used for Pentesting the AWS services, and how to start with the AWS CLI.

AWS offers many services. Like EC2, S3, AWS Lambda, CloudTrail, CloudWatch, and many more….
Many of the data breaches happen because of the misconfiguration of AWS services.
In this series of blog posts, we will discuss how these services can be exploited if it is not configured properly and countermeasures of course.
Let’s have a look at S3 Bucket Basic Services.
- S3

Source: https://blog.lawrencemcdaniel.com/integrating-aws-s3-cloudfront-with-wordpress-2/
Now the question is what is S3?
S3 stands for Simple Storage Service
- Highly scalable storage services with virtually unlimited capacity.
- The main element of the service is a bucket which acts as a container. Contents which are stored in the bucket are called objects like file, backup, documents, images, sensitive file, source code, static web site, etc.
- Using amazon s3, you can store and retrieve any amount of data at any time on the web.
- A different mechanism of access control for s3 buckets
- ACLs
- Bucket policies
- IAM policies
- S3 buckets can be accessed via HTTP interface and AWS CLI
- http://s3.amazonaws.com/bucket_name
- http://bucket_name.s3.amazonaws.com
Refer to the link to understand S3 in detail. https://aws.amazon.com/s3/
- EC2

Source: https://medium.com/awesome-cloud/aws-amazon-ec2-instance-purchasing-options-d57f9b20dfa7
- EC2 is nothing but Elastic Cloud Compute
- Most widely used service that provides a secure and resizable compute capacity in the cloud
- It can be used to launch as many virtual servers you need on a pay-as-you-go basis.
Refer to this link to understand EC2 in detail https://aws.amazon.com/ec2/
- IAM

Source: https://medium.com/@niharmishra511/aws-iam-7b48e997ecb9
- To control privileges
- Is a web service used in combination with all Amazon Services?
Refer to this link to understand IAM in detail. https://aws.amazon.com/iam/
- AWS Lambda

Source: https://blog.iron.io/aws-lambda-reviews/
- FaaS(Function as a Service)
- Offers serverless functions and applications.
- Code runs in response to events
Refer to this link to understand AWS Lambda in detail. https://aws.amazon.com/lambda/
Now the question is why there is a need for pentesting?
As more and more organizations moving towards the cloud, a data breach is increasing day by day, and to protect this data breach Pentesting requirement has become necessary. Let us discuss about the data breach on the cloud in brief.
A data breach on Cloud
According to Gartner, Gartner analyst Neil MacDonald says that 99 percent of cloud security failures will be the customer’s fault through 2025.
- Capital One

- Year: 2019
- Attacker: AWS Employee
- Data leaked: 80,000 bank account numbers leaked
- How: SSRF
- Cause: misconfiguration of IAM role permissions for EC2 instance
- Accenture

- Year: 2017
- Attacker: Unsecured amazon s3 buckets was discovered by one of the UpGuard Security Researcher
- Data leaked: SecretAPI data, authentication credentials, decryption keys, and customer data
There are many data breaches that happened in the past like the GoDaddy data breach due to s3 cloud bucket misconfiguration, Verizon due to S3 leak, AgentRun leaks customer health information, and many more.
These data breaches can be minimized by performing pen-testing, security audits on different AWS cloud services.
Now the question is what are the tools required to start for pentesting AWS cloud?
Tools

- AWS-inventory
Python script to discover all AWS resources created in an account.
Source:https://github.com/nccgroup/aws-inventory
- Pmapper
Principal Mapper (PMapper) is a script and library for identifying risks in the configuration of AWS Identity and Access Management (IAM) in an AWS account.
Source: https://github.com/nccgroup/PMapper
- Bucket_finder
Ruby script to perform brute force attack on s3 bucket
Source: https://github.com/FishermansEnemy/bucket_finder
- Prowler
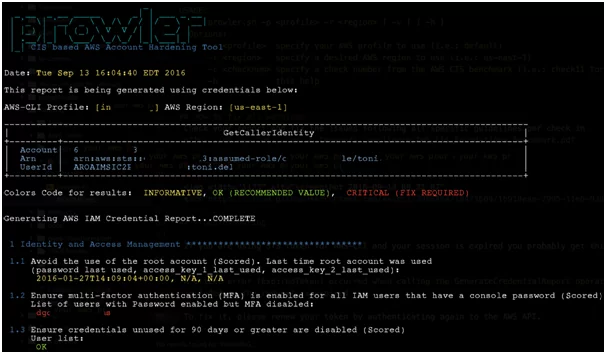
Prawler is a CLI tool for AWS Security Best Practices, auditing, hardening as per CIS AMAZON Web Services Foundations Benchmark.
Source: https://github.com/toniblyx/prowler
- Nimbostratus
Tools for fingerprinting and exploiting Amazon cloud infrastructures.
Source: https://github.com/andresriancho/nimbostratus
Find out the link for more toolsàhttps://github.com/toniblyx/my-arsenal-of-aws-security-tools
Now it’s time to set up AWS CLI in kali linux.
Steps:
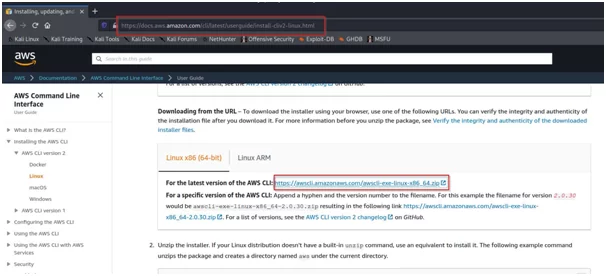
- Go to the link https://docs.aws.amazon.com/cli/latest/userguide/install-cliv2-linux.html in the browser. Click on the link as shown in the below image.

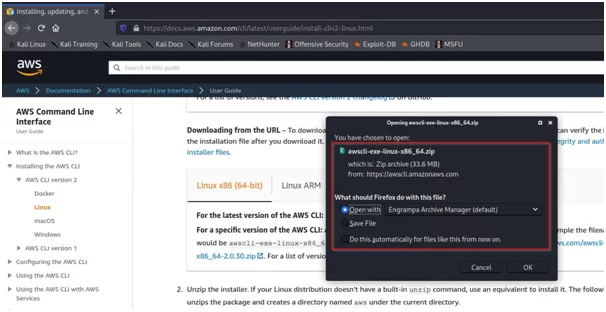
- Save the zip file to a location in your system and rename the folder to awscliv2.zip

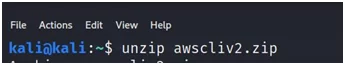
- Unzip the AWS cli

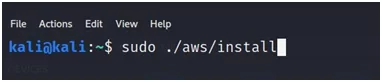
- Install the AWS cli

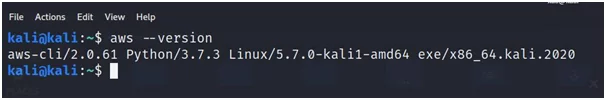
- Verify AWS cli is installed or not by using a command AWS –version

- The next step is to configure your AWS account.
Enter access keys and secret keys of your AWS account with AWS CLI.
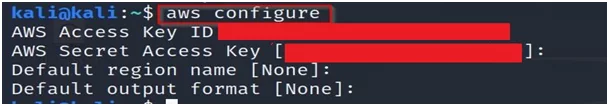
That’s it for now. In the next blog, we will learn about the s3 bucket exploitation part.
Till then bye-bye!
Reference:
https://blog.eccouncil.org/all-you-need-to-know-about-pentesting-in-the-aws-cloud/
https://www.lacework.com/top-cloud-breaches-2019/
https://securityaffairs.co/wordpress/64150/data-breach/accenture-data-leak.html
https://www.slideshare.net/ObikaGellineau/capital-one-data-breach
Author,
Bhamini Shah
Attack & Pentest Team
Varutra Consulting Pvt. Ltd.